1.9 KiB
APK decompilers
JD-Gui
First famous gui Java decompiler, you could use it to investigate the Java code from the APK once you have obtained it.
Jadx
Buildin Java (multi-platform)and at this moment I think it's the recommended one.
Just download the latest version and execute it from the bin folder:
jadx-gui
Using the GUI you can perform text search, go to the functions definitions _CTRL + left click_ on the function and cross refs _right click_ --> _Find Usage_
If you only want the java code but without using a GUI a very easy way is to use the jadx cli tool:
jadx app.apk
Some interesting options of jadx GUI and CLI versions are:
-d <path to output dir>
--no-res #No resources
--no-src #No source code
--no-imports #Always write entire package name (very useful to know where is the function that you might want to hook)
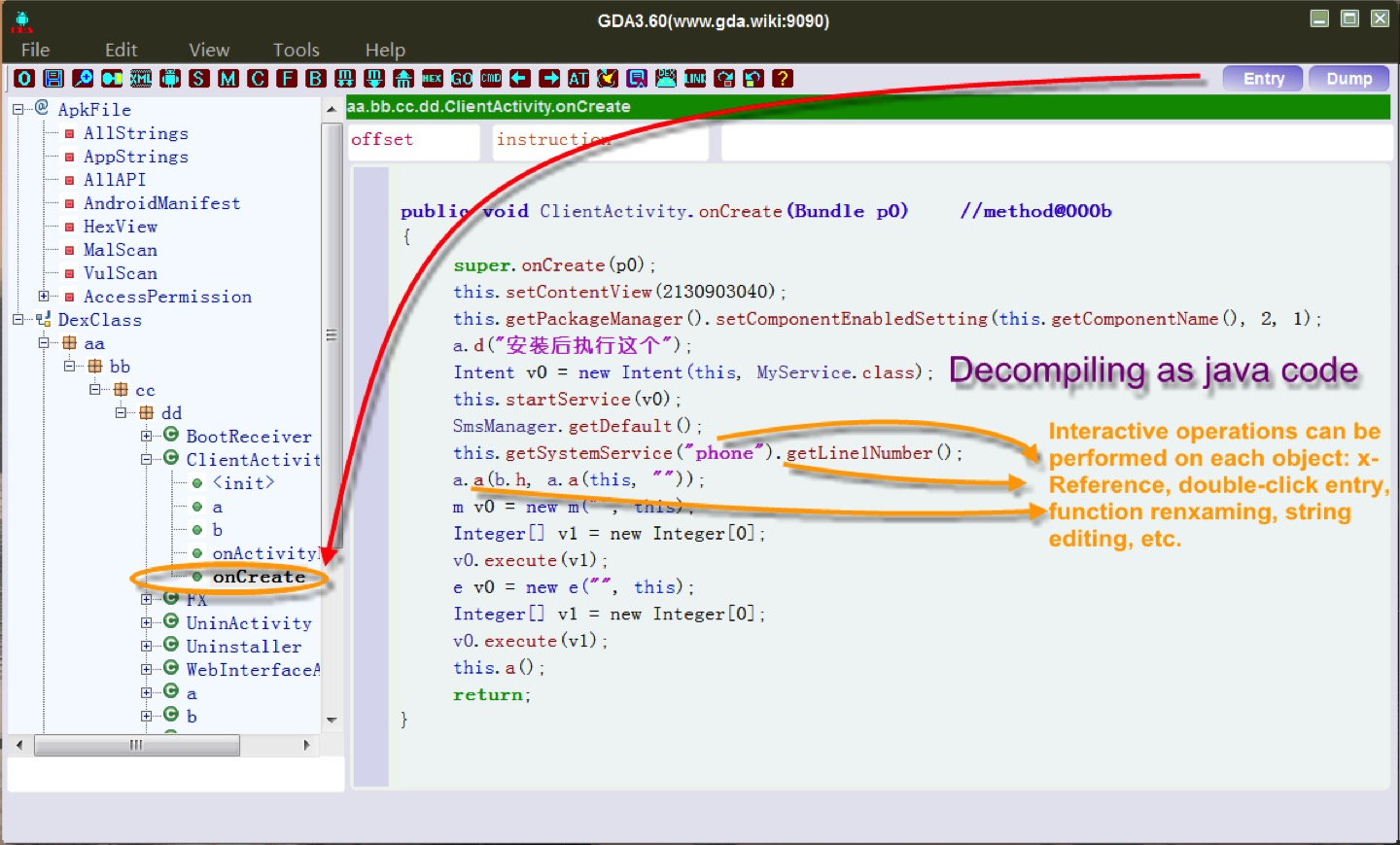
GDA-android-reversing-Tool
Looks faster than JD-Gui, It probides more information MalScan, Strings... and same interesting capabilities: X-refs, go to functions definitions...
But it's only available for Windows.
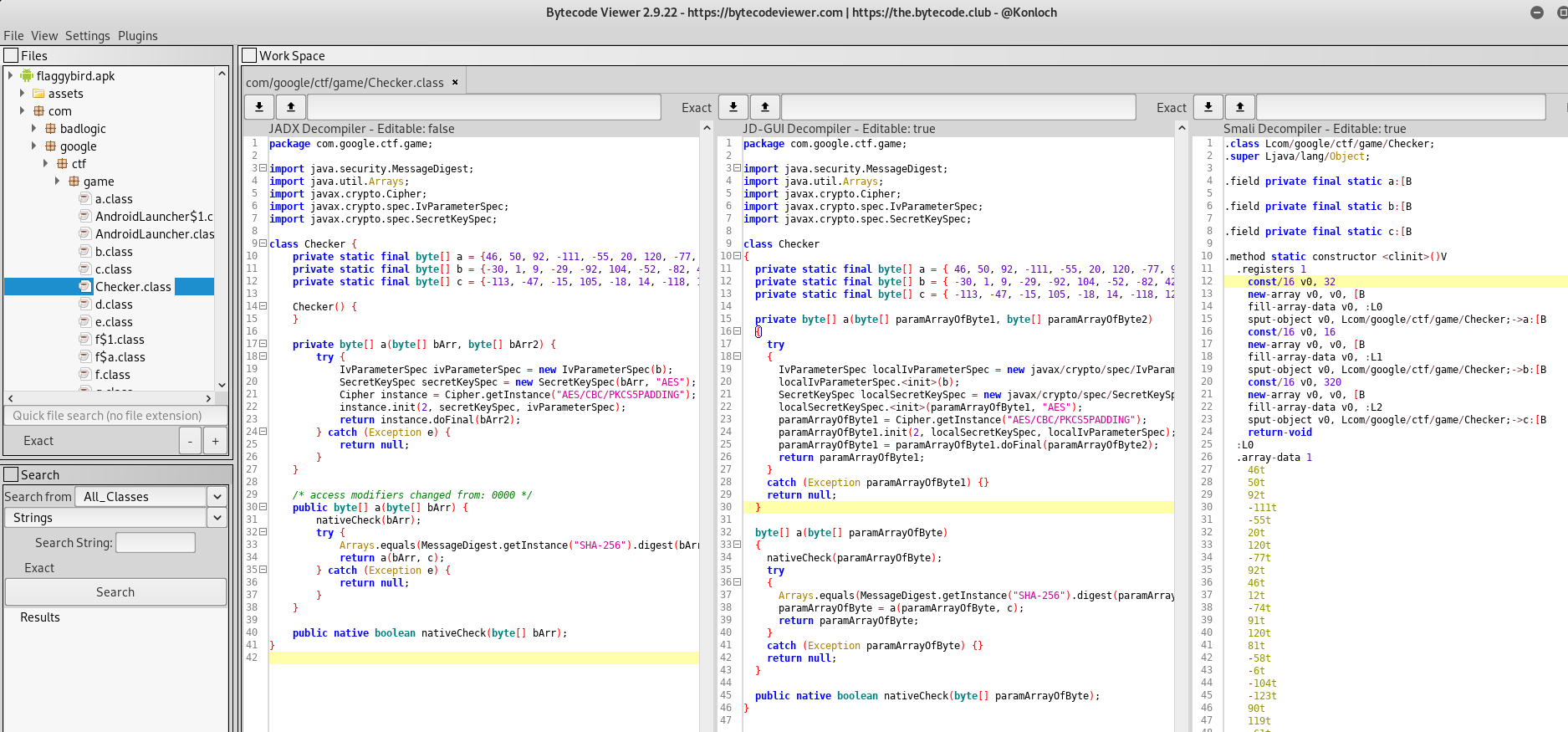
Bytecode-Viewer
Another interesting tool to make a Static analysis is: bytecode-viewer. It allows you to decompile the APK using several decompilers at the same time. Then, you can see for example, 2 different Java decompilers and one Smali decompiler. It allows you also to modify the code:
If you modify the code, then you can export it.
One bad thing of bytecode-viewer is that it doesn't have references or cross-references.