GitBook: [#2815] update padding oracle
This commit is contained in:
parent
0008fa51c7
commit
0455778d02
BIN
.gitbook/assets/image (629) (1).png
Normal file
BIN
.gitbook/assets/image (629) (1).png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 204 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 204 KiB After Width: | Height: | Size: 24 KiB |
@ -1,6 +1,6 @@
|
||||
# GCP Security
|
||||
|
||||
.png>)
|
||||
 (1).png>)
|
||||
|
||||
## Security concepts <a href="security-concepts" id="security-concepts"></a>
|
||||
|
||||
|
||||
@ -4,11 +4,11 @@
|
||||
|
||||
In CBC mode the **previous encrypted block is used as IV** to XOR with the next block:
|
||||
|
||||
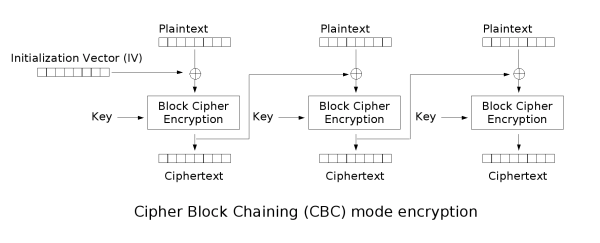
|
||||

|
||||
|
||||
To decrypt CBC the **opposite** **operations** are done:
|
||||
|
||||
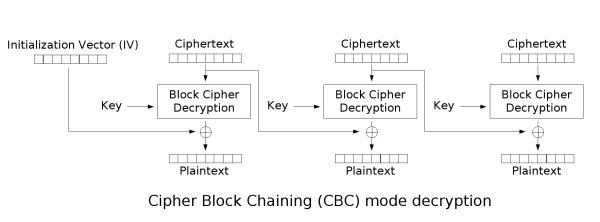
|
||||

|
||||
|
||||
Notice how it's needed to use an **encryption** **key** and an **IV**.
|
||||
|
||||
@ -30,27 +30,27 @@ Note how in the last example the **last block was full so another one was genera
|
||||
|
||||
## Padding Oracle
|
||||
|
||||
When an application decrypts encrypted data, it will first decrypt the data; then it will remove the padding. During the cleanup of the padding, **if **an **invalid** **padding **triggers a detectable **behaviour**, you have a **padding oracle vulnerability**. The detectable behaviour can be an **error**, a **lack **of **results**, or a **slower response**.
|
||||
When an application decrypts encrypted data, it will first decrypt the data; then it will remove the padding. During the cleanup of the padding, if an **invalid padding triggers a detectable behaviour**, you have a **padding oracle vulnerability**. The detectable behaviour can be an **error**, a **lack of results**, or a **slower response**.
|
||||
|
||||
If you detect this behaviour, you can** decrypt the encrypted data** and even** encrypt any cleartext**.
|
||||
If you detect this behaviour, you can **decrypt the encrypted data** and even **encrypt any cleartext**.
|
||||
|
||||
### How to exploit
|
||||
|
||||
You could use [https://github.com/AonCyberLabs/PadBuster](https://github.com/AonCyberLabs/PadBuster) to exploit this kind of vulnerability or just do
|
||||
You could use [https://github.com/AonCyberLabs/PadBuster](https://github.com/AonCyberLabs/PadBuster) to exploit this kind of vulnerability or just do
|
||||
|
||||
```
|
||||
sudo apt-get install padbuster
|
||||
```
|
||||
|
||||
In order to test if the cookie of a site is vulnerable you could try:
|
||||
In order to test if the cookie of a site is vulnerable you could try:
|
||||
|
||||
```bash
|
||||
perl ./padBuster.pl http://10.10.10.10/index.php "RVJDQrwUdTRWJUVUeBKkEA==" 8 -encoding 0 -cookies "login=RVJDQrwUdTRWJUVUeBKkEA=="
|
||||
```
|
||||
|
||||
**Encoding 0** means that **base64 **is used (but others are available, check the help menu).
|
||||
**Encoding 0** means that **base64** is used (but others are available, check the help menu).
|
||||
|
||||
You could also **abuse **this **vulnerability **to **encrypt new data**. For example, imagine that the content of the cookie is "_user=MyUsername_", then you may change it to "_**user=administrator**_" and escalate privileges inside the application. You could also do it using `paduster`specifying the** -plaintext** parameter:
|
||||
You could also **abuse this vulnerability to encrypt new data. For example, imagine that the content of the cookie is "**_**user=MyUsername**_**", then you may change it to "\_user=administrator\_" and escalate privileges inside the application. You could also do it using `paduster`specifying the -plaintext** parameter:
|
||||
|
||||
```bash
|
||||
perl ./padBuster.pl http://10.10.10.10/index.php "RVJDQrwUdTRWJUVUeBKkEA==" 8 -encoding 0 -cookies "login=RVJDQrwUdTRWJUVUeBKkEA==" -plaintext "user=administrator"
|
||||
@ -64,23 +64,21 @@ perl ./padBuster.pl http://10.10.10.10/index.php "" 8 -encoding 0 -cookies "hcon
|
||||
|
||||
### The theory
|
||||
|
||||
In **summary**, you can start decrypting the encrypted data by **guessing **the correct **values **that can be used to **create **all the **different paddings**. Then, the padding oracle attack will start **decrypting **bytes **from **the **end **to the start by **guessing **which will be the correct **value **that **creates a padding of 1, 2, 3, etc**.
|
||||
In **summary**, you can start decrypting the encrypted data by guessing the correct values that can be used to create all the **different paddings**. Then, the padding oracle attack will start decrypting bytes from the end to the start by guessing which will be the correct value that **creates a padding of 1, 2, 3, etc**.
|
||||
|
||||
|
||||
|
||||
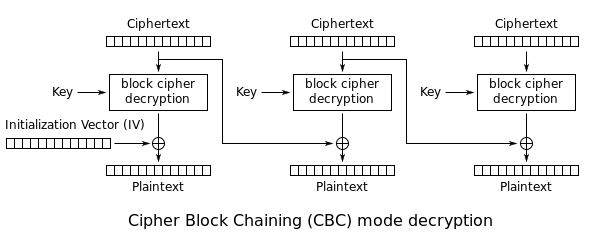
|
||||
.png>)
|
||||
|
||||
Imagine you have some encrypted text that occupies **2 blocks** formed by the bytes from **E0 to E15**.\
|
||||
In order to **decrypt** the **last** **block** (**E8** to **E15**), the whole block passes through the "block cipher decryption" generating the** intermediary bytes I0 to I15**.\
|
||||
In order to **decrypt** the **last** **block** (**E8** to **E15**), the whole block passes through the "block cipher decryption" generating the **intermediary bytes I0 to I15**.\
|
||||
Finally, each intermediary byte is **XORed** with the previous encrypted bytes (E0 to E7). So:
|
||||
|
||||
* `C15 = D(E15) ^ E7 = I15 ^ E7`
|
||||
* `C14 = I14 ^ E6`
|
||||
* `C13 = I13 ^ E5 `
|
||||
* `C12 = I12 ^ E4 `
|
||||
* `C13 = I13 ^ E5`
|
||||
* `C12 = I12 ^ E4`
|
||||
* ...
|
||||
|
||||
Now, It's possible to **modify `E7` until `C15` is `0x01`**, which will also be a correct padding. So, in this case: `\x01 = I15 ^ E'7`
|
||||
Now, It's possible to **modify `E7` until `C15` is `0x01`**, which will also be a correct padding. So, in this case: `\x01 = I15 ^ E'7`
|
||||
|
||||
So, finding E'7, it's **possible to calculate I15**: `I15 = 0x01 ^ E'7`
|
||||
|
||||
@ -103,4 +101,4 @@ But if you BF the padding (using padbuster for example) you manage to get anothe
|
||||
|
||||
## References
|
||||
|
||||
* [https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation](https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation)
|
||||
* [https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation](https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation)
|
||||
|
||||
Loading…
Reference in New Issue
Block a user