| .. | ||
| drozer-tutorial | ||
| frida-tutorial | ||
| adb-commands.md | ||
| android-applications-basics.md | ||
| android-burp-suite-settings.md | ||
| android-task-hijacking.md | ||
| apk-decompilers.md | ||
| avd-android-virtual-device.md | ||
| content-protocol.md | ||
| exploiting-a-debuggeable-applciation.md | ||
| google-ctf-2018-shall-we-play-a-game.md | ||
| inspeckage-tutorial.md | ||
| intent-injection.md | ||
| make-apk-accept-ca-certificate.md | ||
| manual-deobfuscation.md | ||
| react-native-application.md | ||
| README.md | ||
| reversing-native-libraries.md | ||
| smali-changes.md | ||
| spoofing-your-location-in-play-store.md | ||
| webview-attacks.md | ||
Android Applications Pentesting
Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %} {% endhint %}
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.
Android Applications Basics
It's highly recommended to start reading this page to know about the most important parts related to Android security and the most dangerous components in an Android application:
{% content-ref url="android-applications-basics.md" %} android-applications-basics.md {% endcontent-ref %}
ADB (Android Debug Bridge)
This is the main tool you need to connect to an android device (emulated or physical).
It allows you to control your device over USB or Network from a computer, copy files back and forth, install and uninstall apps, run shell commands, perform backups, read logs and more.
Take a look to the following list of ADB Commands _**_to learn how to use adb.
Smali
Sometimes it is interesting to modify the application code to access hidden information (maybe well obfuscated passwords or flags). Then, it could be interesting to decompile the apk, modify the code and recompile it.
In this tutorial you can learn how to decompile and APK, modify Smali code and recompile the APK with the new functionality. This could be very useful as an alternative for several tests during the dynamic analysis that are going to presented. Then, keep always in mid this possibility.
Other interesting tricks
- Spoofing your location in Play Store
- Download APKs: https://apps.evozi.com/apk-downloader/, https://apkpure.com/es/, https://www.apkmirror.com/, https://apkcombo.com/es-es/apk-downloader/
- Extract APK from device:
adb shell pm list packages
com.android.insecurebankv2
adb shell pm path com.android.insecurebankv2
package:/data/app/com.android.insecurebankv2-Jnf8pNgwy3QA_U5f-n_4jQ==/base.apk
adb pull /data/app/com.android.insecurebankv2- Jnf8pNgwy3QA_U5f-n_4jQ==/base.apk
Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %} {% endhint %}
Static Analysis
First of all, for analysing an APK you should take a look to the to the Java code using a decompiler.
Please, read here to find information about different available decompilers.
Looking for interesting Info
Just taking a look to the strings of the APK you can search for passwords, URLs (https://github.com/ndelphit/apkurlgrep), api keys, encryption, bluetooth uuids, tokens and anything interesting... look even for code execution backdoors or authentication backdoors (hardcoded admin credentials to the app).
Firebase
Pay special attention to firebase URLs and check if it is bad configured. More information about whats is FIrebase and how to exploit it here.
Basic understanding of the application - Manifest.xml, strings.xml
Using any of the decompilers mentioned here you will be able to read the Manifest.xml. You could also rename the apk file extension to .zip and unzip it.
Reading the manifest you can find vulnerabilities:
- First of all, check if the application is debuggeable. A production APK shouldn't be (or others will be able to connect to it). You can check if an application is debbugeable looking in the manifest for the attribute
debuggable="true"inside the tag <application Example:<application theme="@2131296387" debuggable="true"- Learn here how to find debuggeable applications in a phone and exploit them
- Backup: The
android:allowBackupattribute defines whether application data can be backed up and restored by a user who has enabled usb debugging. If backup flag is set to true, it allows an attacker to take the backup of the application data via adb even if the device is not rooted. Therefore applications that handle and store sensitive information such as card details, passwords etc. should have this setting explicitly set to false because by default it is set to true to prevent such risks.<application android:allowBackup="false"
- NetworkSecurity: The application network security can be overwritten the defaults values with
android:networkSecurityConfig="@xml/network_security_config". A file with that name may be put in res/xml. This file will configure important security settings like certificate pins or if it allows HTTP traffic. You can read here more information about all the things that can be configure, but check this example about how to configure HTTP traffic for some domains:<domain-config cleartextTrafficPermitted="true"> <domain includeSubdomains="true">formation-software.co.uk </domain></domain-config>
- Exported activities: Check for exported activities inside the manifest as this could be dangerous. Later in the dynamic analysis it will be explained how you can abuse this behaviour.
- Content Providers: If an exported provider is being exposed, you could b able to access/modify interesting information. In dynamic analysis you will learn how to abuse them.
- Check for FileProviders configurations inside the attribute
android:name="android.support.FILE_PROVIDER_PATHS". Read here to learn more about FileProviders.
- Check for FileProviders configurations inside the attribute
- Exposed Services: Depending on what the service is doing internally vulnerabilities could be exploited. In dynamic analysis you will learn how to abuse them.
- Broadcast Receivers: You will learn how you can possibly exploit them during the dynamic analysis.
- URL scheme: Read the code of the activity managing the schema and look for vulnerabilities managing the input of the user. More info about what is an URL scheme here.
- minSdkVersion, targetSDKVersion, maxSdkVersion: They indicate the versions of Android the app will run on. It's important to keep them in mind because from a security perspective, supporting old version will allow known vulnerable versions of android to run it.
Reading resources.arsc/strings.xml you can find some interesting info:
- API Keys
- Custom schemas
- Other interesting info developers save in this file
Tapjacking
Tapjacking is an attack where a malicious application is launched and positions itself on top of a victim application. Once it visibly obscures the victim app, its user interface is designed in such a way as to trick the user to interact with it, while it is passing the interaction along to the victim app.
In effect, it is blinding the user from knowing they are actually performing actions on the victim app.
In order to detect apps vulnerable to this attacked you should search for exported activities in the android manifest (note that an activity with an intent-filter is automatically exported by default). Once you have found the exported activities, check if they require any permission. This is because the malicious application will need that permission also.
Finally, it's important to check the code for possible setFilterTouchesWhenObscured configurations. If set to true, a button can be automatically disabled if it is obscured:
<Button android:text="Button"
android:id="@+id/button1"
android:layout_width="wrap_content"
android:layout_height="wrap_content"
android:filterTouchesWhenObscured=** "true"**>
</Button>
You can use qark with the --exploit-apk parameter to create a malicious application to test for possible Tapjacking vulnerabilities.
A example project implementing this kind of feature can be fund in FloatingWindowApp.
The mitigation is relatively simple as the developer may choose not to receive touch events when a view is covered by another. Using the Android Developer’s Reference:
Sometimes it is essential that an application be able to verify that an action is being performed with the full knowledge and consent of the user, such as granting a permission request, making a purchase or clicking on an advertisement. Unfortunately, a malicious application could try to spoof the user into performing these actions, unaware, by concealing the intended purpose of the view. As a remedy, the framework offers a touch filtering mechanism that can be used to improve the security of views that provide access to sensitive functionality.
To enable touch filtering, call
setFilterTouchesWhenObscured(boolean)or set the android:filterTouchesWhenObscured layout attribute to true. When enabled, the framework will discard touches that are received whenever the view's window is obscured by another visible window. As a result, the view will not receive touches whenever a toast, dialog or other window appears above the view's window.
Task Hijacking
{% content-ref url="android-task-hijacking.md" %} android-task-hijacking.md {% endcontent-ref %}
Insecure data storage
Internal Storage
Files created on internal storage are accessible only by the app. This protection is implemented by Android and is sufficient for most applications. But developers often use MODE_WORLD_READBALE & MODE_WORLD_WRITABLE to give access to those files to a different application, but this doesn’t limit other apps(malicious) from accessing them.
During the static analysis check for the use of those modes, during the dynamic analysis check the permissions of the files created (maybe some of them are worldwide readable/writable).
More information about this vulnerability and how to fix it here.
External Storage
Files created on external storage, such as SD Cards, are globally readable and writable. Because external storage can be removed by the user and also modified by any application, you should not store sensitive information using external storage.
As with data from any untrusted source, you should perform input validation when handling data from external storage. We strongly recommend that you not store executables or class files on external storage prior to dynamic loading. If your app does retrieve executable files from external storage, the files should be signed and cryptographically verified prior to dynamic loading.
Info taken from here.
External storage can be accessed in /storage/emulated/0 , /sdcard , /mnt/sdcard
{% hint style="info" %} Starting with Android 4.4 (API 17), the SD card has a directory structure which limits access from an app to the directory which is specifically for that app. This prevents malicious application from gaining read or write access to another app's files. {% endhint %}
Sensitive data stored in clear-text
- Shared preferences: Android allow to each application to easily save xml files in the path
/data/data/<packagename>/shared_prefs/and sometimes it's possible to find sensitive information in clear-text in that folder. - Databases: Android allow to each application to easily save sqlite databases in the path
/data/data/<packagename>/databases/and sometimes it's possible to find sensitive information in clear-text in that folder.
Broken TLS
Accept All Certificates
For some reason sometimes developers accept all the certificates even if for example the hostname does not match with lines of code like the following one:
SSLSocketFactory sf = new cc(trustStore);
sf.setHostnameVerifier(SSLSocketFactory.ALLOW_ALL_HOSTNAME_VERIFIER);
A good way to test this is to try to capture the traffic using some proxy like Burp without authorising Burp CA inside the device. Also, you can generate with Burp a certificate for a different hostname and use it.
Broken Cryptography
Poor Key Management Processes
Some developers save sensitive data in the local storage and encrypt it with a key hardcoded/predictable in the code. This shouldn't be done as some reversing could allow attackers to extract the confidential information.
Use of Insecure and/or Deprecated Algorithms
Developers shouldn't use deprecated algorithms to perform authorisation checks, store or send data. Some of these algorithms are: RC4, MD4, MD5, SHA1... If hashes are used to store passwords for example, hashes brute-force resistant should be used with salt.
Other checks
- It's recommended to obfuscate the APK to difficult the reverse engineer labour to attackers.
- If the app is sensitive (like bank apps), it should perform it's own checks to see if the mobile is rooted and act in consequence.
- If the app is sensitive (like bank apps), it should check if an emulator is being used.
- If the app is sensitive (like bank apps), it should check it's own integrity before executing it to check if it was modified.
- Use APKiD to check which compiler/packer/obfuscator was used to build the APK
React Native Application
Read the following page to learn how to easily access javascript code of React applications:
{% content-ref url="react-native-application.md" %} react-native-application.md {% endcontent-ref %}
Xamarin Applications
Xamarin apps are written in C#, in order to access the C# code decompressed, you need to get the files from the apk:
7z r app.apk #Or any other zip decompression cmd
Then, decompress all the DLsL using xamarin-decompress:
python3 xamarin-decompress.py -o /path/to/decompressed/apk
and finally you can use these recommended tools to read C# code from the DLLs.
Automated Static Code Analysis
The tool mariana-trench is capable of finding vulnerabilities by scanning the code of the application. This tool contains a series of known sources (that indicates to the tool the places where the input is controlled by the user), sinks (which indicates to the tool dangerous places where malicious user input could cause damages) and rules. These rules indicates the combination of sources-sinks that indicates a vulnerability.
With this knowledge, mariana-trench will review the code and find possible vulnerabilities on it.
Secrets leaked
An application may contain secrets (API keys, passwords, hidden urls, subdomains...) inside of it that you might be able to discover. You could us a tool such as https://github.com/dwisiswant0/apkleaks
Other interesting functions
- Code execution:
Runtime.exec(), ProcessBuilder(), native code:system() - Send SMSs:
sendTextMessage, sendMultipartTestMessage - Native functions declared as
native:public native, System.loadLibrary, System.load
Other tricks
{% content-ref url="content-protocol.md" %} content-protocol.md {% endcontent-ref %}
Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %} {% endhint %}
Dynamic Analysis
First of all, you need an environment where you can install the application and all the environment (Burp CA cert, Drozer and Frida mainly). Therefore, a rooted device (emulated or not) is extremely recommended.
Online Dynamic analysis
You can create a free account in: https://appetize.io/. This platform allows you to upload and execute APKs, so it is useful to see how an apk is behaving.
You can even see the logs of your application in the web and connect through adb.
Thanks to the ADB connection you can use Drozer and Frida inside the emulators.
Local Dynamic Analysis
You can use some emulator like:
- Android Studio (You can create x86 and arm devices, and according to this latest x86 versions support ARM libraries without needing an slow arm emulator).
- If you want to try to install an image and then you want to delete it you can do that on Windows:
C:\Users\<User>\AppData\Local\Android\sdk\system-images\or Mac:/Users/myeongsic/Library/Android/sdk/system-image - This is the main emulator I recommend to use and you can learn to set it up in this page.
- If you want to try to install an image and then you want to delete it you can do that on Windows:
- Genymotion (Free version: Personal Edition, you need to create an account. It's recommend to download the version WITH VirtualBox to avoid potential errors.)
- Nox (Free, but it doesn't support Frida or Drozer).
{% hint style="info" %} When creating a new emulator on any platform remember that the bigger the screen is, the slower the emulator will run. So select small screens if possible. {% endhint %}
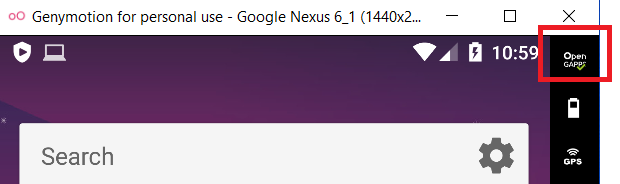
As most people will use Genymotion, note this trick. To install google services (like AppStore) you need to click on the red marked button of the following image:
Also, notice that in the configuration of the Android VM in Genymotion you can select Bridge Network mode (this will be useful if you will be connecting to the Android VM from a different VM with the tools).
Or you could use a physical device (you need to activate the debugging options and it will be cool if you can root it):
- Settings.
- (FromAndroid 8.0) Select System.
- Select About phone.
- Press Build number 7 times.
- Go back and you will find the Developer options.
Once you have installed the application, the first thing you should do is to try it and investigate what does it do, how does it work and get comfortable with it.
I will suggest to perform this initial dynamic analysis using MobSF dynamic analysis + pidcat, so will will be able to learn how the application works while MobSF capture a lot of interesting data you can review later on.
Unintended Data Leakage
Logging
Often Developers leave debugging information publicly. So any application with READ_LOGS permission can access those logs and can gain sensitive information through that.
While navigating through the application use pidcat(Recommended, it's easier to use and read) or adb logcat to read the created logs and look for sensitive information.
{% hint style="warning" %}
Note that from later versions that Android 4.0, applications are only able to access their own logs. So applications cannot access other apps logs.
Anyway, it's still recommended to not log sensitive information.
{% endhint %}
Copy/Paste Buffer Caching
Android provides clipboard-based framework to provide copy-paste function in android applications. But this creates serious issue when some other application can access the clipboard which contain some sensitive data. Copy/Paste function should be disabled for sensitive part of the application. For example, disable copying credit card details.
Crash Logs
If an application crashes during runtime and it saves logs somewhere then those logs can be of help to an attacker especially in cases when android application cannot be reverse engineered. Then, avoid creating logs when applications crashes and if logs are sent over the network then ensure that they are sent over an SSL channel.
As pentester, try to take a look to these logs.
Analytics Data Sent To 3rd Parties
Most of the application uses other services in their application like Google Adsense but sometimes they leak some sensitive data or the data which is not required to sent to that service. This may happen because of the developer not implementing feature properly. You can look by intercepting the traffic of the application and see whether any sensitive data is sent to 3rd parties or not.
SQLite DBs
Most of the applications will use internal SQLite databases to save information. During the pentest take a look to the databases created, the names of tables and columns and all the data saved because you could find sensitive information (which would be a vulnerability).
Databases should be located in /data/data/the.package.name/databases like /data/data/com.mwr.example.sieve/databases
If the database is saving confidential information and is encrypted but you can find the password inside the application it's still a vulnerability.
Enumerate the tables using .tables and enumerate the columns of the tables doing .schema <table_name>
Drozer (Exploit Activities, Content Providers and Services)
Drozer allows you to assume the role of an Android app and interact with other apps. It can do anything that an installed application can do, such as make use of Android’s Inter-Process Communication (IPC) mechanism and interact with the underlying operating system. From Drozer Guide.
Drozer is s useful tool to exploit exported activities, exported services and Content Providers as you will learn in the following sections.
Exploiting exported Activities
Read this if you want to remind what is an Android Activity.
_**_Also remember that the code of an activity starts with the onCreate method.
Authorisation bypass
When an Activity is exported you can invoke its screen from an external app. Therefore, if an activity with sensitive information is exported you could bypass the authentication mechanisms to access it.
Learn how to exploit exported activities with Drozer.
You can also start an exported activity from adb:
- PackageName is com.example.demo
- Exported ActivityName is com.example.test.MainActivity
adb shell am start -n com.example.demo/com.example.test.MainActivity
NOTE: MobSF will detect as malicious the use of singleTask/singleInstance as android:launchMode in an activity, but due to this, apparently this is only dangerous on old versions (API versions < 21).
{% hint style="info" %} Note that an authorisation bypass is not always a vulnerability, it would depend on how the bypass works and which information is exposed. {% endhint %}
Sensitive information leakage
Activities can also return results. If you manage to find an exported and unprotected activity calling the setResult method and returning sensitive information, there is a sensitive information leakage.
Exploiting Content Providers - Accessing and manipulating sensitive information
Read this if you want to remind what is a Content Provider.
Content providers are basically used to share data. If an app has available content providers you may be able to extract sensitive data from them. It also interesting to test possible SQL injections and Path Traversals as they could be vulnerable.
Learn how to exploit Content Providers with Drozer.
Exploiting Services
Read this if you want to remind what is a Service.
_**_Remember that a the actions of a Service start in the method onStartCommand.
As service is basically something that can receive data, process it and returns (or not) a response. Then, if an application is exporting some services you should check the code to understand what is it doing and test it dynamically for extracting confidential info, bypassing authentication measures...
Learn how to exploit Services with Drozer.
Exploiting Broadcast Receivers
Read this if you want to remind what is a Broadcast Receiver.
Remember that a the actions of a Broadcast Receiver start in the method onReceive.
A broadcast receiver will be waiting for a type of message. Depending on ho the receiver handles the message it could be vulnerable.
Learn how to exploit Broadcast Receivers with Drozer.
Exploiting Schemes / Deep links
You can look for deep links manually, using tools like MobSF or scripts like this one.
You can open a declared scheme using adb or a browser:
adb shell am start -a android.intent.action.VIEW -d "scheme://hostname/path?param=value" [your.package.name]
Note that you can omit the package name and the mobile will automatically call the app that should open that link.
<!-- Browser regular link -->
<a href="scheme://hostname/path?param=value">Click me</a>
<!-- fallback in your url you could try the intent url -->
<a href="intent://hostname#Intent;scheme=scheme;package=your.package.name;S.browser_fallback_url=http%3A%2F%2Fwww.example.com;end">with alternative</a>
Code executed
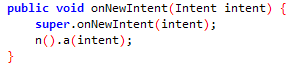
In order to find the code that will be executed in the App, go to the activity called by the deeplink and search the function onNewIntent.
Sensitive info
Every time you find a deep link check that it's not receiving sensitive data (like passwords) via URL parameters, because any other application could impersonate the deep link and steal that data!
Parameters in path
You must check also if any deep link is using a parameter inside the path of the URL like: https://api.example.com/v1/users/{username} , in that case you can force a path traversal accessing something like: example://app/users?username=../../unwanted-endpoint%3fparam=value .
Note that if you find the correct endpoints inside the application you may be able to cause a Open Redirect (if part of the path is used as domain name), account takeover (if you can modify users details without CSRF token and the vuln endpoint used the correct method) and any other vuln. More info about this here.
More examples
An interesting bug bounty report about links (/.well-known/assetlinks.json).
Insufficient Transport Layer Protection
- Lack of Certificate Inspection: Android Application fails to verify the identity of the certificate presented to it. Most of the application ignore the warnings and accept any self-signed certificate presented. Some Application instead pass the traffic through an HTTP connection.
- Weak Handshake Negotiation: Application and server perform an SSL/TLS handshake but use an insecure cipher suite which is vulnerable to MITM attacks. So any attacker can easily decrypt that connection.
- Privacy Information Leakage: Most of the times it happens that Applications do authentication through a secure channel but rest all connection through non-secure channel. That doesn’t add to security of application because rest sensitive data like session cookie or user data can be intercepted by an malicious user.
From the 3 scenarios presented we are going to discuss how to verify the identity of the certificate. The other 2 scenarios depends on the TLS configuration of the server and if the application sends unencrypted data. The pentester should check by it's own the TLS configuration of the server (here) and detect if any confidential information is sent by an unencrypted/vulnerable channel .
More information about how to discover and fix these kind of vulnerabilities here.
SSL Pinning
By default, when making an SSL connection, the client(android app) checks that the server’s certificate has a verifiable chain of trust back to a trusted (root) certificate and matches the requested hostname. This lead to problem of Man in the Middle Attacks(MITM).
In certificate Pinnning, an Android Application itself contains the certificate of server and only transmit data if the same certificate is presented.
It's recommended to apply SSL Pinning for the sites where sensitive information is going to be sent.
Inspecting HTTP traffic
First of all, you should (must) install the certificate of the proxy tool that you are going to use, probably Burp. If you don't install the CA certificate of the proxy tool, you probably aren't going to see the encrypted traffic in the proxy.
Please, read this guide to learn how to do install a custom CA certificate.
For applications targeting API Level 24+ it isn't enough to install the Burp CA certificate in the device. To bypass this new protection you need to modify the Network Security Config file. So, you could modify this file to authorise your CA certificate or you can read this page for a tutorial on how to force the application to accept again all the installed certificate sin the device.
SSL Pinning
We have already discuss what is SSL Pinning just 2 paragraphs before. When it's implemented in an application you will need to bypass it to inspect the HTTPS traffic or you won't see it.
Here I'm going to present a few options I've used to bypass this protection:
- Automatically modify the apk to bypass SSLPinning with apk-mitm. The best pro of this option, is that you won't need root to bypass the SSL Pinning, but you will need to delete the application and reinstall the new one, and this won't always work.
- You could use Frida (discussed below) to bypass this protection. Here you have a guide to use Burp+Frida+Genymotion: https://spenkk.github.io/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/
- You can also try to automatically bypass SSL Pinning using objection:
objection --gadget com.package.app explore --startup-command "android sslpinning disable" - You can also try to automatically bypass SSL Pinning using MobSF dynamic analysis (explained below)
- If you still think that there is some traffic that you aren't capturing you can try to forward the traffic to burp using iptables. Read this blog: https://infosecwriteups.com/bypass-ssl-pinning-with-ip-forwarding-iptables-568171b52b62
Common Web vulnerabilities
Note that in this step you should look for common web vulnerabilities. A lot of information about web vulnerabilities be found in this book so I'm not going to mention them here.
Frida
Dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers. Learn more at www.frida.re.
It's amazing, you can access running application and hook methods on run time to change the behaviour, change values, extract values, run different code...
If you want to pentest Android applications you need to know how to use Frida.
Learn how to use Frida: Frida tutorial
Some "GUI" for actions with Frida: https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security
Some other abstractions based on Frida: https://github.com/sensepost/objection , https://github.com/dpnishant/appmon
You can find some Awesome Frida scripts here: https://codeshare.frida.re/
Android Application Analyzer
This tool could help you managing different tools during the dynamic analysis: https://github.com/NotSoSecure/android_application_analyzer
Intent Injection
This vulnerability resembles Open Redirect in web security. Since class Intent is Parcelable, objects belonging to this class can be passed as extra data in another Intent object.
Many developers make use of this feature and create proxy components (activities, broadcast receivers and services) that take an embedded Intent and pass it to dangerous methods like startActivity(...), sendBroadcast(...), etc.
This is dangerous because an attacker can force the app to launch a non-exported component that cannot be launched directly from another app, or to grant the attacker access to its content providers. WebView also sometimes changes a URL from a string to an Intent object, using the Intent.parseUri(...) method, and passes it to startActivity(...).
Android Client Side Injections and others
Probably you know about this kind of vulnerabilities from the Web. You have to be specially careful with this vulnerabilities in an Android application:
- SQL Injection: When dealing with dynamic queries or Content-Providers ensure you are using parameterized queries.
- JavaScript Injection (XSS): Verify that JavaScript and Plugin support is disabled for any WebViews (disabled by default). More info here.
- Local File Inclusion: Verify that File System Access is disabled for any WebViews (enabled by default)
(webview.getSettings().setAllowFileAccess(false);). More info here. - Eternal cookies: In several cases when the android application finish the session the cookie isn't revoked or it could be even saved to disk
- Secure Flag in cookies
Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %} {% endhint %}
Automatic Analysis
MobSF
Static analysis
Vulnerability assessment of the application using a nice web-based frontend. You can also perform dynamic analysis (but you need to prepare the environment).
docker pull opensecurity/mobile-security-framework-mobsf
docker run -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
Notice that MobSF can analyse Android(apk), IOS(ipa) and Windows(apx) applications (Windows applications must be analyzed from a MobSF installed in a Windows host).
Also, if you create a ZIP file with the source code if an Android or an IOS app (go to the root folder of the application, select everything and create a ZIPfile), it will be able to analyse it also.
MobSF also allows you to diff/Compare analysis and to integrate VirusTotal (you will need to set your API key in MobSF/settings.py and enable it: VT_ENABLED = TRUE VT_API_KEY = <Your API key> VT_UPLOAD = TRUE). You can also set VT_UPLOAD to False, then the hash will be upload instead of the file.
Assisted Dynamic analysis with MobSF
MobSF can also be very helpful for dynamic analysis in Android, but in that case you will need to install MobSF and genymotion in your host (a VM or Docker won't work). Note: You need to start first a VM in genymotion and then MobSF.
The MobSF dynamic analyser can:
- Dump application data (URLs, logs, clipboard, screenshots made by you, screenshots made by "Exported Activity Tester", emails, SQLite databases, XML files, and other created files). All of this is done automatically except for the screenshots, you need to press when you want a screenshot or you need to press "Exported Activity Tester" to obtain screenshots of all the exported activities.
- Capture HTTPS traffic
- Use Frida to obtain runtime information
From android versions > 5, it will automatically start Frida and will set global proxy settings to capture traffic. It will only capture traffic from the tested application.
Frida
By default, it will also use some Frida Scripts to bypass SSL pinning, root detection and debugger detection and to monitor interesting APIs.
MobSF can also invoke exported activities, grab screenshots of them and save them for the report.
To start the dynamic testing press the green bottom: "Start Instrumentation". Press the "Frida Live Logs" to see the logs generated by the Frida scripts and "Live API Monitor" to see all the invocation to hooked methods, arguments passed and returned values (this will appear after pressing "Start Instrumentation").
MobSF also allows you to load your own **Frida scripts (**to send the results of your Friday scripts to MobSF use the function send()). It also has several pre-written scripts you can load (you can add more in MobSF/DynamicAnalyzer/tools/frida_scripts/others/), just select them, press "Load" and press "Start Instrumentation" (you will be able to see the logs of that scripts inside "Frida Live Logs").
Moreover, you have some Auxiliary Frida functionalities:
- Enumerate Loaded Classes: It will print all the loaded classes
- Capture Strings: It will print all the capture strings while using the application (super noisy)
- Capture String Comparisons: Could be very useful. It will show the 2 strings being compared and if the result was True or False.
- Enumerate Class Methods: Put the class name (like "java.io.File") and it will print all the methods of the class.
- Search Class Pattern: Search classes by pattern
- Trace Class Methods: Trace a whole class (see inputs and outputs of all methods of th class). Remember that by default MobSF traces several interesting Android Api methods.
Once you have selected the auxiliary module you want to use you need to press "Start Intrumentation" and you will see all the outputs in "Frida Live Logs".
Shell
Mobsf also brings you a shell with some adb commands, MobSF commands, and common shell commands at the bottom of the dynamic analysis page. Some interesting commands:
help
shell ls
activities
exported_activities
services
receivers
HTTP tools
When http traffic is capture you can see an ugly view of the captured traffic on "HTTP(S) Traffic" bottom or a nicer view in "Start HTTPTools" green bottom. From the second option, you can send the captured requests to proxies like Burp or Owasp ZAP.
To do so, power on Burp --> turn off Intercept --> in MobSB HTTPTools select the request --> press "Send to Fuzzer" --> select the proxy address (http://127.0.0.1:8080\).
Once you finish the dynamic analysis with MobSF you can press on "Start Web API Fuzzer" to fuzz http requests an look for vulnerabilities.
{% hint style="info" %} After performing a dynamic analysis with MobSF the proxy settings me be misconfigured and you won't be able to fix them from the GUI. You can fix the proxy settings by doing:
adb shell settings put global http_proxy :0
{% endhint %}
Assisted Dynamic Analysis with Inspeckage
You can get the tool from Inspeckage.
This tool with use some Hooks to let you know what is happening in the application while you perform a dynamic analysis.
{% content-ref url="inspeckage-tutorial.md" %} inspeckage-tutorial.md {% endcontent-ref %}
Yaazhini
This is a great tool to perform static analysis with a GUI
Qark
This tool is designed to look for several security related Android application vulnerabilities, either in source code or packaged APKs. The tool is also capable of creating a "Proof-of-Concept" deployable APK and ADB commands, to exploit some of the found vulnerabilities (Exposed activities, intents, tapjacking...). As with Drozer, there is no need to root the test device.
pip3 install --user qark # --user is only needed if not using a virtualenv
qark --apk path/to/my.apk
qark --java path/to/parent/java/folder
qark --java path/to/specific/java/file.java
ReverseAPK
- Displays all extracted files for easy reference
- Automatically decompile APK files to Java and Smali format
- Analyze AndroidManifest.xml for common vulnerabilities and behavior
- Static source code analysis for common vulnerabilities and behavior
- Device info
- Intents
- Command execution
- SQLite references
- Logging references
- Content providers
- Broadcast recievers
- Service references
- File references
- Crypto references
- Hardcoded secrets
- URL's
- Network connections
- SSL references
- WebView references
reverse-apk relative/path/to/APP.apk
SUPER Android Analyzer
SUPER is a command-line application that can be used in Windows, MacOS X and Linux, that analyzes .apk files in search for vulnerabilities. It does this by decompressing APKs and applying a series of rules to detect those vulnerabilities.
All rules are centered in a rules.json file, and each company or tester could create its own rules to analyze what they need.
Download the latest binaries from in the download page
super-analyzer {apk_file}
StaCoAn
StaCoAn is a crossplatform tool which aids developers, bugbounty hunters and ethical hackers performing static code analysis on mobile applications*.
The concept is that you drag and drop your mobile application file (an .apk or .ipa file) on the StaCoAn application and it will generate a visual and portable report for you. You can tweak the settings and wordlists to get a customized experience.
Download latest release:
./stacoan
AndroBugs
AndroBugs Framework is an Android vulnerability analysis system that helps developers or hackers find potential security vulnerabilities in Android applications.
Windows releases
python androbugs.py -f [APK file]
androbugs.exe -f [APK file]
Androwarn
Androwarn is a tool whose main aim is to detect and warn the user about potential malicious behaviours developped by an Android application.
The detection is performed with the static analysis of the application's Dalvik bytecode, represented as Smali, with the androguard library.
This tool looks for common behavior of "bad" applications like: Telephony identifiers exfiltration, Audio/video flow interception, PIM data modification, Arbitrary code execution...
python androwarn.py -i my_application_to_be_analyzed.apk -r html -v 3
MARA Framework
MARA is a Mobile Application Reverse engineering and Analysis Framework. It is a tool that puts together commonly used mobile application reverse engineering and analysis tools, to assist in testing mobile applications against the OWASP mobile security threats. Its objective is to make this task easier and friendlier to mobile application developers and security professionals.
It is able to:
- Extract Java and Smali code using different tools
- Analyze APKs using: smalisca, ClassyShark, androbugs, androwarn, APKiD
- Extract private information from the APK using regexps.
- Analyze the Manifest.
- Analyze found domains using: pyssltest, testssl and whatweb
- Deobfuscate APK via apk-deguard.com
Koodous
Useful to detect malware: https://koodous.com/
Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %} {% endhint %}
Obfuscating/Deobfuscating code
Note that depending the service and configuration you use to obfuscate the code. Secrets may or may not ended obfuscated.
ProGuard
ProGuard is an open source command-line tool that shrinks, optimizes and obfuscates Java code. It is able to optimize bytecode as well as detect and remove unused instructions. ProGuard is free software and is distributed under the GNU General Public License, version 2.
ProGuard is distributed as part of the Android SDK and runs when building the application in release mode.
From: https://en.wikipedia.org/wiki/ProGuard_(software)
DexGuard
Find a step-by-step guide to deobfuscate the apk in https://blog.lexfo.fr/dexguard.html
(From that guide) Last time we checked, the Dexguard mode of operation was:
- load a resource as an InputStream;
- feed the result to a class inheriting from FilterInputStream to decrypt it;
- do some useless obfuscation to waste a few minutes of time from a reverser;
- feed the decrypted result to a ZipInputStream to get a DEX file;
- finally load the resulting DEX as a Resource using the
loadDexmethod.
DeGuard
DeGuard reverses the process of obfuscation performed by Android obfuscation tools. This enables numerous security analyses, including code inspection and predicting libraries.
You can upload an obfuscated APK to their platform.
Simplify
It is a generic android deobfuscator. Simplify virtually executes an app to understand its behavior and then tries to optimize the code so it behaves identically but is easier for a human to understand. Each optimization type is simple and generic, so it doesn't matter what the specific type of obfuscation is used.
APKiD
APKiD gives you information about how an APK was made. It identifies many compilers, packers, obfuscators, and other weird stuff. It's PEiD for Android.
Manual
Read this tutorial to learn some tricks on how to reverse custom obfuscation
Labs
Androl4b
AndroL4b is an Android security virtual machine based on ubuntu-mate includes the collection of latest framework, tutorials and labs from different security geeks and researchers for reverse engineering and malware analysis.
OWASP
{% embed url="https://github.com/OWASP/owasp-mstg%0Ahttps://mobile-security.gitbook.io/mobile-security-testing-guide/ios-testing-guide/0x06g-testing-network-communication" %}
Git Repos
https://github.com/riddhi-shree/nullCommunity/tree/master/Android
https://www.youtube.com/watch?v=PMKnPaGWxtg&feature=youtu.be&ab_channel=B3nacSec
References
For more information visit:
- https://appsecwiki.com/#/ It is a great list of resources
- https://maddiestone.github.io/AndroidAppRE/ Android quick course
- https://manifestsecurity.com/android-application-security/
- https://github.com/Ralireza/Android-Security-Teryaagh
To Test
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.
Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %} {% endhint %}