6.6 KiB
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.
Google CTF 2018 - Shall We Play a Game?
Download the APK here:
I am going to upload the APK to https://appetize.io/ (free account) to see how the apk is behaving:
Looks like you need to win 1000000 times to get the flag.
Following the steps from pentesting Android you can decompile the application to get the smali code and read the Java code using jadx.
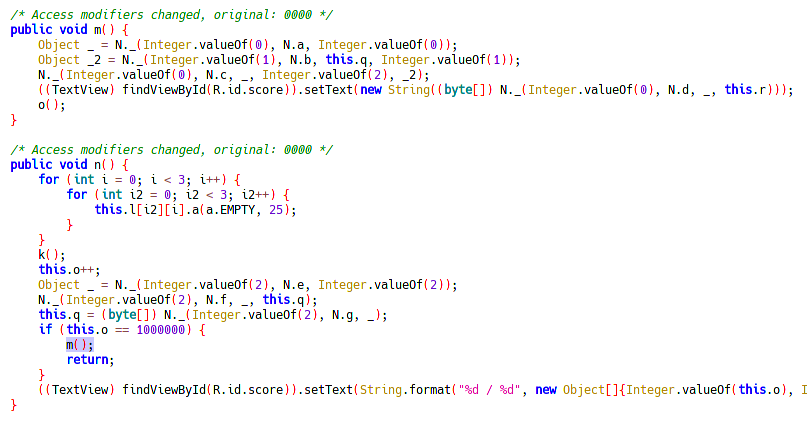
Reading the java code:
It looks like the function that is going print the flag is m().
Smali changes
Call m() the first time
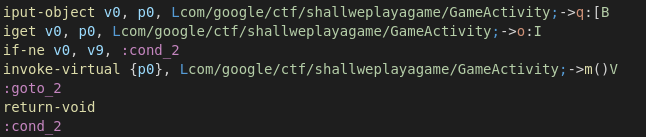
Lets make the application call m() if the variable this.o != 1000000 to do so, just cange the condition:
if-ne v0, v9, :cond_2
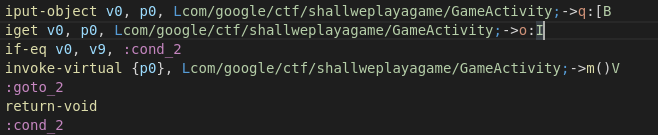
to:
if-eq v0, v9, :cond_2
Follow the steps of pentest Android to recompile and sign the APK. Then, upload it to https://appetize.io/ and lets see what happens:
Looks like the flag is written without being completely decrypted. Probably the m() function should be called 1000000 times.
Other way to do this is to not change the instrucction but change the compared instructions:
Another way is instead of comparing with 1000000, set the value to 1 so this.o is compared with 1:
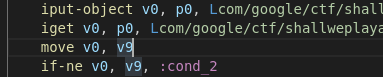
A forth way is to add an instruction to move to value of v9(1000000) to v0 (this.o):
Solution
Make the application run the loop 100000 times when you win the first time. To do so, you only need to create the :goto_6 loop and make the application junp there if this.o does not value 100000:
You need to do this inside a physical device as (I don't know why) this doesn't work in an emulated device.
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.